HTTP CONNECT Proxy Support on MR Access Points
Click 日本語 for Japanese
Overview
An HTTP Proxy server acts as an intermediary between a client and the final destination server. Let’s consider two network deployment scenarios: the one without HTTP proxy and the one with HTTP proxy.
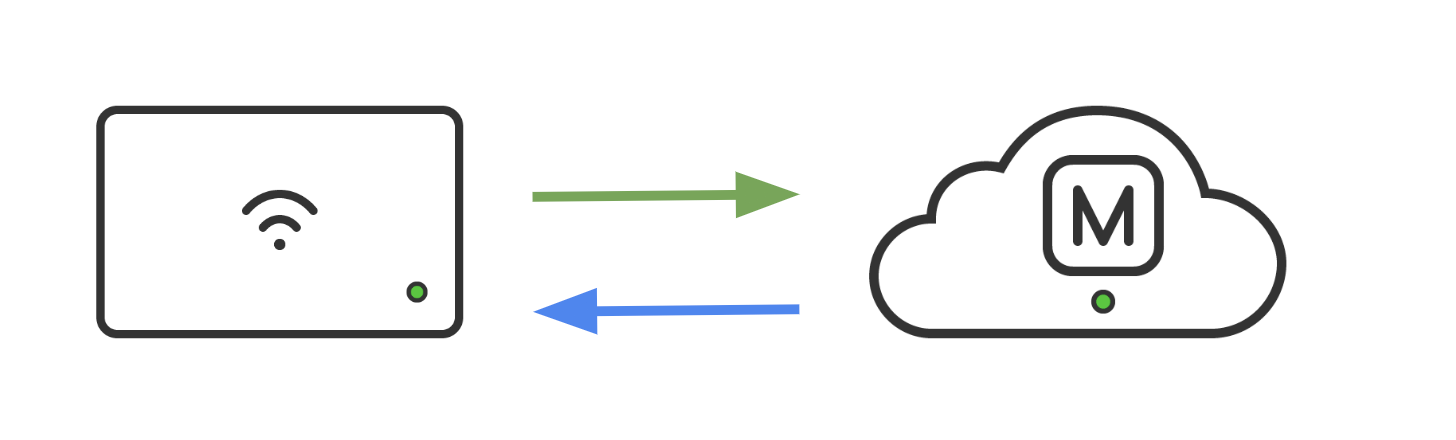
Typically, in networks without an HTTP proxy server, any device (including MRs) has direct access to the Internet. For this example, we will not consider additional restrictions like firewall rules and access control policies, site-to-site VPN connection with full tunneling, etc. In this case, a simplified network diagram would look like this:
In some highly secure network environments filtering traffic through a proxy server might be necessary. In this case, a simplified network diagram would look like this:
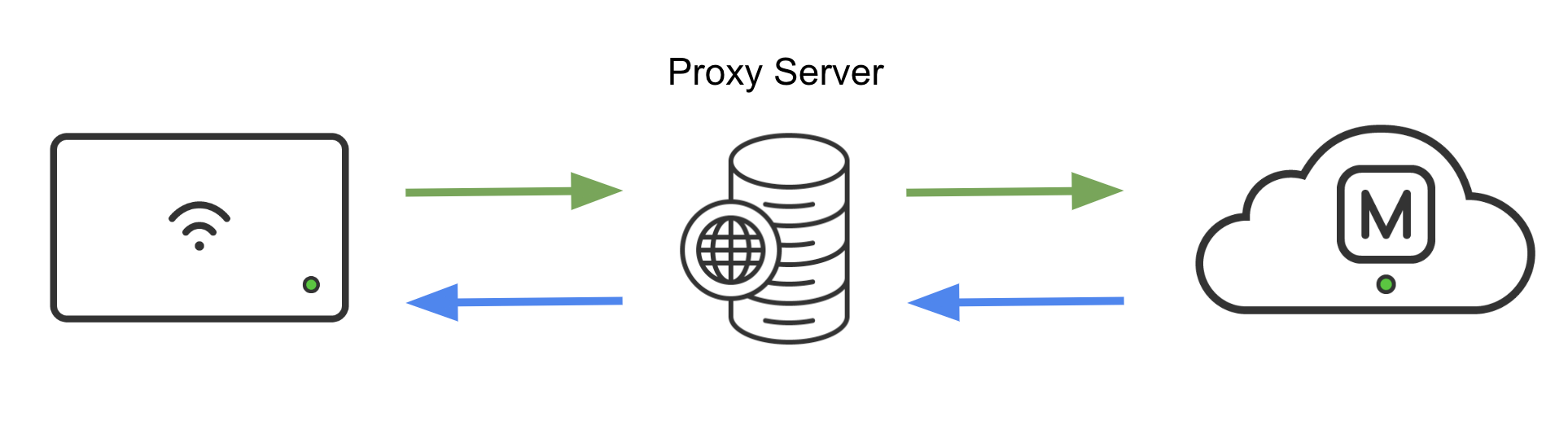
Given the nature of Meraki's cloud-native dashboard, it could be challenging for customers to both meet security requirements (using an HTTP proxy server) and utilize the simplicity of the Meraki dashboard. Therefore, we introduced a new feature - HTTP CONNECT Proxy in MR 30.1 and newer firmware to help address these challenges.
