MV Intelligence Training
Overview
All second and third generation (MVx2, MVx3) cameras are capable of processing powerful analytics on the camera itself and transmitting this metadata to the Meraki cloud. This revolutionary architecture dramatically reduces the cost and complexity of gathering detailed analytics in any environment.
One of the new and exciting capabilities of this platform is the ability to do machine learning-based analytics, including object detection of persons and vehicles. This allows you to understand the occupancy and use of your environments and search for specific security- or emergency-related events. To ensure robust and trustworthy object detection across various locations and scenes, we have built MV Intelligence Training.
What is Intelligence Training?
MV Analytics serves many advanced use cases today, built on top of detecting people and vehicles. To improve the current capabilities of our machine learning models and introduce new capabilities in the future, MV needs to train on visual data from a wide variety of scenes. Intelligence Training enables customers to register their MV cameras to contribute to and benefit from this model enhancement lifecycle, while providing them tools for transparency and control.
Always striving to improve
The goal of MV analytics is simple: bring as much intelligence and capability to the edge of the device and reduce the need for extensive infrastructure and complexity. By enhancing our capabilities and performance at the edge, insights from the camera can be used to deliver real-time results for security and business intelligence needs alike. The accuracy of the object detection is dependent, in part, on the ML model’s understanding of the environment.

Diversity of data is key
To improve the quality of our machine learning analytics, we need to provide training samples from a diverse range of environments: indoor and outdoor, brightly lit or candle lit, in rain, sleet, and snow. We also need to provide a diverse set of images for the objects we're interested in monitoring or tracking across these environments. People of all shapes and sizes, outfits, accessories, and poses. Vehicles of every type, size, and color. By expanding our machine learning analytics' understanding of what constitutes a person or vehicle, we enhance its ability to perform this task reliably in every setting.

Privacy by Design, Privacy by Default
The privacy of our customers' data has always been at the forefront of our product design principles. We have extensively engineered and developed our entire camera platform to ensure video encryption end-to-end, signed firmware, secure boot with trust anchor module, two-factor authentication, and many other security- and privacy-centric features are standard. Our approach to customer video is no different.
- Privacy first: MV Intelligence Training is off by default and only configurable by Organization Administrators. Customers have control over what information they choose to share and from which devices.
- Ease of use: The process to opt cameras into Intelligence Training is simple and provides complete control over the data shared.
- Bandwidth conscious: We only collect what we need, and nothing more. Changes in motion, lux, or object detections flag interesting frames for us to analyze.
How to configure Intelligence Training
There are two methods available for configuring cameras to opt-in to the Intelligence Training process: the temporary opt-in banner and the Intelligence Training page.
Temporary opt-in banner
To provide visibility and additional detail on this new feature, an opt-in banner has been added to all Organizations. This banner is only visible to Organization Administrators and provides context for the purpose and value this new feature offers to Cisco Meraki MV customers. This banner will disappear after it has been dismissed three times or immediately for all Org Admins of the network if a camera is registered into the service.
Intelligence Training page
The page is located under Cameras > Configure > Intelligence training, the Intelligence Training page gives users complete visibility and control over which cameras are opted into the process and the methods for removing collected data or opting out.
Opt-in cameras to the service
There are two flows to access the opt-in tool: via the temporary banner or the Intelligence Training page. Users can opt-in cameras by following these quick steps:
- Select the camera(s) from the thumbnail or list view
- If you have many cameras, you can search by camera name, model, or serial number
- Click the "Confirm Selection" button at the bottom
- Review the Automated Collection Agreement (downloadable and accessible always from the Intelligence Training page)
- Confirm by clicking the "Agree and Opt-in" button that appears below

Remove collected data from a time range
If training data may have been shared from a time range that shouldn't have been (for any reason), customers can remove any data from that range by following these quick steps:
- Select the camera(s) from the list
- Click the "Remove Frames" button that appears
- Select the appropriate time range where data should be removed (or select the checkbox to remove all collected data)
- Confirm by clicking the "Remove Frames" button that appears below

Opt-out cameras from the service
You can remove registered cameras from the service by following these quick steps:
- Select the camera(s) from the list
- Click the "Opt-out Camera(s)" button that appears
- Confirm by clicking the "Opt-out Camera(s)" button that appears below

