Air Marshal
Click 日本語 for Japanese
Learn more with these free online training courses on the Meraki Learning Hub:
Wireless Security Threats in an Enterprise Environment
Secure WiFi access has become a critical component of enterprise networking. WiFi Internet access is critical for corporate communication in verticals, including financial services, retail, and distributed enterprises. Due to the widespread use of WiFi and a variety of use cases (e.g., point-of-sale (POS) communications, corporate access, warehouse inventory, asset tracking, and WiFi services for targeted advertising), the wealth of information transmitted across the wireless medium has skyrocketed. Data transmitted over wireless increasingly contains sensitive personal and financial data. Unfortunately, the tremendous growth in wireless has been accompanied by an increasingly widespread ability to obtain open-source hacking tools that can compromise a wireless network through the impersonation of client devices and access points (APs).
Examples of Common Threats in a Modern WiFi Environment
Network impersonation: achievable by purchasing any consumer-grade access point and copying an SSID, “tricking” clients into thinking that this SSID is available and snooping on their information transactions.

Wired network compromise: achieved by an unsuspecting employee or student plugging in a consumer-grade access point into the wired infrastructure and exposing the LAN to hackers.

To successfully protect an enterprise network, a Wireless Intrusion Prevention System (WIPS) should provide powerful wireless intrusion scanning capabilities, enabling detection and classification of different types of wireless threats, including rogue access points and wireless hackers. Additionally, a WIPS system should be configurable with intuitive auto-containment policies to facilitate preemptive action against rogue devices. Once a threat has been detected, the WIPS platform should kick into gear to enact powerful policies, including intelligent auto-disablement of APs matching a pre-defined criteria and generating different tiers of e-mail alarms based on the type of threat in your airspace.
Cisco Meraki’s Air Marshal mode allows network administrators to meet these requirements and design an airtight network architecture that provides an industry-leading WIPS platform in order to completely protect the airspace from wireless attacks. The remainder of this document describes in greater depth wireless threats and the necessary security measures required to remediate against these threats; the conclusion then summarizes the setup and configuration process for Meraki’s Air Marshal WIPS platform in order to achieve the highest security protection possible.
Wireless Threats
Understanding the wireless airspace around you can help to take effective measures, both preventive and reactive, to ensure that the wireless airspace is secure and interference-free from other wireless networks. Several different threats exist in the modern enterprise environment, facilitated by easy access to cheap consumer-grade 802.11 equipment, along with open-source hacking tools that can be used to simulate and spoof devices and generate traffic floods. Leading enterprise WLAN providers such as Cisco provide built-in WIPS features to ensure detection and remediation against these threats.
Threat Classifications
Visibility and classification of potential wireless threats is an important first step in securing the wireless network and network infrastructure as a whole. Once classified, remediation can be taken against confirmed threats and innocuous alerts can be dismissed. Cisco Meraki Air Marshal automatically classifies threats into the following categories to provide the greatest visibility and overall protection for your network.
Rogue SSIDs
Rogue SSID seen on LAN: SSIDs that are broadcast by rogue access points and seen on wired LAN; this could suggest a compromise of the wired network.
Note: On MRs with a scanning radio, Air Marshal will not contain Rogue and Other SSIDs seen by the scanning radio if those SSIDs are on a DFS channel. This is because regulations require that significant time be spent determining that such channels are clear before transmitting on them, and this amount of time is great enough that it would render MRs unable effectively to scan the spectrum. As a result, only SSIDs on non-DFS channels can be contained by the scanning radio.
However, if the client-serving radio of the MR is operating on a DFS channel that matches that of the Rogue or Other SSIDs, Air Marshal will contain those SSIDs on that DFS channel if configured to do so.
Note: Air Marshal may flag legitimate Wi-Fi Direct SSIDs since Wi-Fi Direct allows simultaneous peer-to-peer and infrastructure WLAN connections.
Other SSIDs
Interfering SSIDs: wireless networks that are broadcasting and could be causing RF interference, as well as attracting accidental associations from clients who are supposed to be connecting to your own network.
Ad-Hoc SSIDs: modern smartphones and mobile devices are capable of associating to WiFi networks and then re-broadcasting the SSID, essentially acting as a wireless bridge. Devices in ad-hoc mode can connect to a client AP and create a gateway for wireless hackers.
Spoofs