Note: All APs running MR 27.X or older firmware could use a Web proxy feature that can be configured on the Local status page. The Web proxy feature has been deprecated in MR 28.X and MR 29.X firmware for Wi-Fi 6 and newer APs. The HTTP Connect Proxy feature described below is a unique and separate feature available on Wi-Fi 6 and newer APs running MR 30.X or more recent firmware.
HTTP CONNECT Overview
The HTTP CONNECT method is one of the ways for devices (e.g., MRs) behind an HTTP proxy to establish two-way communications with the requested resource (e.g., Meraki dashboard). The main benefit of this method is that if the end-to-end encryption (e.g., SSL/TLS) is in use between a device (e.g., MR) and the final destination (e.g., Meraki dashboard), the HTTP proxy server does not need to decrypt this connection to allow it through.
Note: With MR 28.1 and newer firmware, Wi-Fi 6 and newer AP use TCP 443 (TLS) as a default way of dashboard communication. This is important because the HTTP CONNECT method allows the communication between an MR and Meraki dashboard to stay fully encrypted.
If an AP is configured with the HTTP CONNECT option, it simply asks the HTTP proxy server to establish a Layer 4 TCP tunnel (by sending an HTTP CONNECT request) to the Meraki dashboard on the AP’s behalf:
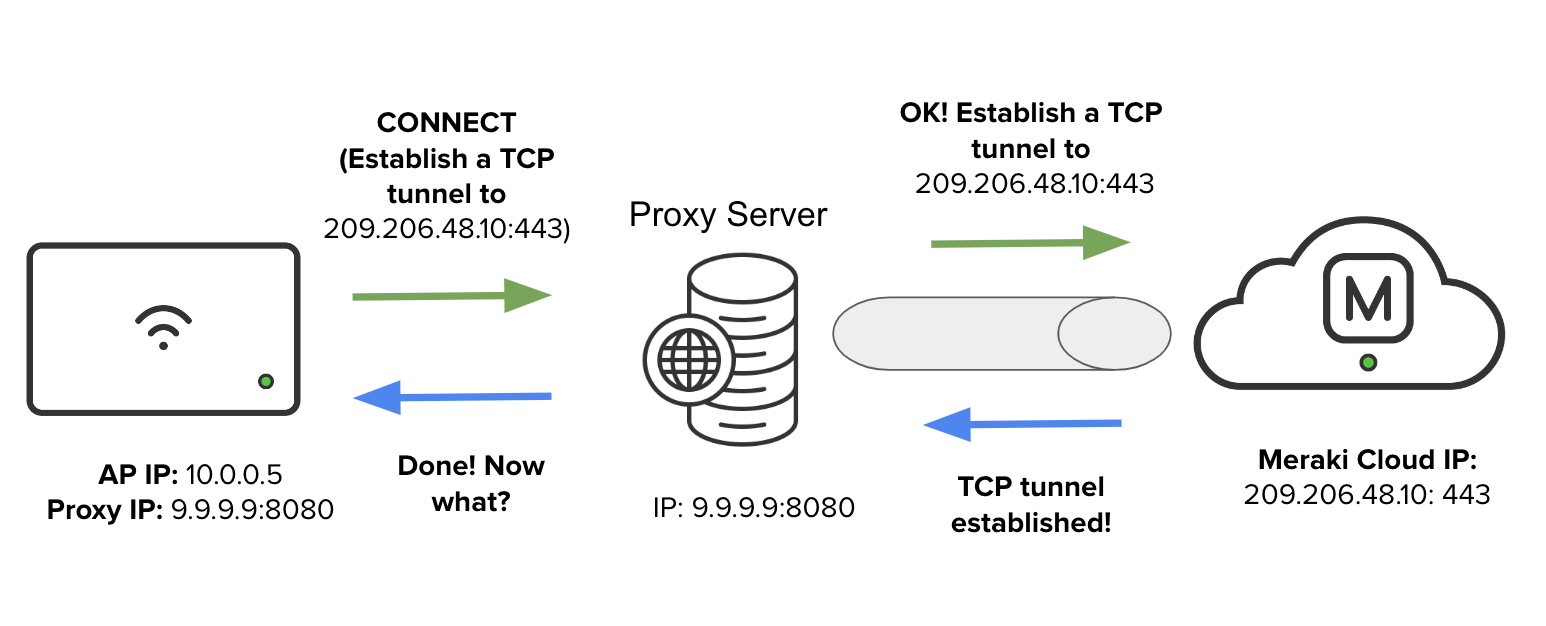
