Enabling MAC-based access control on an SSID
MAC-based access control admits or denies wireless association based on the connecting device’s MAC address. In this authentication method wireless devices use their MAC address as the username and password. Follow the steps below to configure an SSID to require MAC-based access control with RADIUS.
Note: To enable MAC-based access control without a RADIUS server, a Sign-on Splash page can be used in a similar fashion.
1. From Dashboard navigate to Wireless > Configure > Access control.
2. Select MAC-based access control (no encryption) for Security.
3. For Splash page choose None (direct access). Click-through can be selected if desired.
Select Cisco Identity Services Engine (ISE) Authentication if your setup uses the AVP Service Type - Call Check, otherwise the access points won't include it in their access-request packets.
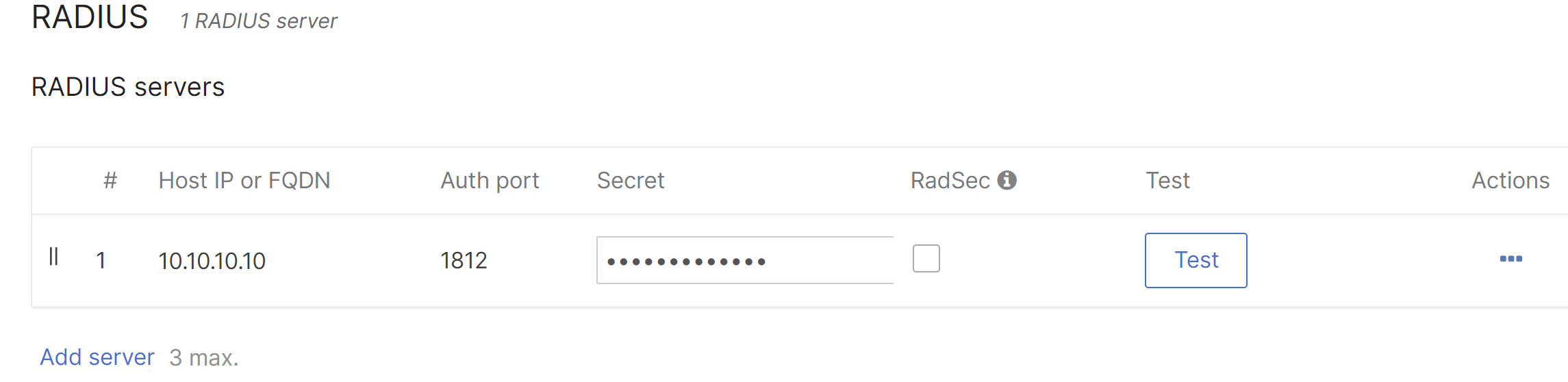
4. For RADIUS servers, click Add server. Enter the RADIUS server IP address, listening port, and RADIUS shared secret to be used by your access points which are configured RADIUS clients on the server.
5. For Client IP and VLAN, choose External DHCP server assigned in a VLAN environment. Meraki AP assigned (NAT mode) could be used without VLANs if desired.
6. An SSID can bridge wireless devices onto different VLANs. A default SSID VLAN can be set using the VLAN tag drop down. Then by setting the RADIUS override it can override VLAN tag from VLAN override drop down. RADIUS accept messages containing a different VLAN tag will be able to override the default VLAN for the SSID.
7. Click Save.
MAB authentication fallback to Guest VLAN
This feature allows the use of a guest vlan for customers that do not complete authentication or when the RADIUS server is unreachable. A configuration where authenticated devices are desired to be on a designated VLAN and everything else, using the same SSID, would be placed in a Guest VLAN.
This configuration can be used with VLAN tagging or without it, meaning the authorized clients can be put in the designated VLAN by VLAN tagging option, or can use the untagged VLAN the access point is using (default behavior without using vlan tagging).
This feature is introduced from MR 27.2 and on
In order to configure this feature, a new option can be found on Wireless > Configure > Access Control when MAC-based access control (no encryption) is selected. You will see the following option, where it can be enabled:
Once enabled, the option to fill the Guest VLAN ID will be displayed where the VLAN ID can be input.
For example:
In an SSID using MAC authentication with a VLAN tagging of 10, using RADIUS Guest VLAN with a Guest VLAN of 1.
When a client completes the authentication, meaning the RADIUS server is reachable and it received "Access-Accept" as a result of the authorization process.

The client will be put into VLAN 10.
However, if the client is rejected or the RADIUS server is unreachable:

Then the client will be put into VLAN 1, which is designated as the Guest VLAN.

