Loop and MAC Flap Detection on MS
Click 日本語 for Japanese
Learn more with this free online training course on the Meraki Learning Hub:
Overview
This article describes how loop detection and MAC flap feature works and how this can be used for monitoring and troubleshooting purposes.
Loop detection and MAC flap detection are available on MS12.8 and higher for supported models.
Supported models: MS130/MS120/MS210/225/250/350/355/390/410/420/425/450
MAC Flap detection is supported on MS390s starting with MS15.14+
But first, its important to understand why these features are important. Redundancy reduces downtime in the event of a link or network device failure but sometimes it can lead to complex network design. This makes maintaining a network harder as the network continues to grow to accommodate more users and applications.
One challenge with redundancy is that it can introduce loops, which can cause a broadcast storm. One solution is to enable STP that protects against layer 2 loops and most of the time it works well however if there is BPDU loss then layer 2 loop is inevitable. This can happen due to
- Duplex Mismatch
- Packet Corruption: High rate of packet corruption may cause BPDU loss
- Resource Error: High CPU utilization may cause inadequate BPDU transmission
- Shorted wire, and STP misconfiguration
To detect these issues, loop and MAC flap detection is available on Meraki switches.
Loop Detection
Loop detection feature is by default enabled in Meraki switches. It sends a loop-detection control packet and monitors those to detect the loop and generate an event log/SNMP trap on the Meraki dashboard.
All the Switches in the topology will periodically generate broadcast probe packets that are sent out on every active logical port. This period defaults to 10 seconds. These probe packets are uniquely identified by a broadcast address (ff:ff:ff:ff:ff:ff), the Cisco SNAP Organization Code (00:00:0c), and the SNAP PID 0x013c as shown in the 60 seconds packet capture below

If the switch received this packet and sees its own mac address it will report a loop to the dashboard and generate an event log shown below

An event log will be generated right away the first time a loop is detected, logs will be generated every 30 seconds after that to avoid populating event logs with the same information.
MAC Flap Detection
MAC flap detection feature is enabled by default in Meraki switches. This feature will monitor the MAC forwarding table and if a MAC address is learned 3 times or more on 2 or more different ports within 10 seconds MAC flap detection feature will report it to the dashboard as shown in the image below:
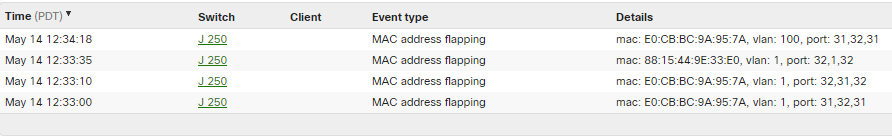
NOTE: In the above example, a MAC flap event can occur when a client appears on port 31 then to 32 then back to 31, which could mean there is a loop in the topology, or a misbehaving wireless client roaming back and forth between access points.
Additional Notes
- Loop detection feature will not log ports blocked by STP.
- If there is a loop it is expected to see both loop detection and MAC flap detection logs.
- These features are only for detection purposes and do not protect the network from the broadcast storms.
- Event log reporting is dependent on the available CPU cycle of the switch. If the broadcast storm is severe event logs will not be reported to the dashboard until more CPU cycle becomes available to do so.
- If access points are on bridge mode MAC flap event log may be seen if wireless client roams between access points faster than switch MAC address table expiration.

