vMX Setup Guide for Alibaba Cloud
Overview
This document is a walk-through for setting up a virtual MX appliance in the Alibaba Cloud Marketplace. After completing the steps outlined in this document, you will have a virtual MX appliance running in Alibaba Cloud that serves as an Auto VPN termination point for physical MX devices.
Key Concepts
Before deploying a virtual MX, it is important to understand several key concepts.
Concentrator Mode
All MXs can be configured in either NAT or VPN concentrator mode. There are important considerations for both modes. For more detailed information on concentrator modes, click here.
One-Armed Concentrator
In this mode, the MX is configured with a single Ethernet connection to the upstream network. All traffic will be sent and received on this interface.
NAT Mode/Secure Cloud Gateway
In this mode, any traffic coming over to LAN port of the vMX will be NATed to the vMX's WAN IP as it egresses the vMX, while also maintiaining its ability to act as a hub for Site-to-Site and Client VPN.
As of MX 19.1, vMX will also support all other NAT Mode and Security features that you would find on a physical MX, enabling the vMX to act as a Secure Gateway for your cloud-hosted resources. Please look at vMX NAT Mode Use Cases and FAQ for more information.
Change in default behaviour
All new vMXens deployed post October, 31, 2022 will be deployed in Routed/NAT Mode Concentrator by default, existing vMX deployments will not be effected. If you wish to use the vMX in passthrough mode, please change the deployment settings to Passthrough or VPN Concentrator mode from the Security & SD-WAN > Configure > Addressing & VLANs page.
VPN Topology
There are several options available for the structure of the VPN deployment.
Split Tunnel
In this configuration, branches will only send traffic across the VPN if it is destined for a specific subnet that is being advertised by another MX in the same dashboard organization. The remaining traffic will be checked against other available routes, such as static LAN and third-party VPN routes, and if not matched will be NATed and sent out the branch MX unencrypted.
Full Tunnel
In full-tunnel mode, all traffic that the branch or remote office does not have another route to is sent to a VPN hub.
Alibaba Cloud Terminology
This document will make reference to several key Alibaba Cloud-specific terms and concepts.
Alibaba Cloud Elastic Compute Service (ECS)
A type of computing service that features elastic processing capabilities, it has a simpler and more efficient management mode than physical servers. You can resize disks and create, add, or release any number of ECS instances at any time to fit your business needs.
Alibaba Cloud Elastic IP
An Elastic IP address is a NAT IP address. It resides in the public network gateway of Alibaba Cloud and is mapped to the private network gateway of the bound ECS instance by NAT. It allows the ECS instance to communicate with the internet without exposing its IP address.
Alibaba Cloud Virtual Private Cloud (VPC)
An Alibaba Cloud virtual private cloud (VPC) is a private network built and customized based on Alibaba Cloud. Full logical isolation is achieved between Alibaba VPCs and users can create and manage cloud product instances such as ECS, intranet server load balancer, and RDS in their own VPCs.
VRouter
A networking hub in the VPC, the VRouter connects all VSwitches in the VPC and serves as a gateway device that connects the VPC to other networks. It forwards network traffic according to specific route entries.
VServer Group
A VServer group are back-end servers that can be customized and managed in the listener dimension. They allow listeners under a server load balancer (SLB) instance to distribute requests to different back-end servers depending on the configured forwarding rule.
VSwitch
A VSwitch is a basic device on the VPC network that can be connected to different cloud product instances. When creating a cloud product instance in a VPC network, you must specify a VSwitch for the cloud product instance.
Instance
An independent virtual machine that includes basic cloud computing components such as CPU, memory, operating system, bandwidth, disks, etc.
Instance ID
The Instance ID is for the instances you have purchased and can be viewed on the console. ApsaraDB for Redis limits connection quantities, bandwidth, CPU specifications, and other aspects based on capacity specifications of individual corresponding instances.
Additional Information
Please refer to the Alibaba Cloud glossary for cloud terminology on the Alibaba Cloud Platform.
Meraki Dashboard Configuration
Begin by creating a new Security Appliance network in your organization. This guide will walk you through creating a new network in the Meraki dashboard.
1. Adding license(s) to the Meraki dashboard.
The Meraki dashboard will require a vMX license to be added before you are able to continue. If you do not have access to a vMX license, please reach out to your Meraki reseller or sales representative.
Create a "Security Appliance" network type:

Once you have created the "Security Appliance" network and added the appropriate license, you will be able to deploy a new vMX to your network by clicking on the 'Add vMX' button.

