AnyConnect Troubleshooting Guide
The following troubleshooting guide highlights common AnyConnect issues and resolutions.
For more information on configuring AnyConnect, see AnyConnect on the MX Appliance.
Unable to Connect
No Log-in Prompt
-
MX is running the wrong firmware version.
Ensure your MX is running the correct firmware version. The firmware section on the Appliance Status page should say MX 16.X** version. If your MX is running firmware versions MX14 or MX15, contact Meraki Support to upgrade your MX.
Some devices are restricted to MX14 firmware and cannot run AnyConnect.
MX400s and 600s are restricted to firmware version MX16. These devices might not support the full set of features for AnyConnect, or receive additional bug fixes.
-
The connection request did not make it to the MX (AnyConnect server).
If your MX is behind a router or firewall, confirm traffic is forwarded to your MX. Requests from the AnyConnect client could be reaching the upstream router or firewall device but not your MX (AnyConnect server). Take a packet capture on the WAN to confirm traffic is forwarding as expected.
If you are using a port other than the default 443, for example 1443, ensure the new port is appended to the end of the DDNS hostname. For example: "xyz.dynamic-m.com:1443"
Note: Some ISPs block TCP 443 inbound on non-business class connections to prevent customers from setting up their own web servers. These restrictions might cause issues for MX or Z-series devices that have been assigned a public IP address.
Authentication Issues
Secure gateway could not be located
Wrong AnyConnect client version
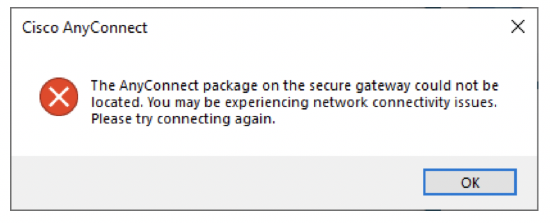
"The AnyConnect package on the secure gateway could not be located. You may be experiencing network connectivity issues. Please try connecting again."
This error might occur when a user tries to connect with an AnyConnect client version 4.7 or lower. AnyConnect client version 4.8 or higher is required to connect to the MX (AnyConnect server).
Your current location is restricting access to the internet
Unable to connect due to captive portal
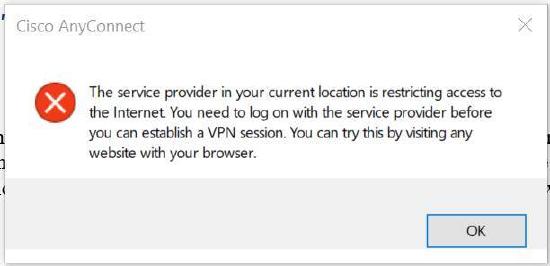
"The service provider in your current location is restricting access to the internet. You need to log on with the service provider before you can establish a VPN session. You can try this by visiting any website with your browser."
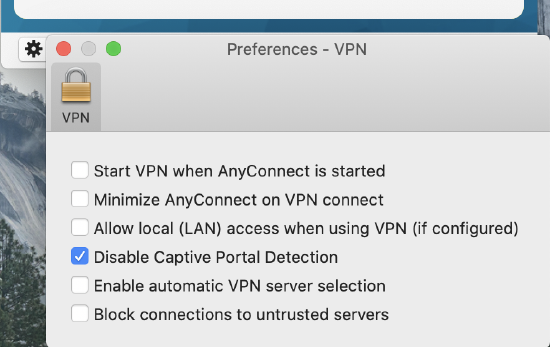
This error occurs when a captive portal is enabled on the user's network. If the error occurs on a network where no captive portal is enabled, disable captive portal detection in the AnyConnect client preferences.
Wrong Username/password Combination
Look at the event log and filter by "AnyConnect authentication failures" and try testing with different username and password or try updating your credentials.
Authentication Server Is Down or Not Responding
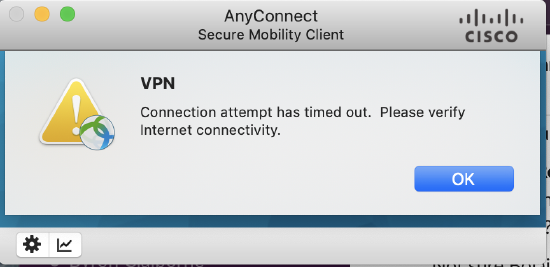
When authenticating with RADIUS or Active Directory (if offline), after entering your username and password, your AnyConnect client will look like screenshots below. When the RADIUS or AD server responds immediately with authentication failure, the user will get a prompt to reenter their password immediately. If the user does not get a prompt to reenter their credentials, the server is not responding or the response from the server is not making it back to the MX for some reason. You may even see error messages indicating an issue with the server certificate, although the issue really is that the Active Directory or RADIUS server did not respond to the authentication request.