Once the Layer 4 TCP tunnel is established, the AP would negotiate a TLS connection with the Meraki dashboard through the tunnel between the HTTP proxy server and the Meraki dashboard. The HTTP server merely streams messages received from the AP and forwards them to the Meraki dashboard while relaying the return messages back to the AP:
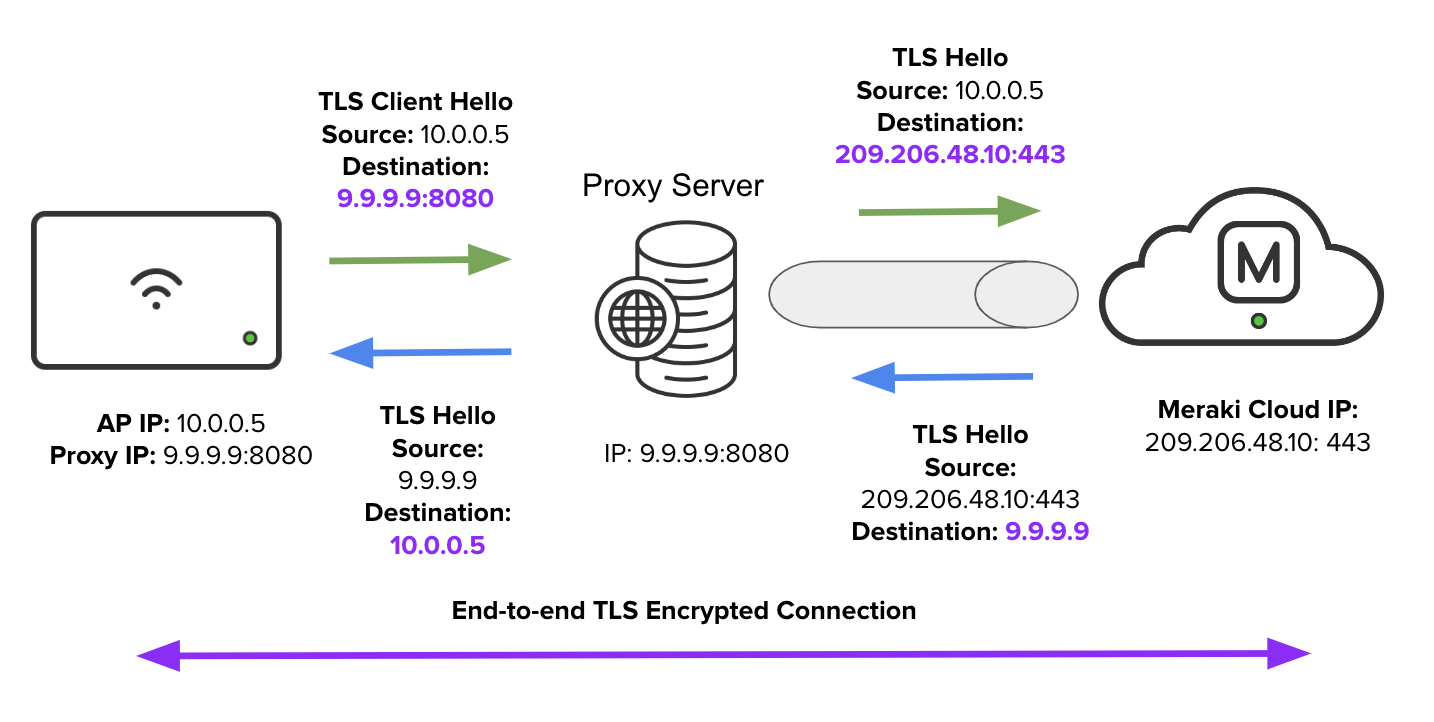
Supported Models and Requirements
Supported APs
-
Wi-Fi 6 Compartible APs (MR45, MR55)
-
Wi-Fi 6 APs (MR28, MR36, MR36H, MR44, MR46, MR46E, MR56, MR76, MR78, MR86)
-
Wi-Fi 6E APs (MR57, CW9162I, CW9164I, CW9166I)
-
Wi-Fi 7 APs (CW9171I, CW9172I/H, CW9174I/E, CW9176I/D1, CW9178I, CW9179F)
Required Firmware
-
Firmware: MR 30.1 or newer firmware
Additional Requirements and Considerations
-
HTTP proxy server must support the HTTP CONNECT method
-
If an Auto Proxy Discovery via DHCPv4 is used (see the Configuration section below for details), DHCP Server that issues DHCPv4 leases to APs must be configured with the DHCP Option 60 that is set to “MERAKI”
-
If an Auto Proxy Discovery via DHCPv4 is used (see the Configuration section below for details), DHCP Server that issues DHCPv4 leases to APs must be configured with the DHCP Option 43, which is set to the IP address of the HTTP proxy server and a port.
- The format for the Option 43 is as follows: <tag (1 byte)><size (1 byte)><value (vary)>
- Tag 02 - HTTP Proxy IP address, length 04 following four octets, representing IPv4.
- Tag 03 - HTTP Proxy port, length 02 following two octets, representing port
