Cloud Monitoring for Catalyst Eligibility and Requirements for Onboarding
This guide is for Cloud Monitoring for Catalyst Switches. See Cloud Monitoring for Catalyst Wireless Requirements for detailed information on Catalyst 9800 wireless controllers requirements.
Onboarding is the process of enabling cloud-monitoring functionality for an existing Catalyst switch. For background information regarding cloud monitoring for Catalyst, please refer to Cloud Monitoring Overview and FAQ.
Learn more with these free online training courses on the Meraki Learning Hub:
Eligible Catalyst Devices
Cloud monitoring for Catalyst currently supports the following hardware and software:
-
Catalyst 9200 series switches (including 9200L and 9200CX models)
-
Catalyst 9300 series switches (including 9300L and 9300X models)
-
Catalyst 9500 series switches
-
The full list of supported Catalyst switches is available at: Supported Catalyst 9000 Series Switches (Cloud Monitoring)
-
IOS-XE 17.3.1 - 17.10.1 and IOS-XE 17.12.3
-
IOS-XE software downloads are available at https://software.cisco.com/download/home
-
IOS-XE upgrade instructions and release notes: https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst9300/software/release/17-3/release_notes/ol-17-3-9300.html#id_67613
-
Current recommended IOS-XE release information can be found at: https://www.cisco.com/c/en/us/support/docs/switches/catalyst-9300-series-switches/214814-recommended-releases-for-catalyst-9200-9.html#anc4
-
To enable cloud monitoring for Catalyst, the Catalyst device must be connected to, registered and provisioned by Meraki Dashboard. The Cloud Monitoring Onboarding application was created to facilitate this process. This application will help configure your Catalyst device to establish a TLS connection to the Cisco cloud infrastructure and register it to your dashboard organization. From there, dashboard will configure the necessary services on your Catalyst device to enable cloud monitoring. To utilize Cloud Monitoring, all Catalyst switches that will be added to the Meraki Dashboard must have an active DNA Essentials or DNA Advantage license. See Cloud Monitoring for Catalyst Onboarding for additional details.
Pre-Onboarding
- Meraki Dashboard Account
-
Verify the ability to log in to https://dashboard.meraki.com/
-
Or create a free account. Instructions are available at: https://documentation.meraki.com/General_Administration/Organizations_and_Networks/Creating_a_Dashboard_Account_and_Organization.
The Dashboard Account used to onboard Catalyst devices must have full read/write access for the organization to which switches will be onboarded.
-
From My Profile, choose "Generate new API key" or use an existing key. Note that a full admin account must be used. SAML log-in is not supported for API key creation
- Additional documentation regarding enabling API access is available at: https://documentation.meraki.com/General_Administration/Other_Topics/Cisco_Meraki_Dashboard_API#Enable_API_Access.
If an "invalid API key" error message appears, confirm the key and try again. API keys may take up to 15 minutes to become active in the onboarding application after creation.
-
The computer from which the onboarding application is run must be able to reach api.meraki.com and meraki-cloud-monitoring-onboarding-app.s3.amazonaws.com on TCP port 443
-
The onboarding application is a stand-alone executable file; security settings on your local device must permit running this application and accessing the host names listed above
-
Onboarding Application software updates are automatically checked at meraki-cloud-monitoring-onboarding-app.s3.amazonaws.com.
-
-
The Catalyst devices to onboard need access to the Cisco cloud
-
Ensure any firewall rules in place allow communication with the gateway corresponding with the dashboard region on TCP port 443:
-
Americas: us.tlsgw.meraki.com
-
EMEA: eu.tlsgw.meraki.com
-
Asia Pacific and Japan: ap.tlsgw.meraki.com
-
-
HTTPS proxies to access the API endpoint and the TLS gateway are not currently supported. If necessary, ensure rules are in place to allow direct HTTPS connections to each.
- Determine which dashboard networks to assign switches to
-
The network must be "switch" or "combined" type. Note: if type "combined" then it must already include a "switch" network
- Information about creating a new network is available at: https://documentation.meraki.com/General_Administration/Organizations_and_Networks/Creating_and_Deleting_Dashboard_Networks#Creating_a_Network
-
If not already configured as such, the onboarding process will automatically enable "Unique Client Identifier" tracking method for that network.
-
When the tracking method is changed, clients may appear to be duplicated until previously collected data ages out and is no longer valid. For more information, see: https://documentation.meraki.com/MX/Monitoring_and_Reporting/Client-Tracking_Options.