Monitoring and logging
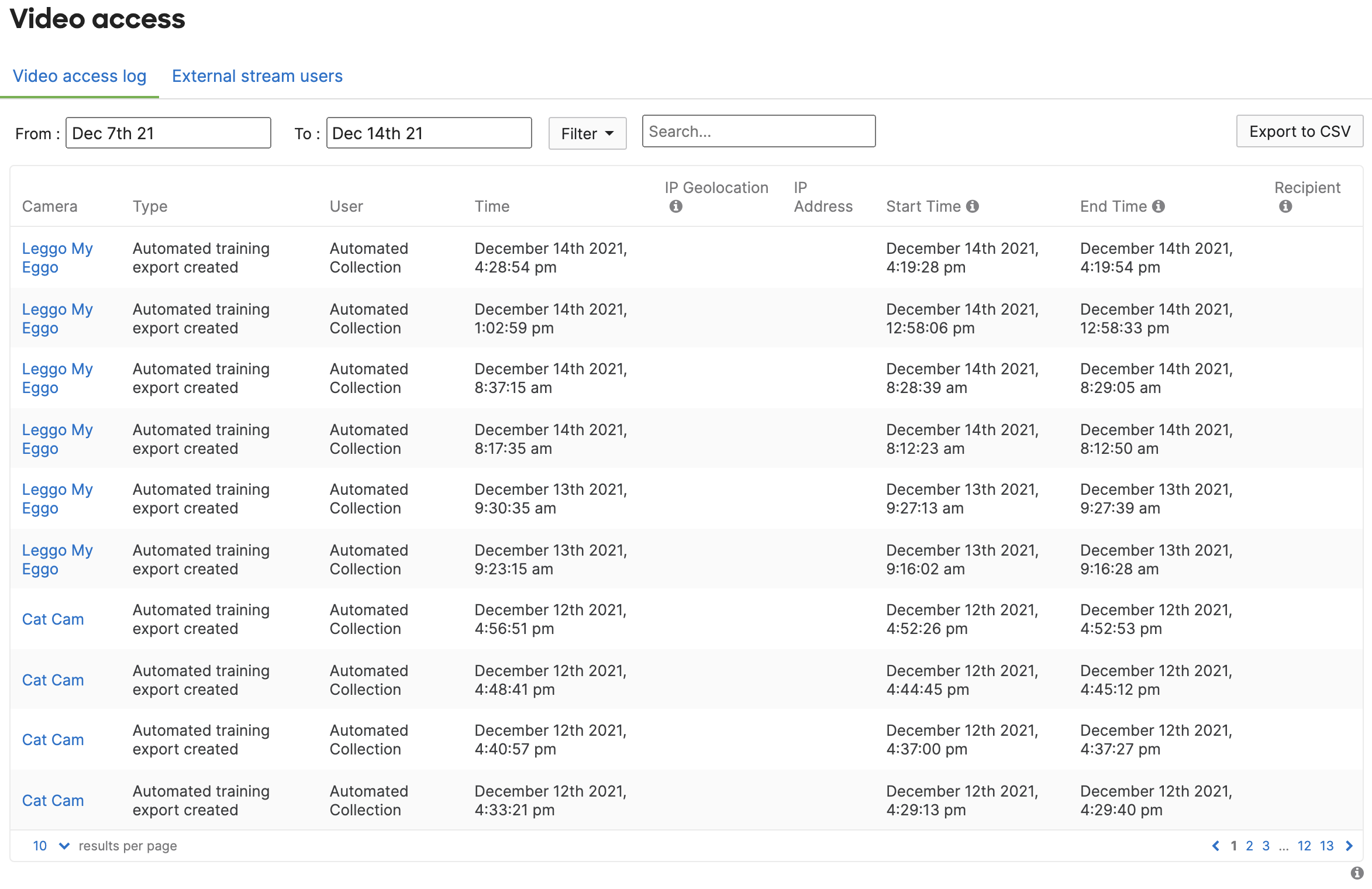
Navigate to Camera > Monitor > Video access, Organization Administrators can observe all automatic collections taken from cameras for Intelligence Training, along with start/stop timestamps. You can filter for these events directly by selecting the type filter as "Automated training export created."
Refer to Technical FAQs for more information.

