Cisco Secure Connect - Remote VPN Access Start
Overview
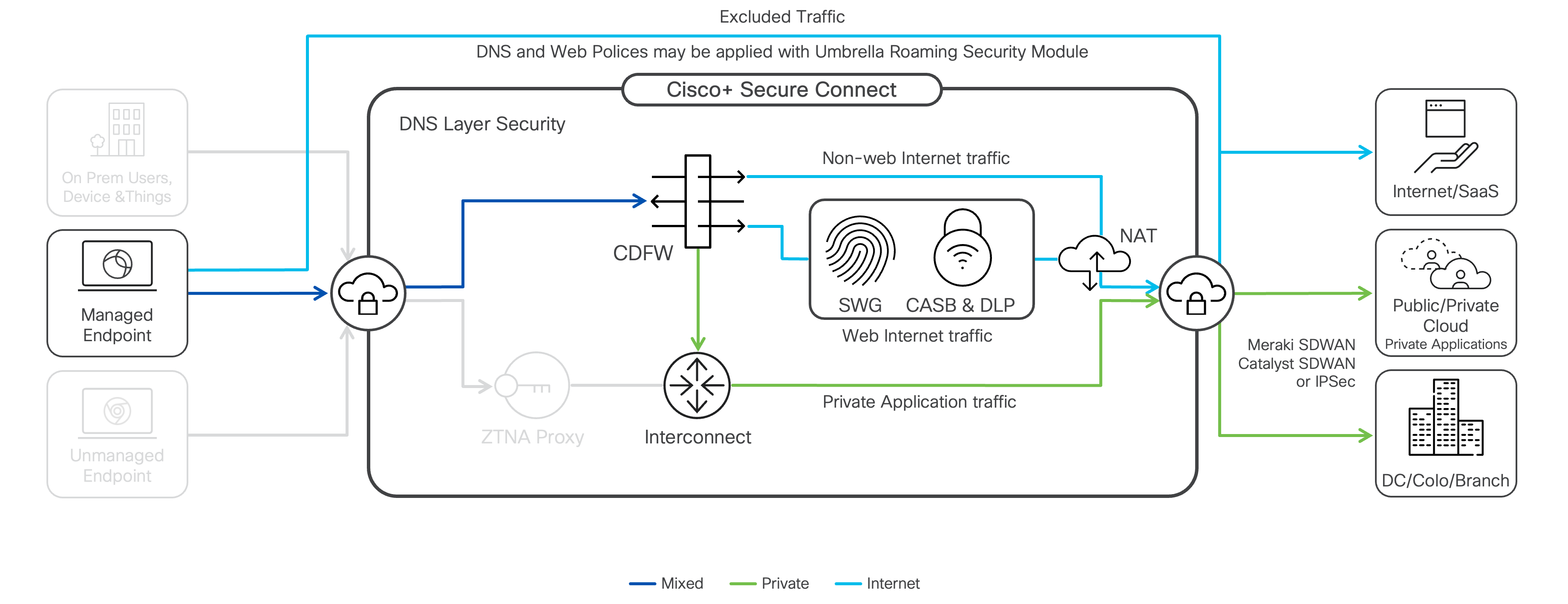
Cisco Secure Connect enables remote users to access private applications from anywhere through Secure Connect fabric using Cisco Secure Client (formerly the Cisco AnyConnect client). Identity-based access control is available using SAML authentication through customer’s IdP (Identity Provider) solution. Endpoint Compliance, also known as Endpoint Posture, is also evaluated when connecting to remote VPN access.
Prerequisites
|
Requirement |
Details |
|---|---|
| DNS server IP address(es) | DNS Servers is used to resolve private application host-names. |
| Default domain(s) | Default domain is used to complete any unqualified host names input by users when accessing private applications through the secure tunnel. |
|
Client assigned IP address pools |
Each region specified must have a minimum of two locations configured with a private address pool. (Notice: We recommend to use contiguous private address pools for an easy route summarization and rule updates.) These pools cannot be overlapping with any existing addresses/subnets used in customer internal network. At least one region is required. For a complete list of supported regions and data center locations please check here. |
| DTLS support - UDP port 443 Open | For optimal performance of Remote Access VPN UDP port 443 should be open for the client to connect. If UDP port 443 is not open TCP port 443 will be used, adding latency and reduce throughput. |
Remote Access VPN Setup
-
Require Configurations
Next Step - Network and Policy Setup
After completing the Remote Access setup, the rest of tasks can be complete depending on your situation.

- Enable application connectivity
- Setup a Meraki Network
- Setup a Non-Meraki Network
- Be sure to select tunnel type of Private Access
- Add all internal networks (routes) behind the private tunnel as client prefixes to the tunnel
- Add routes to the IPSec termination device for all remote access client subnets provisioned previously
- Apply policies
- Import policy (Optional)
- Create new firewall rule