Spoofs are APs that are impersonating the SSID (and possibly MAC address) of your APs. An AP spoof means that someone is deliberately impersonating your network and should be treated with the highest level of severity.
Malicious Broadcasts
Denial of Service (DoS) attacks are attempts to prevent clients from associating to the legitimate AP by sending an excessive number of broadcast messages to clients. DoS attacks could be from malicious clients, APs, or even another WIPS system in the area that considers the corporate network a threat and is attempting to remediate.
Packet Floods
Clients or APs that are sending an excessive number of packets to your AP. Packets are monitored and classified based on multiple categories including beacon, authentication and association frames. An excessive number of any category of packets seen within a short time interval will be marked in Air Marshal as a packet flood.
Containment
Cisco Meraki access points feature powerful Air Marshal technology that can assist with mitigating wireless threats to your network. Access points feature the ability to contain rogue access points that can put your network at risk. This Knowledge Base article covers the following:
-
Overview of Air Marshal containment
-
Configuring containment
-
Types of containment
Overview of Air Marshal Containment
Rogue access points can be contained once they have been identified. When a rogue access point is contained, clients will be unable to connect to the rogue access points. Additionally, any currently associated clients will lose their connection to the rogue access point.
Note: 6 GHz containment will not work because 6 GHz uses protected management frame and it would not be possible to contain the clients over the air.
A Cisco Meraki AP accomplishes containment by sending deauthentication packets with the spoofed MAC address of the rogue access point (the BSSID of the rogue wireless network). The deauthentication packets force any clients that are connected to the rogue access point to disconnect. If a client attempts to connect to the rogue network, they will be immediately forced off by the Air Marshal. The image below shows a Cisco Meraki AP performing containment on a rogue SSID.
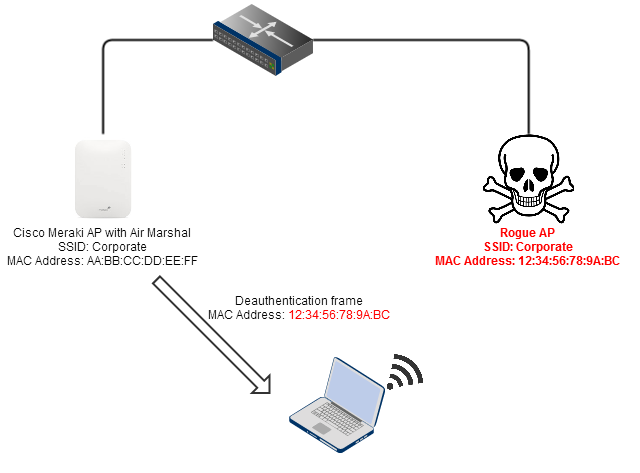
Air Marshal containment operations
Rogue AP Detection Outside Regulatory Domain
Hardware
This enhancement applies to all Wi-Fi 6 or above APs that are running MR31.x, except for MR28 and MR78.
Overview
Before the release of MR31.1, access points could only monitor for unauthorized APs within their designated regulatory domains. This posed a concern for large enterprise networks with numerous branch locations worldwide. For example, in Spain, APs do not support UNII-3 channels. A malicious actor may set up a Rogue AP on one of those UNII-3 channels and get users to connect to the SSID to steal credentials.
With the release of MR31.1, Air Marshal’s Rogue Detection support has been expanded beyond the AP’s regulatory domain.
Configuration
This feature is disabled by default. Please contact Meraki support to have this enabled on your network.
Note: This is for Detection Alert and Non-Containment capabilities only.
The enhancement is strictly limited to scanning out-of-regulatory domain channels for detection and alert purposes, containment of rogue APs is only done in regulatory domain channels.
Configuring Meraki’s Air Marshal WIDS/WIPS platform
Dual-radio Meraki APs will run wireless scans opportunistically while also serving clients; this means they will scan the channel on which they are serving clients. It is possible to schedule ‘mandatory’ scans to be run at pre-specified time intervals that can be set as frequently as once a day. Dual-radio APs can be set into a dedicated Air Marshal mode where it will not serve clients but will scan using both the 2.4GHz and 5GHz frequencies. Many Meraki access points include a third radio which comes pre-configured for permanent Air Marshal scanning. These APs do not require any dedicated Air Marshal configuration and will scan and remediate against threats in real-time.
For dual-radio Meraki access points: Air Marshal mode can be switched on by selecting the relevant APs on the Access Points page. By clicking the relevant AP and selecting ‘On’ under the Air Marshal scanning section or by applying the 'AirMarshal' tag to the AP, it is possible to designate this AP as a dedicated WIPS scanner. This Air Marshal AP will no longer serve clients but will now be a dedicated sensor performing scans of the surrounding environments for threats, the results of which will be displayed on the WIPS page in real-time.
A note on hybrid vs. dedicated scanners: APs with two radios running in client-serving mode will only scan the airspace opportunistically; this means they will scan the client-serving channel in real-time, and will scan across all channels either once a day or when no clients are being served. Most WLAN vendors recommend having dedicated scanning sensors (with no clients being served) in security conscious environments, to ensure real-time security alerting and protection. Some vendors offer ‘time slicing’ which allows cross-channel scans while serving clients, but this sacrifices performance of latency-sensitive applications such as VoIP and is generally not recommended in the industry. For this reason, Meraki recommends utilizing APs with dedicated scanning radios for high performance, real-time scanning.

