Get Started - Securing Access to Private Applications and Networks
Cisco Secure Connect secures access to private network destinations and applications via site-to-site VPN tunnels, client-based VPN access tunnels (Cisco Secure Client VPN) with identity-based control, clientless (browser-based) ZTNA (Zero Trust Network Access) per-app access using any browser and client-based ZTNA using Zero Trust Access policy controls access to applications enabled with client-based ZTNA.
With these you will be able to:
- Secure Applications with granular access control so only authorized users can access them
- Define and manage internal applications for the use in Access policies
- Provide least privileged access to users that are connecting from anywhere using a client or via a browser
- Only allow user devices that meet the device posture requirements of your organization
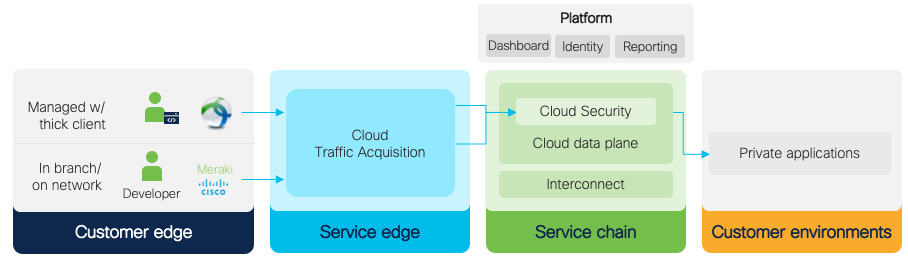
What’s the difference between client based and clientless?
Client based VPN Access
With client based, as the DTLS terminates, the user is prompted for authentication, and once authorized the user’s traffic is directly routed through the Cloud Deliver Firewall (CDFW) for finer-grained access control to private resources based upon contextual controls such as identity and posture.
CDFW policies apply when:
SourceTraffic |
Destination Traffic |
|
| Application hosted in Private Cloud or On Prem Data Center |
Application hosted in Branch | |
| Secure Client VPN |  |
 |
| Branch |  |
Note: Meraki branches connected to the same cloud hub are secured by their local firewalls rather than CDFW. |
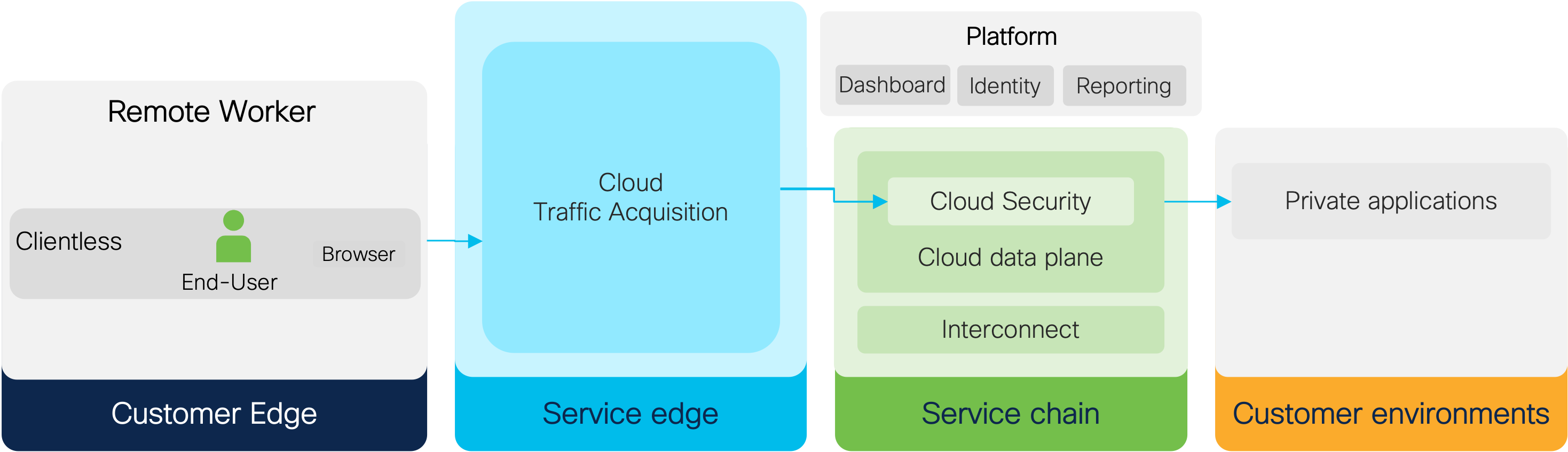
Clientless (Browser-based) ZTNA
Clientless (Browser-based) ZTNA allows you to leverage a web browser for user authentication and application access without requiring users to install the Cisco Secure Client on their devices. This feature addresses situations where it might not be feasible or desirable to install the Cisco Secure Client. For example, you might want to:
- Control user access to applications on devices with operating systems that are not currently supported by Cisco Secure Client.
- Provide third-party access to applications on devices that might not be owned or managed by your company (e.g., contractor or partner-owned devices)
Each user and device is verified and validated by a Zero Trust Access Policies, before access is permitted to an app or resource. The verification is granular, per session. Users have the freedom to connect from anywhere with any policy-compliant device.
Clientless (Browser-based) ZTNA
Client-based ZTNA
Client-based ZTNA offers secure private access to internal network resources for devices with Cisco Secure Client. ZTNA provides more granular control than traditional remote access VPNs as it operates higher up the network stack with full visibility to the fully qualified domain name (FQDN) of your private application. This additional visibility combined with per-app connection provides greater security by limiting access to only the required network resources, adhering to Zero Trust Principles.Client-based ZTNA works well with most modern applications that are client-initiated. Most web applications will work out of the box. Applications that can struggle with the reverse proxy architecture of ZTNA are server-initiated or client-to-client applications. For customers with private applications not supported by ZTNA, Cisco recommends using the traditional remote access VPN that is included in Cisco Secure Connect.


