Remote Access - Traffic Steering
Click 日本語 for Japanese
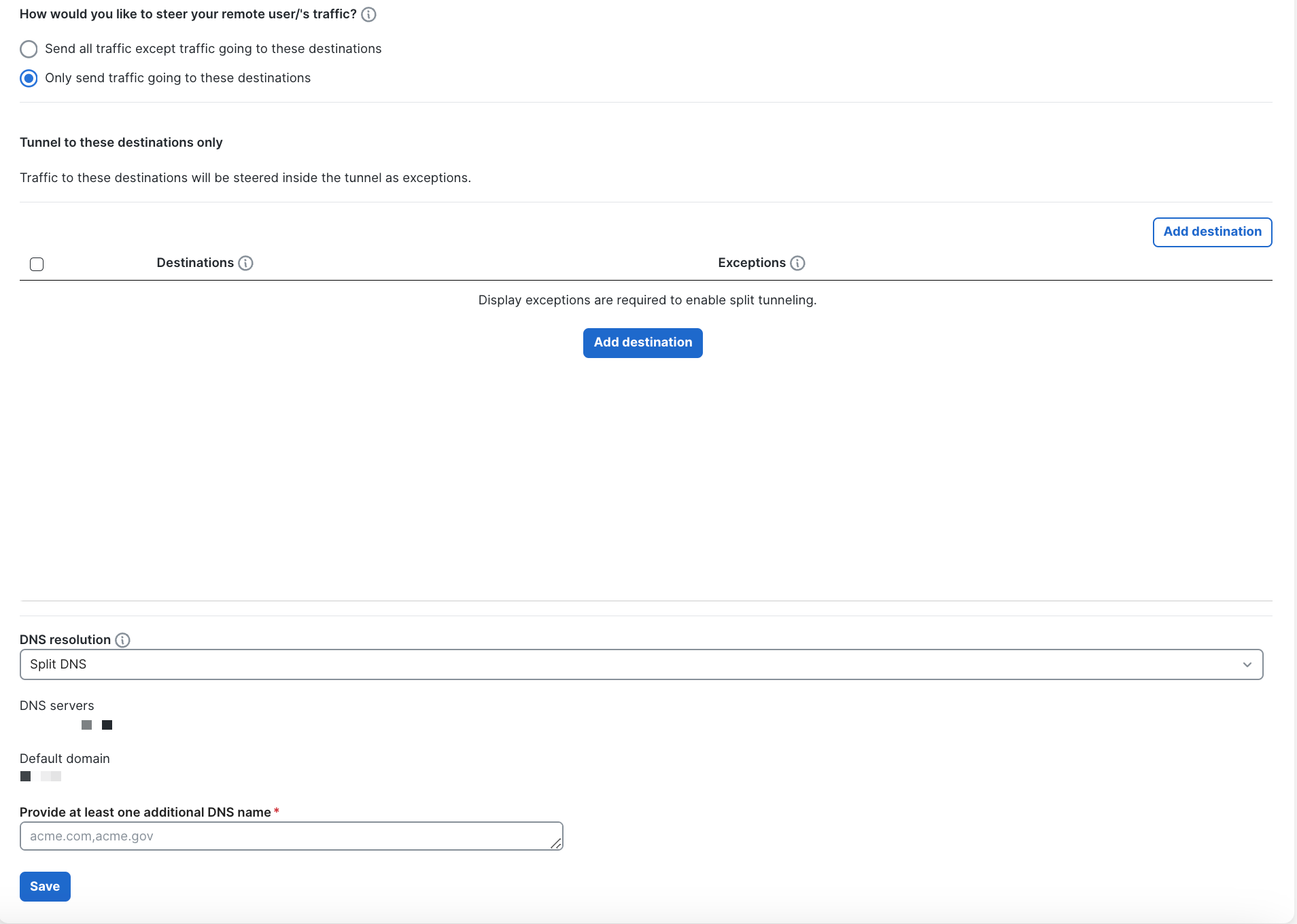
Traffic Steering (Optional)
Traffic Steering, also known as split tunneling, enables you will be able to decide what traffic you want to encrypt and transit over the Secure Client connection (inside the tunnel), and which traffic (if any), you want to go directly to internet resources (outside the tunnel).
By default, all traffic will be sent through Secure Connect tunnel. Users will not have access to local resources while connected.

If you want to enable Traffic Steering, select Customize traffic steering, you can
- Enable LAN access for remote users to designate LAN access outside secure tunnel if access to local resources, e.g. local printers, is required while connected.

- Only send traffic going to these destinations with exceptions. For example, whatever you specify under destinations, only these destinations will be sent through Secure Connect tunnel. You can add Exceptions to exclude a certain subset of destinations under this rule to steer out traffic from Secure Connect tunnel.
To be noted: All Exceptions must match the format used for the Destinations (CIDR or domain).
- Send all traffic except traffic going to these destinations with exceptions. For example, when you choose this selection, traffic will by default send through Secure Connect tunnel except the destinations you specify. The destinations you added will be steered outside the tunnel. You can add Exceptions under this rule such that a subset of destinations will still be sent through Secure Connect tunnel.
To be noted: All Exceptions must match the format used for the Destinations (CIDR or domain).

When using the Traffic Steering option "Only send traffic going to these destinations," at least one CIDR address must be configured as a destination.
DNS resolution mode
A secondary DNS server can be configured for a failover purposes. A client will failover to the secondary DNS server IP in case the primary is either not responding or taking longer than expected to respond to DNS queries.
There are three DNS resolution modes available:
- Standard DNS (Default)
All of the DNS queries move through the VPN tunnel. In the case of a negative response, the DNS queries can fall back to DNS servers which are configured on the physical adapter.
In the default Standard DNS mode, how queries are sent depend on the operating system.
- Modern Windows OS will send DNS queries to the VPN interface and LAN/physical interface at the same time and just uses the fastest response.
- Older Windows OS and some other operating systems may try the VPN first and “failover” to the LAN/physical interface. - Tunnel All DNS
With Tunnel All DNS, all queries must be sent via the VPN interface. This mode is only really advisable if you wanted to ensure no DNS leaked outside the VPN for security reasons. The performance of the tunnel and private access will directly impact the performance of DNS.
In this mode, Secure Client blocks all DNS traffic except via the VPN interface, and the Primary DNS server must be able to resolve ALL internal and external queries (eg. Recursion enabled). - Split DNS
With Split DNS, Secure Client can only allows internal DNS queries via the VPN interface, and only allows external DNS queries via the LAN/physical interface. It will be beneficial that:
- May offer better DNS performance for external DNS queries, whilst still maintaining internal DNS resolution
- Prevents DNS query information for your internal domains “leaking” outside the VPN
- Allows you to control the behavior when you have an external and internal copy of the same zone.

Please NOTE that:
- Split DNS is only available when you enable "Only send traffic going to these destinations"
- At least two DNS domain names are needed (separate by comma)
More on behaviour of DNS queries with Secure Client can be found here.
Split DNS mode is only available when "Only send traffic going to these destinations" is selected.
If you want to learn more on how to deployment Remote VPN Access, please refer to Remote Access Deloyment.