Air Marshal configuration page
Default LAN Containment
Administrators may specify whether or not they wish for clients to be able to connect to rogue SSIDs. By choosing to allow devices to connect to rogue SSIDs by default, users will be able to freely connect to non-authorized access points seen on the LAN and broadcasting an SSID. In some environments, this provides the necessary level of flexibility for proper workplace operations. Administrators can use the SSID block list rules to enforce more granular security policies.
If an administrator selects block clients from connecting to rogue SSIDs by default, then devices will be automatically contained when attempting to connect to an SSID being broadcast by non-Meraki AP seen on the wired LAN. This provides greatest level of security for the wireless network.

Configuring automatic containment of rogue SSIDs
SSID Block List
If clients are allowed to connect to rogue SSIDs by default, then administrators may specify additional rules to block list (contain) certain SSIDs or BSSIDs. These policies may match on exact words, MAC address (BSSID), keywords or wildcards, as shown in the image below. Email and syslog alerts will also be generated if SSIDs matching the rules in the block list table are seen.
Warning: Care should be taken when configuring SSID block list policies as these policies will apply to SSIDs seen on the LAN as well as off of the LAN from neighboring WiFi deployments. Containment can have legal implications when launched against neighbor networks, and it may harm your own network by increasing channel utilization and potential disrupt clients connecting to your APs. Ensure that the rogue device is within your network and poses a security risk before you launch the containment.
Review the above mentioned section Overview of Air Marshal Containment to understand how the APs may block the configured SSIDs.

Figure A: SSID block list policy enforcement
The following are acceptable wildcard characters that can be used to match on for the SSID block list, SSID allow list and SSID alerting tables:
* - Any number of characters
? - Any single character
SSID Allow List
Similarly, if administrators wish to block clients from connecting to rogue SSIDs via containment by default, then administrators may use Air Marshal rules to allow list certain SSIDs or BSSIDs that clients will be allowed to connect to. Rogue or Other SSIDs that match these rules will not generate alerts.

Figure B: SSID allow list policy enforcement
SSID Alerting
Lastly, administrators may configure rules to alert when SSIDs matching a rule are seen. Alerts will be sent via email (as specified on the Network-wide > Configure > Alerts page) and via Syslog (as specified on the Network-wide > Configure > General page).

Figure C: SSID alert policy
When a SSID/BSSID configured within SSID alerting is detected, and there is a syslog server configured, the syslog messages uses the event type of device_alerting.
"airmarshal_events type=device_alerting"
Manually Applying Security Policies
When a rogue SSID or other SSID has been identified by an AP, it can have a security policy manually applied to it. Follow the steps below to manually apply a security policy to an SSID.
-
Navigate to Wireless > Monitor > Air Marshal .
-
Locate the SSID that you wish to apply a policy to under the Rogue SSIDs or Other SSIDs tab.
-
Select the check-box to the left of the SSID(s), as shown in Figure E.
-
Select edit and specify if you'd like to allow list, contain, alert, or uncontain, as shown in Figure F.
-
Specify if the policy should be applied by SSID or BSSID. Selecting SSID will add an 'Exactly Matches' policy entry to the respective SSID block list, allow list or alert table on the Configure tab. Selecting BSSID will ad a 'Matches MAC Address' policy entry to the respective SSID block list, allow list or alert table.