- You can use an IP-to-hex converter to help with the IP portion and a decimal-to-hex converter to help with the port portion.
Examples:
- 02:04:C0:A8:80:10:03:02:0C:38 represents 192.168.128.16:3128
- 02:04:0A:50:0A:5E:03:02:0C:38 represents 10.80.10.94:3128
An MX appliance is configured in the example below with DHCP options 43 and 60.
02:04:C0:A8:80:10:03:02:0C:38 in the DHCP option 43 represents 192.168.128.16:3128, where the 192.168.128.16 is the IP address of the HTTP proxy server, and 3128 is a port.

Note: Any DHCP server can be used to configure DHCP options 43 and 60. The proxy server port is required to be set in the DHCP option 43. Only IPv4 addresses are supported for HTTP proxy IP addresses.
-
APs must be able to resolve FQDN for cloud servers (Meraki dashboard) using DNS server(s) configured (either via DHCP or manually). This means that the DNS traffic from the APs must be allowed through the HTTP proxy server and DNS responses must be allowed back to the APs.
-
HTTP CONNECT proxy is only supported for Meraki dashboard connectivity over IPv4. Dashboard connectivity over IPv6 and connection to HTTP server over IPv6 are not supported in MR 30.X firmware.
-
No authentication methods or hostname (FQDN) configurations are currently supported for HTTP CONNECT proxy configuration.
-
Confirmation the of AP’s proxy configuration is only available from the Local status page. There is no monitoring of this configuration available from the Meraki dashboard.