Before generating the token, please verify the firmware is running MX 15.37+. If the vMX network is upgraded to anything below that, the upgrade will not occur.
2. Generate the authentication token.
After you add the new vMX to your network, navigate to Security & SD-WAN > Monitor > Appliance status and select “Generate authentication token” to generate the token for the Alibaba Cloud user-data field.

3. Copy the newly generated token and save it.
The newly generated token will be used in the "System Configurations" section when creating a new Alibaba Cloud instance.
The authentication token must be entered into the Alibaba Cloud instance within one hour of generating it. If it has been more than one hour, a new token must be generated.
Alibaba Cloud Setup
This section walks you through configuring the necessary requirements within Alibaba Cloud, and adding a vMX instance to your virtual private cloud (VPC). For more details on setting up a VPC and other components, please refer to Alibaba's Cloud Documentation here.
Before You Begin
You must have the following before you begin:
- Alibaba Cloud virtual private network. To find more information about this, please click here.

Accessing the Offer
To gain access to the VM offer, please access this link. A screenshot of the Marketplace list of Cisco Meraki vMX in Alibaba Cloud is included below:

Configuring the ECS
After continuing, you will be prompted to configure the ECS instance settings.

1. Select "Pay-As-You-Go."
2. Select the desired region and zone.
Country deployment limitations
If the vMX image is deployed from the Alibaba Cloud International Marketplace, then the vMX will have access to all regions (including China).
If the vMX image is deployed from the Alibaba China Marketplace, then the vMX will be limited to regions in China.
3. Select "Compute Optimized."
4. Select the desired instance type (ecs.c5/c6.x/large).
5. Select the vMX image from the Marketplace image and click "Next: Networking."

6. Select the VPC.

7. If you wish to assign a public IP, check "Assign Public IP Address."

8. If you wish to gain access to the local status page, allow ports 80/443 in a security group.

9. Select the desired ENI and click "Next: System Configurations."

10. Scroll down to "Advanced" and paste the token.

11. Finally, click "Preview" and "Create Instance."

Troubleshooting
The most common problem people face when deploying a vMX is getting it provisioned and online in their Meraki dashboard in the first place. New troubleshooting/diagnosis messages have been added to the vMX console screen, so you can identify what went wrong during the provisioning process.
When the vMX boots, it will execute the following steps during its initial provisioning process:
- Obtain user-data (vMX auth token).
- Authenticate with the dashboard (using auth token).
- Connect to dashboard.
Obtain User Data and Authenticate to Dashboard
Once a vMX has successfully connected to a network, it will then attempt to obtain its user data (vMX auth token). There are different user-data mechanisms in each platform that the vMX currently runs on to provide the token to the vMX. In AWS, Azure, GCP, and Alicloud there are user-data fields in the VM configuration where this can be provided.
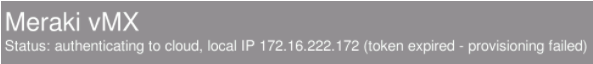
Token Expired
vMX auth tokens have a lifetime of only one hour for security purposes. If you see the following message on your vMX console, it means the token you provided is no longer valid.
Invalid Token
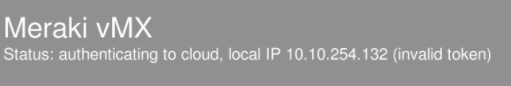
If the token provided is incorrect in any way, the "invalid token" message is displayed on the console.
Unable to Reach Meraki Dashboard
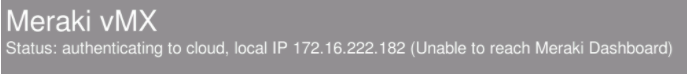
If the vMX is unable to reach the dashboard on TCP port 7734, the initial provisioning phase will fail and an "Unable to reach Meraki dashboard" message will be displayed on the console (check the firewall information page for a list of all the firewall rules needed for Cisco Meraki cloud communication). Please refer to this document on the correct ports/IPss that need to be opened for Meraki dashboard communication.
No "Add vMX" Button
When navigating to Security & SD-WAN > Monitor > Appliance Status, if there is no "Add vMX" button, please ensure the following two conditions are met:
- You have available vMX licenses in your license pool.
- You have created a "Security Appliance" network type.
Please note that Meraki Support does not troubleshoot Alibaba Cloud-specific firewall rules and deployments.