Figure D. Select the check-box to the left of the SSID

Figure E. Specify to allow list, Contain, Alert or Uncontain the selected SSID(s)
APs across different networks within the same Dashboard Organization will not be flagged as rogues or interfering unless containment is activated. You can restrict them by containing the SSID through precise matches, MAC addresses, keywords, or wildcard rules. Additionally, APs are automatically restricted when the option "Block clients from connecting to rogue SSIDs by default" is activated.
For instance, consider "Network A" and "Network B" within the same Dashboard Organization. If the APs in Network A contain the APs from Network B, the Dashboard for Network A will display an entry under Wireless > Air Marshall > Rogue SSIDs for the contained SSIDs belonging to Network B.
Containment Types and Status
Uncontained
This is a rogue or other wireless network that is not currently contained. Upon evaluating the threat, you may wish to either block list or allow list the SSID. An uncontained SSID that has not been allow listed could eventually become contained if its status on the LAN were reclassified as being a rogue SSID if LAN containment is enabled, or if a block list rule is added that matches with the SSID or BSSID. An uncontained SSID has simply been noticed and no administrative decision has been made regarding its status yet.
Contained
This is a rogue wireless network that your Cisco Meraki AP is currently containing. Whenever a client attempts to connect to the rogue wireless network, they will be forced off via the deauthentication process described earlier.
Partially contained
This is a rogue wireless network that can not be completely contained because some of the rogue access points may be on a different channel. This can occur when a non-Air Marshal AP notices the rogue on a different channel during a channel scan. The AP can not fully contain the rogue wireless network because of the channel difference. Deploying more APs with dedicated third Air Marshal scanning radios can help mitigate these issues.
Allow Listed
This is a wireless network that has been allow listed either via a rule in the SSID allow list table or manually and will not be contained under any circumstances. You may choose to allow list a wireless network when you have identified it as being a legitimate part of your infrastructure. Allow listed networks will not be contained in any way.
Uncontained Other
This is a wireless network that was noticed during a scan, but has not been determined to be a threat to your network.
Rogue SSIDs
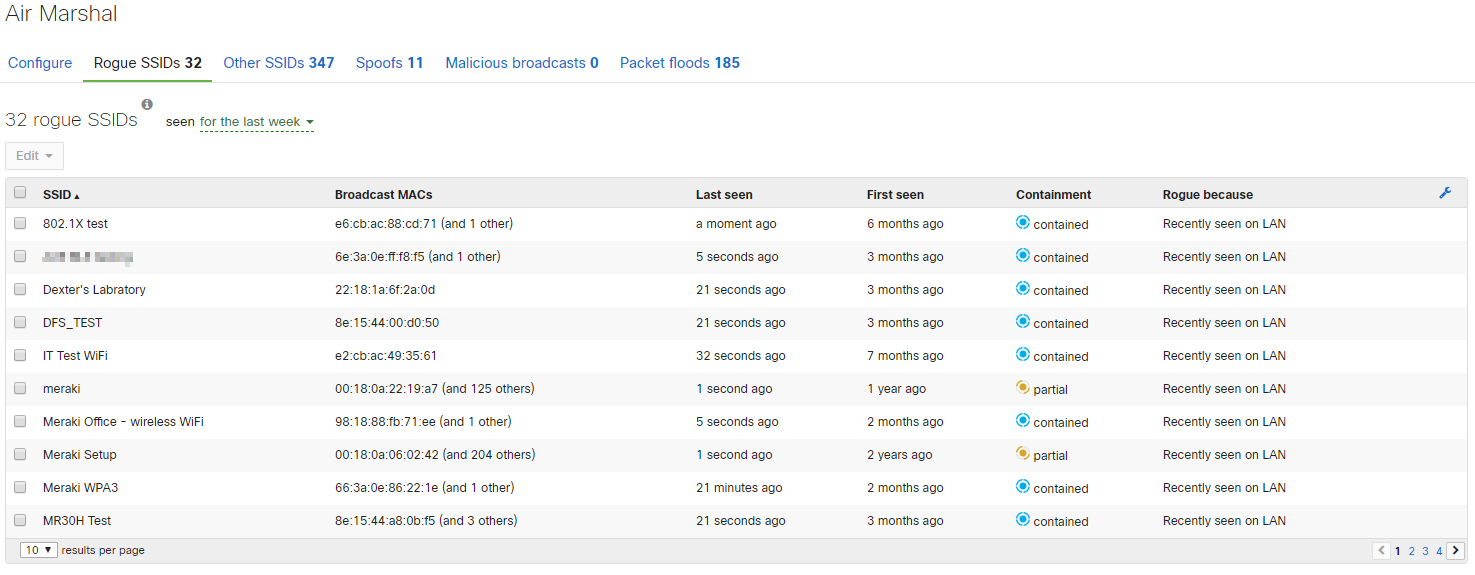
When a Beacon Frame for an SSID is detected by an access point in Air Marshal mode or with a dedicated scanning radio, it is classified as either a 'Rogue SSID' or as an 'Other SSID'. To determine if an SSID is originating locally, we look at the MAC address of local devices, and the BSSID of the broadcasted SSID. When a wireless access point of any brand generates a beacon packet, it uses a BSSID, which is virtual physical address. More information on this behavior can be found here.
Note: A “hidden SSID” on the Air Marshal page is an SSID name that is not included in the beacons and probe responses for a particular BSSID. These can usually be ignored during common network operation, and are unlikely to result in noticeable RF interference. Administrators may specify the same allow list, contain, alert, uncontain rules for BSSIDs contributing to the hidden SSID's seen by selecting the Hidden row and selecting the Broadcast MAC to apply the rule to.
Additional information about a specific rogue SSID can be found by selecting the row of the rogue SSID in question. RSSI of the rogue SSID will be displayed on a map or floorplan indicating which AP's are able to 'hear' the rogue SSID with the strongest signal, along with information pertaining to when the SSID was seen, on which channels, the broadcast MAC (BSSID), the manufacturer and the reason the SSID was identified as rogue.