Services Supported Through HTTP CONNECT Proxy
Note: Meraki APs will only try to send traffic to the HTTP proxy server using the HTTP CONNECT proxy method if this traffic flows that fall within the scope of Dashboard services listed below. For example, if configured to use the HTTP CONNECT proxy, a Meraki AP will always try to communicate with the Meraki dashboard via a proxy server. Meraki APs will not try to send traffic flows outside of the Dashboard services listed below via an HTTP proxy server.
In addition, Meraki APs will not send local traffic (e.g., a communication between a Meraki AP and a local RADIUS server) to the HTTP proxy server. In this case, Meraki APs will always contact such local resources directly.
MR 30.X firmware supports the following services through HTTP CONNECT proxy:
Meraki Dashboard Connectivity
APs behind an HTTP proxy server can check into the Meraki dashboard and appear online on the Wireless > Monitor > Access points page.
Configuration Download
APs behind an HTTP proxy server can download the configuration, which is necessary for APs to get any configuration or backend changes from the Meraki dashboard.
Firmware Upgrades
APs behind an HTTP proxy server can download and update their firmware using the Meraki dashboard.
Deployment Considerations
Before placing APs into a network where an HTTP proxy server controls access to the Internet, APs must be upgraded to MR 30.1+ firmware. This is true for new out-of-the-box APs and already deployed APs running MR 29. X or older firmware.
Warning: After APs have been configured for HTTP proxy and deployed behind an HTTP proxy server, their firmware cannot be downgraded below MR 30.1. Since firmware versions below MR 30.1 do not support HTTP CONNECT proxy, downgrading the firmware will result in the loss of Meraki dashboard connectivity.
Therefore, the only way to restore the Meraki dashboard connectivity is to provide APs with unrestricted access to the Internet and allow them to upgrade the firmware to MR 30.1+. After the upgrade is complete. APs must be reconfigured to use the HTTP CONNECT proxy as described below.
Configuration
You can configure HTTP CONNECT Proxy on MRs in the following ways:
Auto Proxy Discovery via DHCPv4
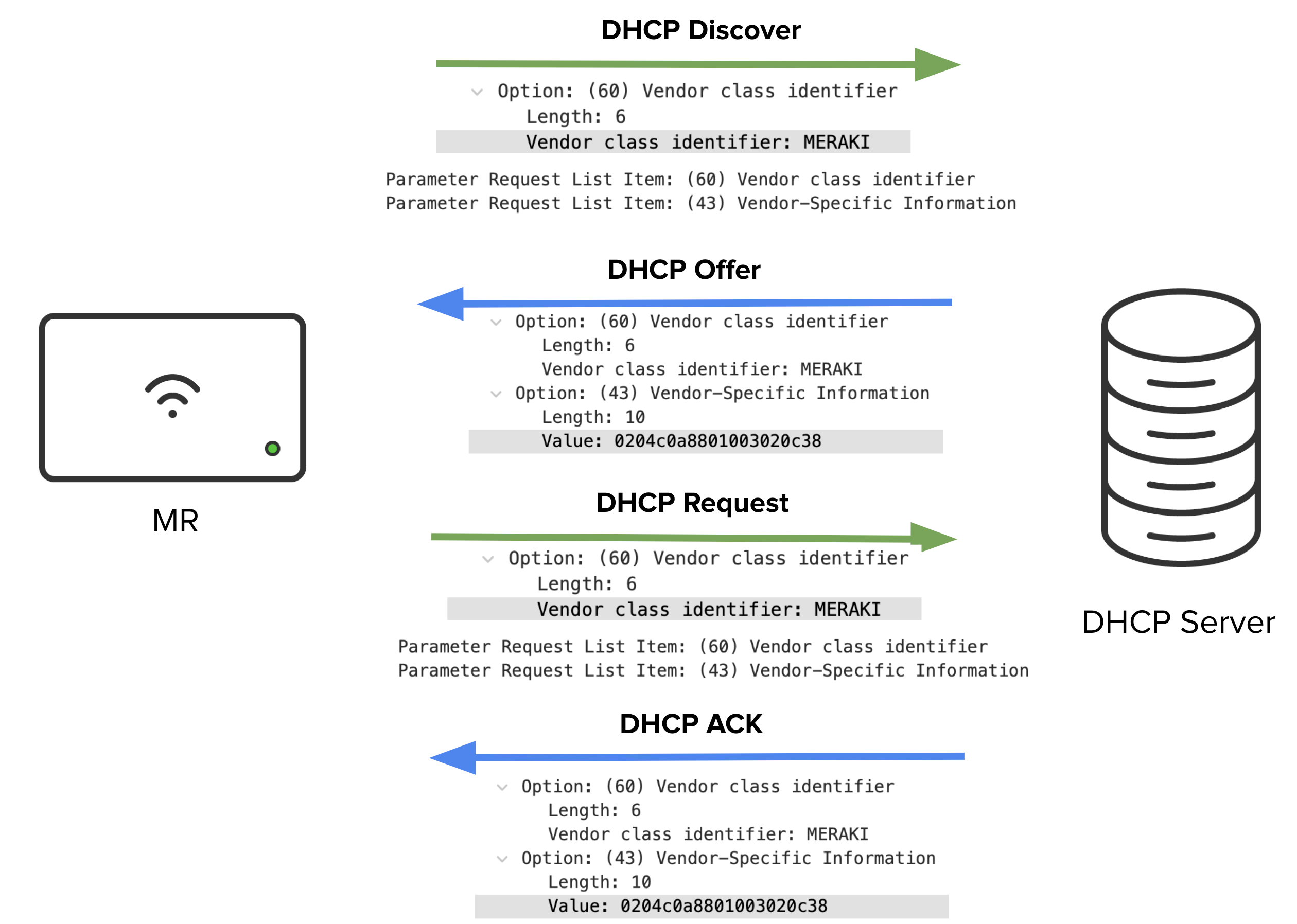
APs can acquire HTTP proxy IP address and port number as part of the DHCP process when requesting an IP address. In addition, an AP includes “MERAKI” specific Option 60 VCI (Vendor Class Identifier) when sending out a DHCP Discover.
