AnyConnect SAML Troubleshooting Guide
This guide covers troubleshooting of SAML authentication with AnyConnect on the MX Appliance. Before digging into troubleshooting,
-
Verify your MX is running at least 16.13+ or 17.5+ firmware
- Verify configuration on your Identity Provider and on the MX AnyConnect Settings page to ensure they are both configured correctly, see configuration guide.
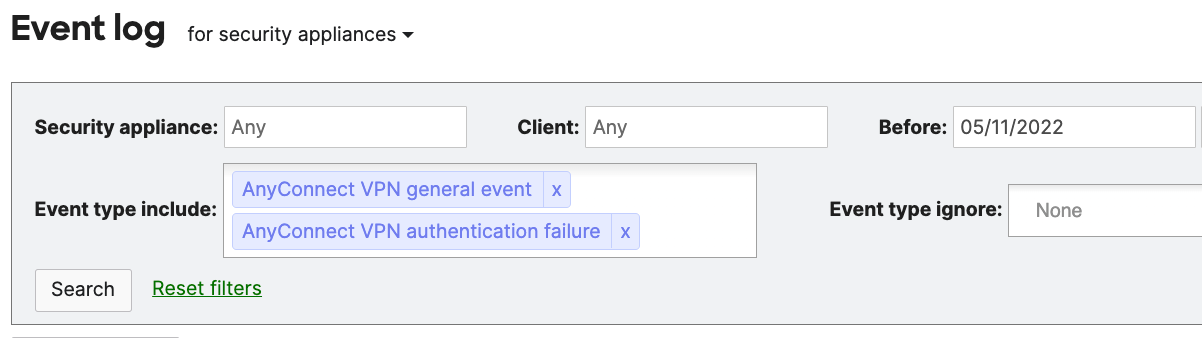
For debugging check Network-wide > Event Log for Security Appliances and Filter by “AnyConnect VPN general event” and “AnyConnect VPN authentication failure” as seen below then search.
IdP = Identity Provider (e.g. DUO, AzureAD, Okta, etc)
Use the table below to correlate error messages, understand the error and take corrective action
|
Possible error message |
Explanation |
Corrective action |
|
SSO token verify failure for user: <username> |
Single-sign-on token presented by the AnyConnect client failed verification. This can happen if the session has been removed, or if the STRAP key associated with that session has changed. |
|
|
Received null assertion message |
The SAML assertion presented is missing. Possible man in the middle issue. |
|
|
SAML assertion message content is null |
The SAML assertion presented is empty. Possible man in the middle issue. |
|
|
No response in http data |
There is no request body in the HTTP assertion message. Possible man in the middle issue. |
|
|
No SAMLResponse in assertion |
There is no "SAMLResponse=" string in the SAML assertion. Possible man in the middle issue. |
|
|
No SSO token in SAML login_final message |
There is no SSO token in SAML login_final message. This is an AnyConnect client issue. Possible man in the middle issue. |
|
|
No CSRF token in SAML login_final message |
There is no CSRF token in SAML login_final message. This is an AnyConnect client issue. Possible man in the middle issue. |
|
|
Base URL too long (> 128 char) |
The AnyConnect Server URL config attribute is too long. This is a misconfiguration issue. |
Reconfigure AnyConnect server URL to be less than or equal to 128 characters. This will require shortening the AnyConnect Server hostname and updating it accordingly in the IdP configuration portal. |
|
Warning: Base URL not https (<url>) |
This is a warning. AnyConnect Server URL does not start with https. It will be used, but is likely a misconfiguration error. |
Reconfigure AnyConnect Server URL on Dashboard. Ensure the URL starts with https |
|
Failed to base64-decode IdP metadata from text, SAML disabled |
If anyconnect_vpn_saml_metadata_text was configured, the base64-encoded metadata could not be base64-decoded. This is likely a misconfiguration error or corrupted metadata file. |
Re download the metadata file from IdP and re upload it on the Dashboard |
|
Failed to obtain IdP provider ID from metadata, SAML disabled |
The IdP metadata was provided, but it did not contain the IdP Provider ID. This is an issue with the IdP, or the translation of the metadata from the IdP to the AnyConnect server config. |
Re download the metadata file from IdP and re upload it on the Dashboard |
|
IdP Provider ID %s too long (> 384 char), SAML disabled |
The IdP Provider ID is too long. This is configured on the IdP, and extracted from the IdP metadata. |
Reconfigure new AnyConnect App in the IdP portal. |
|
Failed to generate server from SP metadata |
Failed to create an internal LASSO server object due to a LASSO library error. |
Contact Meraki Support
|
|
Failed to add IdP info to server Failed to generate Lasso server |
These two messages are due to failure to add IdP info to the internal LASSO server object due to a LASSO library error. |
Contact Meraki Support |
|
Failed to generate login Failed to generate Lasso login |
These two messages are due to failure to create a LASSO login object due to a LASSO library error. |
Contact Meraki Support
|
|
Profile is empty |
Failed to create a LASSO profile object from the LASSO login object due to a LASSO library error. |
Contact Meraki Support
|
|
Failed to init authentication request |
Failed to initialize the LASSO login object due to a LASSO library error. |
Contact Meraki Support
|
|
Failed to build authentication request |
Failed to build a LASSO authentication request due to a LASSO library error. |
Contact Meraki Support
|
|
Assertion is not url encoded |
SAML assertion received from the client is not URL encoded. This is either an IdP issue or a client issue. |
Reconfigure new AnyConnect in the IdP portal or verify configuration is correct |
|
Failed to process auth response |
Failed to process the SAML authentication response due to a LASSO library error. |
Contact Meraki Support
|
|
Failed to obtain auth response |
Failed to obtain the SAML authentication response from the processed response, due to a LASSO library error. |
Contact Meraki Support
|
|
Failed to process assertion |
Failed to obtain the SAML assertion from the SAML authentication response. |
Contact Meraki Support
|
|
Assertion is expired or not valid |
MXs local clock is not within the "Not valid before" and "Not valid on or after" times specified in the SAML assertion This could be due to a clock sync issue between the IdP and the host device (the MX in Meraki's case) It could also be due to the client attempting to use an expired SAML assertion to log in. |
Ensure you are running 16.13+ or 17.5+ |
|
Assertion audience misconfigured or mismatched. Expecting <url> |
The assertion audience presented in the SAML assertion did not match the configured value. This is likely a misconfiguration on the IdP. |
Ensure IdP configuration is correct. There should not be any trailing white spaces in the URL configuration on the IdP. |
|
No issuer in response |
There is no Issuer found in the SAML Assertion response message. This is likely an IdP configuration issue. |
Ensure IdP configuration is correct. |
|
No subject in assertion |
There is no Subject found in the SAML Assertion response message. This is likely an IdP configuration issue. |
Ensure IdP configuration is correct. |
|
No name ID in assertion |
There is no Name ID found in the SAML Assertion response message. This is likely an IdP configuration issue. |
Ensure IdP configuration is correct. |
| Authentication failed due to problem navigating to the single sign-on URL | There is an unknown error experienced with the AnyConnect embedded browser when using WebView2 | Add DWORD registry value UseLegacyEmbeddedBrowser set to 1 to the relevant registry key:
|

