Containerization with Systems Manager
Overview
A critical component of device management, especially in an era where the line between personal and work devices continues to blur, is containerization. This refers to the separation of work and personal data on devices, for example in BYOD environments where users require email or wireless configurations on their personal phones.
Management and security at this point becomes a key question - how can IT push settings or applications to a device that is not organizationally owned, and have the security of remotely wiping sensitive information on a BYOD device, or keeping personal applications from accessing work data? From the other perspective, how can an end-user experience the convenience of having settings and apps automatically installed, while having the peace of mind knowing that their employer isn't able to access or wipe personal data?
Systems Manager implements native containerization. These are the latest technologies Android and iOS have built into their core operating systems to separate work and personal data, meaning there is no need for proprietary SDKs or APIs to work around when managing apps. This means that applications managed through Systems Manager, in the apps page, will automatically be separated from personal apps on end users' devices.
The result of this native containerization is greater data security and control. On both iOS and Android platforms, personal apps can communicate with each other, and work apps can communicate with each other, but work and personal apps cannot communicate between containers.
Systems Manager has explicit control over the work container and can remotely wipe, modify and control apps and settings within the container. Additionally, devices that are unenrolled and removed from Systems Manager have their configuration profiles and apps removed.
Android Containerization
Android Enterprise (Android for Work) BYOD deployments enrolled with a work profile will automatically create a work container upon enrollment, and mark all work apps with a small orange briefcase.
![]()
Apps within the work container are fully controlled by Systems Manager. They can be installed, uninstalled and have managed app configurations pushed to them. In addition, administrators can block copy-pasting between containers. This will reduce the likelihood of sensitive information being shared outside of the work container.
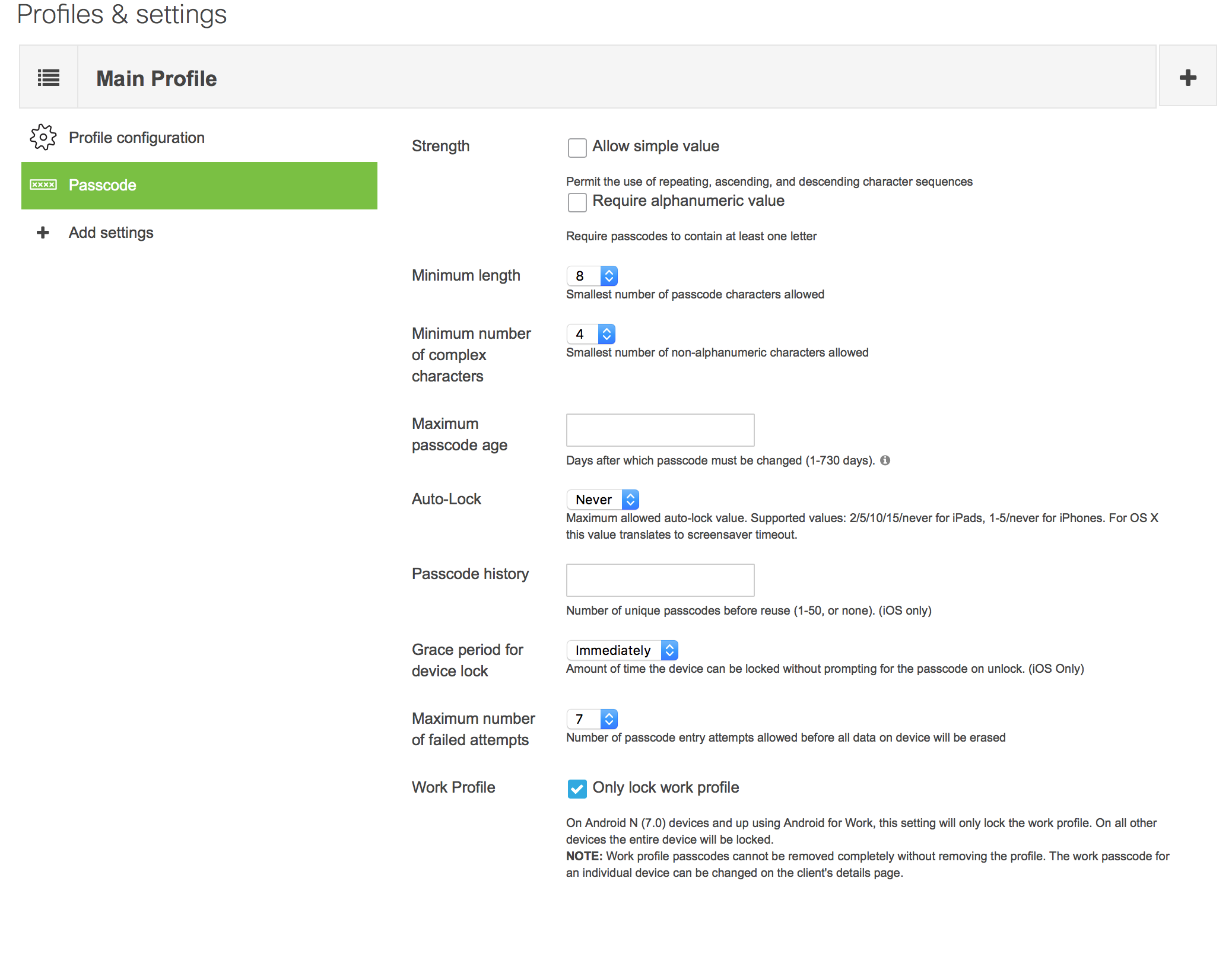
A base requirement for Android Enterprise (Android for Work) is encryption. This encryption applies to the entire device, which includes the work container. Configuration profiles can be used to set a passcode on the work container so that sensitive data within the work container is passcode protected. Systems manager can remotely reset or clear this password if the end user ends up forgetting the password.