When the DHCP server sees an already configured VCI in a DHCP Discover from a DHCP client, it returns the mapped vendor-specific information in its DHCP offer to the client as DHCP Option 43.
Note: Auto Proxy Discovery via DHCPv4 is a preferred option for configuring HTTP CONNECT proxy because it’s more scalable than configuring HTTP proxy info on the Local status page for each AP.
Local Status Page Configuration
You may also configure the HTTP CONNECT proxy directly on the Local status page of each AP by navigating to the Configure tab under the Web proxy section:

Please enter a valid IPv4 address and a port in the fields above. If either of the fields is left blank or has an invalid input, the “Use a proxy?” will revert to the previously configured setting,
Note: No authentication methods or hostname (FQDN) configurations are currently supported for HTTP CONNECT proxy.
HTTP CONNECT Proxy Configuration Priority Order
By default, APs listed in the Supported APs section and running MR 30.1+ firmware are configured for the Auto Proxy Discovery via DHCPv4. APs must be able to connect to the Meraki dashboard to upgrade to MR 30.1+ firmware and to download this setting as part of the configuration update. You can verify if an AP is set to support HTTP CONNECT proxy on the Local status page by confirming that the “Use a proxy?” is set to “From DHCP”.

The fields above are read-only and will be populated once an AP receives HTTP proxy server information (IP address and port) via DHCP Option 43.
If the default HTTP CONNECT proxy was changed to Custom and the IPv4 address and port are valid, the AP will only try connecting to the Meraki dashboard via the configured IPv4 address and port.

Warning: If an HTTP proxy server information is received via DHCP “Use a proxy?” - “From DHCP” or explicitly configured on the Local status page (Use a proxy?” - “Custom”) with valid IPv4 address and port , an AP will not try to connect to the Meraki dashboard directly, even if it’s unable to reach the HTTP server or the HTTP server is unable to forward AP’s traffic to the Meraki dashboard for any reason.
Please ensure that your proxy server settings (IPv4 address and port) are configured correctly on the DHCP server, no routing or filtering rules exist that could prevent the AP from reaching your proxy server, and that the proxy server is configured properly to rely the traffic from your APs to the Meraki dashboard.
Finally, if the “Use a proxy?” option is set to “No” the AP will not try to request proxy server information in the DHCP Discover message or connect to the Meraki dashboard via a proxy server.