- Ping the RADIUS or AD server to see if it is online
- Ensure your MX is listed as a RADIUS client, if authenticating via RADIUS
- Take a packet capture on LAN/VPN/WAN depending on where the authentication server resides to see if authentication requests and replies are seen been the MX and the authentication server
Certificate Validation Failure
"Certificate Validation Failure"
This error occurs when certificate authentication is enabled and none of the certificates presented by the authenticating client were issued by the root CA whose certificate was uploaded to the MX when certificate authentication was configured.
Note: Wildcard certificates are not supported at this time.

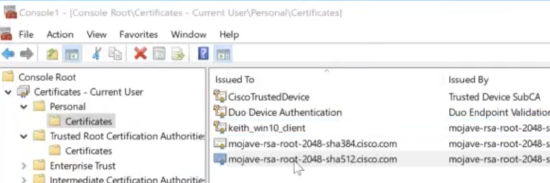
- The uploaded trusted CA certificate needs to be in PEM format.
- Check the User > Personal > Certificates folder of the client to verify that there is a valid certificate that was issued by the Trusted CA certificate uploaded to the Dashboard for certificate authentication.
Untrusted Server Certificate
"Security Warning: Untrusted Server Certificate!
AnyConnect cannot verify server:
Certificate does not match the server name.
Certification is from an untrusted source."
Security Warning Within 10 Minutes of Enabling AnyConnect
By default, configuring AnyConnect on your MX generates a temporary self-signed certificate. Then the MX initiates enrollment for a publicly-trusted certificate based on the Dynamic DNS (DDNS) hostname. This enrollment process takes approximately 10 minutes after AnyConnect is enabled to complete.
If attempting to make a connection before a publicly-trusted certificate is available, you will see the “Untrusted Server Certificate” message. After the public certificate enrollment is complete, the AnyConnect server will replace the self-signed certificate with the publicly-trusted certificate.
Security Warning After Certificate Enrollment
If this message is encountered after the enrollment process is complete:
- Ensure the device is online in the dashboard
- Ensure Dynamic DNS is enabled and resolves to the MX IP
- Ensure you are connecting with the DDNS hostname not the IP of the MX--connecting with the IP will cause a certificate error even if there is a publicly trusted certificate on the MX
- Connect to the MX with different devices to see if they all report the MX as an “Untrusted Server"
- Devices should have HydrantID Server CA O1 certificates by default
- If this is seen on some devices, check the Trusted CA folder on your client device
- If you do not see the HydrantID certificates, update your browser to the latest version
- It might be necessary to download the Root CA certificate and push it to the end device in order for it to trust the AnyConnect Server certificate
- To identify what Root CA to download, try connecting to the DDNS hostname or IP of the MX
- When the Untrusted Server message appears, click details
- Look at the Issuer field to identify the Root CA required
- The Root CA certificate can then be downloaded from the internet and pushed to the client
SAML Troubleshooting
For detailed SAML troubleshooting, see AnyConnect SAML Troubleshooting Guide.
Issues with Connection
Connected with Limited or No Access
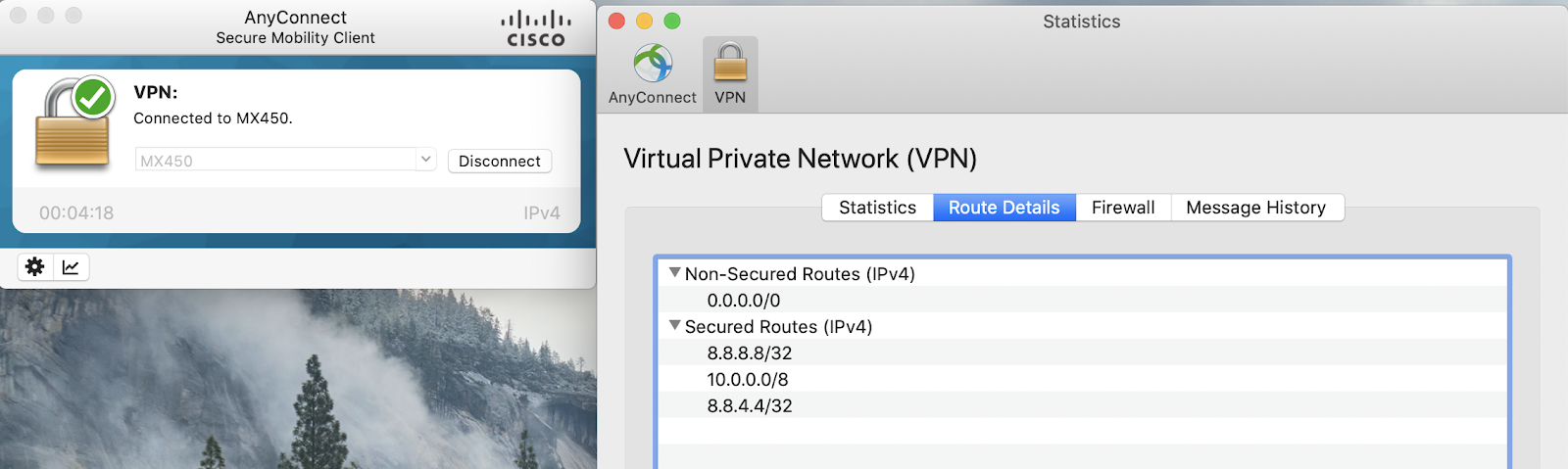
Check traffic settings on MX or routes on your AnyConnect client.