When we detect an SSID being broadcast, we compare it to other known MAC addresses on the LAN. The criteria for a match are as follows:
- If a wired MAC and the broadcasted BSSID MAC match on the 3rd and 4th bytes of the MAC (starting with the 0th byte on the left, ending on the 5th byte on the right)
- AND if the rest of the bytes differ by 5 bits or less (except for the 4 least significant [rightmost] bits of the 5th byte, which are masked out), it is classified as a Rogue SSID.
This comparison is done with an Xor of the MAC address in binary notation. Below is an example of a wired MAC compared to the Broadcasted MAC in the SSID. This example was detected by Air Marshal:

When the MAC addresses are written out in binary, you can see that very few of the bits are different. When performing an Xor, you see that only 3 significant bits in the calculation are different between the two MAC addresses.

Note: Any BSSIDs that are seen broadcasting with a particular SSID will be associated together. Air Marshal containment focuses primarily on SSIDs. So if a single BSSID matches the checks listed above, the rest associated with that SSID will be flagged as well. This can be seen in the following example, where not all BSSIDs satisfy the requirements to match with the SSID.

Air Marshal will detect rogues on all VLANs if the Meraki AP is connected to a upstream trunk port given that all VLANs are allowed.
With the ability to locate Rogue SSIDs, administrators are better equipped to prevent unauthorized access points from operating on their local network. After detection, an administrator is able to take action, either containing the SSID using Air Marshal, or using the gathered information to find the offending device and remove it from the network.
Threat Remediation using Air Marshal
A careful study of the common wireless security threats has led to the development of Meraki’s Air Marshal platform, which allows access points to act as WIPS sensors on a dedicated radio while serving clients. Air Marshal is a WIPS platform which comes equipped with security alerting and threat remediation mechanisms. This includes the following:
Monitoring and alerting
A robust and intuitive display of all of the threats for a particular network, including auto-alerting based on the network administrator’s preferences.
Rogue Access point monitoring
802.11ac Meraki APs utilize a dedicated scanning radio to scan across all 2.4 GHz and 5 GHz channels and build a list of rogue access points in the nearby vicinity. In addition, further mechanisms are in place to track APs on the wired LAN network by inspecting traffic on the wired port of the Meraki AP, and using this to build a list of rogue access points that may be on the wired LAN. E-mail alerts as as well as syslog messages will be triggered for any SSID's that match rules configured on the SSID block list table or SSID alerts table.
Email alerting can be configured by navigating to the Network-wide > Configure > Alerts page and specifying that email alerts should be sent when a rogue access point is detected.

Syslog alerting can be configured by navigating to the Network-wide > Configure > General page and configuring the syslog server IP, port, and specifying 'air marshal' events.