-
- Back up the current running configuration on the switch prior to beginning onboarding (i.e., copy run flash:config-backup.txt)
Device Configuration Requirements
Connectivity to Meraki dashboard must be accessible via a front-panel switch port (not the management port).
SSH Connection
To perform these actions the onboarding application must connect to the device(s) over SSH. This connection must be successful in order to proceed any further as a failure to establish an SSH connection will stop the device eligibility check process entirely.
Onboarding does not support Telnet
-
The onboarding application SSH client initiates the connection with the device and negotiates the secure tunnel setup.
-
Authenticate to the device using the user provided device credentials
-
Verify device user privilege level. The device user credentials provided must have IOS-XE privilege-15 access.
Device Pre-checks
Once the SSH session connection is open, the rest of the pre-checks can be performed. The onboarding application will perform all checks regardless if any checks fail.
The following items are not directly configured by the Onboarding application since they can be specific to your network environment. Please consider these requirements carefully.
IOS-XE Versions
-
Devices must be running IOS-XE 17.3.1 - 17.10.1 or IOS-XE 17.12.3
Network Payload Encryption (NPE) Required
-
Devices must be running IOS-XE image WITH payload encryption
Device Clock
-
An NTP server is configured on the device - ntp server {address}
-
The device clock must reflect the correct current time in order to establish the TLS tunnel to Dashboard
IP routing Enabled
-
IP routing must be enabled on the device - ip routing
-
IP routing is required for NETCONF and Telemetry streaming to function on Catalyst devices.
Default IP route
-
Only the default VRF is supported
-
Along with IP routing enabled, the device also must have a default route. Use of ip default-gateway is not supported
IP domain name-server
-
The device must have a DNS server configured - ip name-server {Domain server IP address}
-
DNS is required for hostname resolution of the Dashboard TLS tunnel IP address.
IP domain lookup Enabled
-
The device must allow domain lookup to connect to the dashboard via the DNS host name - ip domain lookup
AAA new-model and authorization
The aaa new-model command immediately applies local authentication to all lines and interfaces (except console line line con 0). If a telnet / SSH session is opened to the switch after this command is enabled (or if a connection times out and has to reconnect), then the user has to be authenticated with the local database of the switch. It is recommended to define a username and password on the switch before you start the AAA configuration, so you are not locked out of the switch.
-
The device must have AAA enabled with aaa new-model
-
AAA authorization must be set to start an exec shell with aaa authorization exec default local or aaa group name
-
If the aaa authorization exec default specifies a aaa server-group name first in the list, a aaa group server tacacs+ {server-group name} server group with that group name must be configured
Loopback Interface Available
-
A dedicated loopback interface will be configured on the device used to communicate with the dashboard. The device must have loopback interface numbers 1000 or 2000 available
VTY Slots Available
-
For dashboard to communicate with the device, two VTY lines will be configured. The device must have at least two unused consecutive VTY slot numbers between 16 and 98
Access Control Lists
-
Two IP access-lists will be configured on the device and applied to the VTY lines to permit only the dashboard IP address on port 2222 inbound and outbound
-
There can be no existing ACL names that include the text : "MERAKI_BLOCK", "MERAKI_VTY_IN", or "MERAKI_VTY_OUT"
TLS Gateway Connectivity check
-
To confirm the dashboard TLS Gateway is reachable, the device must be able to open a telnet session on port 443 to the TLS Gateway
-
Ensure that outbound telnet connections are allowed on the line VTY - transport output all or telnet
-
The outbound telnet connection is only established to verify that port 443 is accessible. No data is from the device to the TLS gateway over this telnet sessions.
Downloading the Onboarding Application
The onboarding application can be downloaded from the following links:
Alternatively, the onboarding application is also available for download through the Meraki dashboard. To access it, go to Network-wide > Add Devices from the navigation on the left side. In this section, click on the link to add Catalyst switches to the dashboard.
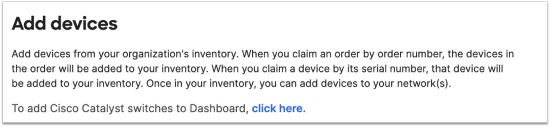
From the pop-up select your operating system to download the version for your computer.

Onboarding
Once you have completed the pre-requisites and confirmed your devices eligibility and configuration and installed the Onboarding Application, you are now ready to Cloud Monitoring for Catalyst Switch Onboarding