Verify the destinations have routes configured under Secured Routes in the Route Details on the client. If the destination routes are not configured, modify the traffic setting on the AnyConnect Settings page and reconnect to the AnyConnect server to update your routes.
Firewall rules or group policy.
Check the firewall rules on the MX to ensure traffic to the destination is not being blocked from your AnyConnect client IP or subnet.
Do not include port number when adding the Meraki hostname to DUO configuration.
e.g. Use meraki-hostname.com instead of meraki-hostname.com:443
According to DUO Support, the global port numbers are not required and may result in the following behavior if used:
- User is able to enter credentials and goes through the second factor authentication (if enabled).
- DUO app reports an authentication confirmation, and user is presented with a "You are successfully authenticated" page.
- Secure Client reports a warning saying "Please complete the authentication process in the AnyConnect Login window", and client is not able to access internal resources. Dashboard's Event Log reports Admin State: Auth reply timer expired at XXXX waiting for response.
Take packet captures on the AnyConnect VPN interface.
Packet captures taken on the AnyConnect VPN interface can verify if traffic is making it to the MX. To take packet captures, navigate to:
Dashboard > Network > Packet captures > Select AnyConnect VPN interface.

If traffic from the expected client is not in the packet capture, and the routing appears to be configured correctly on each end of the tunnel, contact AnyConnect TAC.
Tunnel Drops and re-establishes after initial connection is made
When initializing a tunnel, the AnyConnect client will attempt to connect using both TLS, and DTLS (Datagram TLS) over TCP and UDP 443 respectively. If it is unable to form a tunnel using the latter, it will fail back to TLS, but this requires a reinitialization of the connection, leading to a brief drop and reconnection right after the initial connection is established.
More details on the problem, and ways to resolve it can be found here
Group Policies Not Enforced
NOTE: AnyConnect Client policies are not currently synchronized with the dashboard. Clients will always appear with a "normal" policy unless they have been manually modified by an administrator.
Ensure that a Filter-ID attribute is being passed by your RADIUS server to the MX in an Access-Accept packet. This can be accomplished by taking a packet capture on the appropriate interface, validating that the attribute exists, and that its value exactly matches the name of the policy defined in the dashboard.
Troubleshooting Dynamic Split Tunneling
Dynamic split tunneling is a client-side feature. The AnyConnect server on MX/Z devices is responsible only for pushing the list of included and/or excluded domains to the client. For other issues related to functionality, contact AnyConnect TAC.
Note: Dynamic split tunneling is not currently supported on Linux or mobile devices.
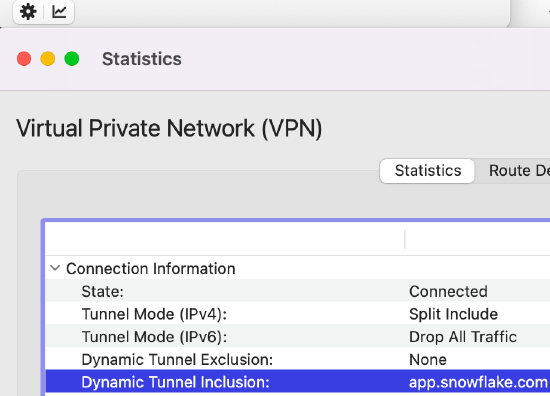
To verify if clients are receiving the expected lists, review the Dynamic Tunnel Exclusion and Inclusion fields under the VPN tab of the Statistics window of the AnyConnect Client.
If you need to change your list of URLs during production hours, you will need your clients to disconnect any active VPN sessions they have before the updates will propagate to them.
Additional Resources
Cisco Secure Client Diagnostics and Reporting Tool (DART)
For instructions on how to use the Cisco Secure Client Diagnostics and Reporting Tool (DART), please refer to Using the Cisco Secure Client Diagnostics and Reporting Tool (DART).
Cisco Reference for Other AnyConnect Client Issues
For assistance on other issues relating to the AnyConnect Client, see Cisco AnyConnect Secure Mobility Client Administrator Guide, Release 4.0 in Cisco Docs.