Lastly, scan results can be retrieved via the Dashboard API using the GET call get-network-wireless-air-marshal.
Remediation mechanisms
Air Marshal access points come equipped with the ability to automatically ‘contain’ rogue access points and alert on rogue access points either by default or by configuring Air Marshal rules. This allows for administrators to take physical action to remove rogue access points.
What is containment?
‘Containment’ is a common mechanism that calls for the Air Marshal AP to impersonate or spoof the rogue access points in order to render it ineffective. Air Marshal does this by generating a large number of 802.11 packets and using the BSSID of the rogue access points as the the source MAC address. Air Marshal APs also provides more sophisticated containment methods including spoofing clients attempting to associate to the rogue by generating packets with the source MAC of the clients; this allows for a ‘two-way’ spoof and ensures a fool-proof shutdown of the rogue access points.
Packet types generated by WIPS during containment:
- 802.11 Broadcast deauthorizations with source = Rogue access point, destination = broadcast
- 802.11 Deauthorization messages with source = Rogue access point, destination MAC = client
- 802.11 Deauthorization and disassociate messages with source = client, destination = Rogue access point
#3 ensures that more sophisticated 802.11 clients with battery-saving capabilities are also unable to connect to the rogue, as they may ignore deauthorization messages from the Rogue access point if they are ‘sleeping’ in order to save battery life.


PCI Compliance
Understanding and remediating against wireless threats is also a requirement under the Payment Card Industry Data Security Standard (PCI DSS), a standard required for retailers to follow when processing credit card data over WLAN networks. Examples of WIPS requirements under PCI DSS include:
Section 9.1.3 Physical Security:
Restrict physical access to known wireless devices.
Section 10.5.4 Wireless Logs:
Archive wireless access centrally using a WIPS for 1 year.
Section 11.1 Quarterly Wireless Scan:
Scan all sites with card dataholder environments (CDE) whether or not they have known WLAN APs in the CDE. Sampling of sites is not allowed. A WIPS is recommended for large organizations since it is not possible to manually scan or conduct a walk-around wireless security audit of all sites on a quarterly basis
Section 11.4 Monitor Alerts:
Enable automatic WIPS alerts to instantly notify personnel of rogue devices and unauthorized wireless connections into the CDE.
Section 12.9 Eliminate Threats:
Prepare an incident response plan to monitor and respond to alerts from the WIPS. Enable automatic containment mechanism on WIPS to block rogues and unauthorized wireless connections.
Creating a WIPS response plan
By configuring alerts and utilizing Meraki’s Air Marshal view to monitor these threats retroactively and in real-time, it is possible to build a robust security plan that can be enforced. An example of a complete security methodology is as follows:
- Create a WIPS plan as per your company’s security policies
- Configure mandatory scanning intervals or designate APs to run in Air Marshal mode
- Configure auto-containment policies for rogue SSIDs
- Configure WIPS alerts
- Proactive monitoring of Air Marshal
- Visit Air Marshal page weekly or quarterly and mark known rogues as ‘allow listed’, contain dangerous rogues.
- Keep SSID block list, allow list, alert rules up-to-date.
- Consume the Air Marshal scan results via the API for data warehousing and auditing records.
- Contain rogues that may be a threat
- Reactive monitoring of Air Marshal alerts
- Receive alerts and react accordingly (set containment, find and contain rogue, etc).
Physically Deploying Air Marshal APs
APs that are designated as full-time Air Marshals for WIPS scanning can be deployed using exactly the same methodology as a regular client-serving AP in terms of wall mounting, using PoE, etc.
An Air Marshal AP has a wider effective radius than a regular AP, as it can detect and contain rogues at a lower bitrate than what is required for sustained client connectivity. The coverage radius of an Air Marshal AP for sensing and remediating against rogue access points is approximately twice as large as the coverage area for serving clients; therefore, the total coverage area for WIPS scanning is approximately 4 times as large as the area for serving clients. When planning for full WIPS coverage, the approximate ratio of Air Marshal APs to client serving APs will be 1:4, but could vary from 1:3 to 1:5 depending on the parameters of the deployment and WIPS coverage density required.

Conclusion
By understanding the spectrum of wireless security threats in today’s environment and creating a comprehensive response plan, network administrators can preclude the possibility of a serious compromise of critical network assets — including access to secure network devices that belong to the enterprise. A best-in-class WIPS platform should be capable of delivering intuitive reporting and monitoring, along with a robust suite of tools allowing for automatic alerts and security enforncement.
Meraki’s Air Marshal system includes real-time detection, remediation and alerting capabilities, including the ability to define pre-emptive policies that will intelligently take action to contain rogue access points using sophisticated containment mechanisms. Meraki’s wireless portfolio contains both dual-radio APs which can be converted into full-time sensors running in Air Marshal mode, and three-radio APs with dedicated scanning radios permanently running as Air Marshal scanners. By utilizing Meraki access points and Meraki’s intuitive web-based Dashboard interface, network administrators can create a robust WIPS policy plan, and easily deploy an airtight network to deliver enterprise-grade security in a WLAN environment.

