Remote Access - Secure Client configuration
Click 日本語 for Japanese
Secure Client Configuration (Optional)
For Secure Client configuration, you are able to:
- Define the timer for Session Timeout
- Enable Auto-Connect remote users on Start
- Enable Auto-Reconnect remote users on Start.
- Customize a Post-authentication-banner
- Allow users to manual input host
- Customize Logon enforcement for RDP
- Customize VPN establishment for RDP

Define the timer for Session Timeout
The number of hours (1-9999) can be defined for the VPN connection to remain active.

When the remote users reach the maximum time of the VPN session, the VPN connection will be disconnected with below error message pop up and they will need to re-connect to the VPN for accessing company's resource.

Enable Auto-Connect remote users on Start
Allow you to choose automatically established a VPN connection when Cisco Secure Client starts.

Enable Auto-Reconnect remote users on Start
Allow you to enable re-establish a VPN connection if you lose connectivity.
Customize a Post-authentication-banner
The message you provide will be displayed to a remote use upon successful VPN connection and authentication.

Allow users to manual input host
Allow remote users to enter different VPN addresses than those listed in the dropdown menu when turned on.

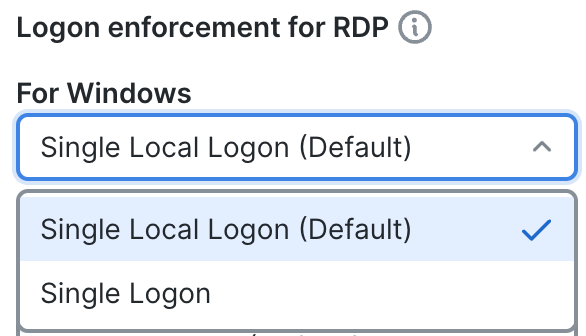
Customize Logon enforcement for RDP
Allows a VPN session to be established from a Remote Desktop Protocol (RDP) session. Split tunneling must be configured in the group policy. Secure Client disconnects the VPN connection when the user who established the VPN connection logs off. If the connection is established by a remote user, and that remote user logs off, the VPN connection terminates. For more informations, please refer to this link.

- Single Local Logon (Default) - (Local: 1, Remote: no limit) Allows only one local user to be logged on during the entire VPN connection. Also, a local user can establish a VPN connection while one or more remote users are logged on to the client PC. This setting has no effect on remote user logons from the enterprise network over the VPN connection.
- Single Logon - (Local + Remote: 1) Allows only one user to be logged on during the entire VPN connection. If more than one user is logged on, either locally or remotely, when the VPN connection is being established, the connection is not allowed. If a second user logs on, either locally or remotely, during the VPN connection, the VPN connection terminates. No additional logons are allowed during the VPN connection, so a remote logon over the VPN connection is not possible.
Customize VPN establishment for RDP
Choose the type of user for a VPN session to be established from a Remote Desktop Protocol (RDP) session.

- Local user only (Default) - Prevents a remotely logged-on (RDP) user from establishing a VPN connection.
- Allow Remote Users - Allows remote users to establish a VPN connection. However, if the configured VPN connection routing causes the remote user to become disconnected, the VPN connection terminates to allow the remote user to regain access to the clients PC. Remote users must wait 90 seconds after VPN establishment if they want to disconnect their remote login session without causing the VPN connection to be terminated.

Secure Client on Linux hosts does not support "VPN establishment for RDP". VPN establishment rules for Linux hosts only apply to SSH sessions. Please refer to this link for more details.
If you want to learn more on how to deployment Remote VPN Access, please refer to Remote Access Deloyment.