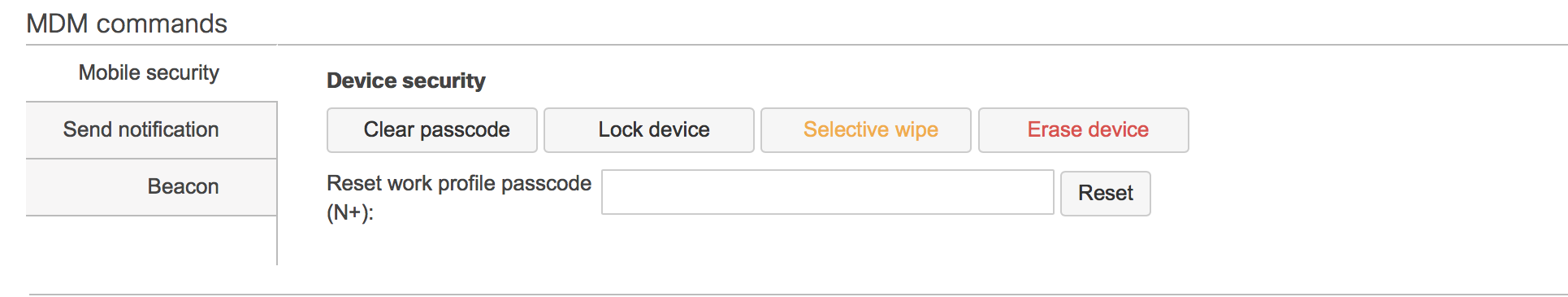
The Android for Work work profile enables administrators to perform the following within the work profile container:
- Enforce settings and app restrictions
- Create, modify, and remove data contained within the container
- Push and install apps in the work profile
- Install certificates
- Remotely wipe the container
- Reset, Clear and modify the password on the work profile
- Push app specific payloads
For more information on Work Profiles, Google has a Help Article.
iOS Containerization
iOS devices using Systems Manager implement Apple's Managed Open-In policy, which covers all managed apps. Managed Open-In divides the device into two containers, one for managed work apps and one for personal apps. The containerization built into the core of iOS allows for the user to maintain the same look and feel of iOS while seamlessly enabling administrators to effectively manage sensitive data. The iOS experience looks and feels identical to the end user while allowing for powerful control over managed apps.
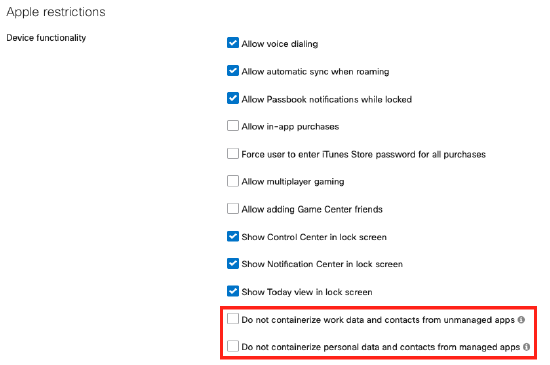
Systems manager can push Managed Apps to enrolled iOS devices. Once those managed apps are installed on the device, administrators can leverage configuration profiles to exert control over the device and the managed apps. Systems Manager can push a profile that disallows work data and contacts from managed apps from being opened in unmanaged apps. A common use case would be to ensure that users aren't adding sensitive documents and attachments to personal email or personal sharing services such as Google Drive or Dropbox. This can be configured on Dashboard by going to Systems Manager > Manage > Settings and can be found in the Restrictions payload.
The entire iOS device, including the work container, can be encrypted easily by using MDM to require a passcode. Once a passcode is set, iOS natively encrypts the device. You can use Systems Manager to set password requirements such as requiring a complex password that has never been used before.
Related Settings
Systems Manager allows you to control the following settings related to containerization.
iOS
- Do not containerize work data and contacts from unmanaged apps (iOS 7+)
- Do not containerize personal data and contacts from managed apps (iOS 7+)
- Disallow sharing of managed documents with AirDrop (iOS 9+)
- Allow managed app to store data in iCloud
- Allow screen capture
Android
- Prevent cross profile copy and paste
- Only lock work profile

