Troubleshooting Security Policies in Systems Manager
Security policies in Systems Manager (SM) networks can be used to monitor a number of security-related data points on enrolled client devices. Compliance information can then be used to generate scheduled reports or control deployment of apps and profiles to clients through the use of automatically generated security dynamic tags. For more information on the purpose of a Security Policy and how to set one up, please review our document on 'Security Policies in Systems Manager'.
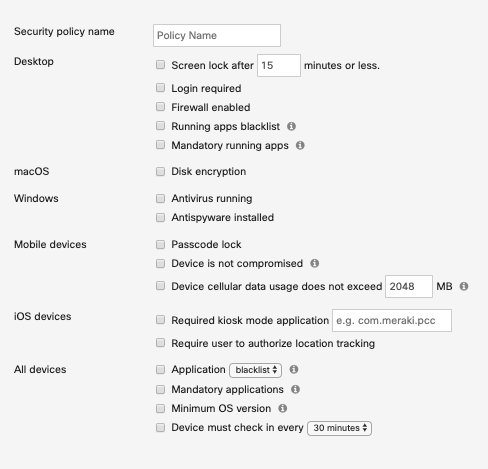
As of 1/28/2020 this is the list of Security Policies.
On macOS and Windows: Security Policies refresh about once every 6 hours. On Android and iOS it will be much faster should happen within 1 hour. All devices need to be online to communicate this information into Meraki Dashboard, of course.
Desktop
The "Desktop" security policies are supported on macOS and Windows. The Meraki SM agent is required to detect the device compliance, always ensure that the device is checking in correctly via the agent (not just via MDM profile) so these policies can be reported correctly from the SM Agent. A ist of Security Policies and their functions are detailed below:
Screen lock after '__' minutes or less
macOS:
As of macOS Mojave 10.14+, detecting screen lock delay is no longer supported.
Windows:
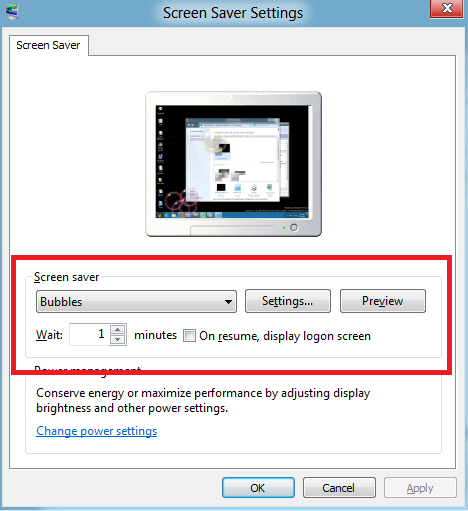
If screensaver timeout "wait" time is less than the SM security policy time value, the policy is compliant
Login required
macOS:
System Preferences > Users & Groups > Login Options > Automatic Login.
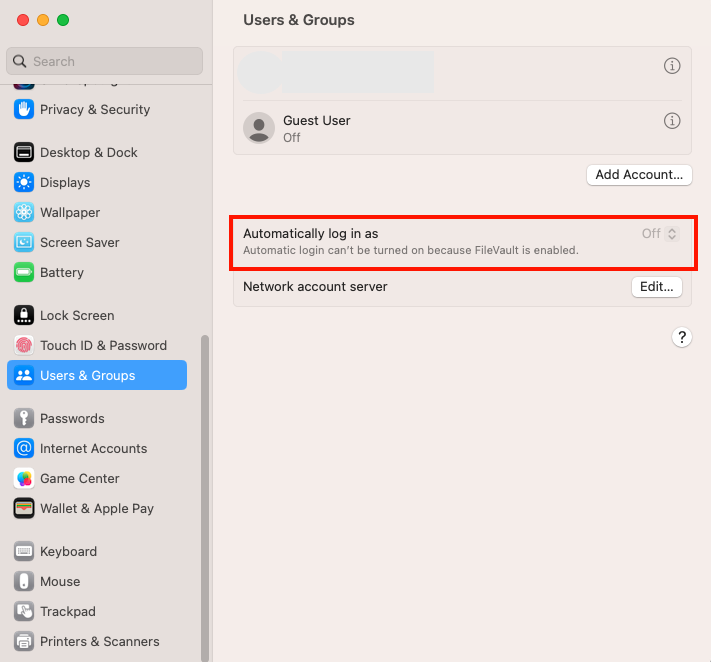
If Automatic Login is set to "Off" the security policy is compliant.
This is checked with the following command:
sysadminctl -autologin status 2
Windows:
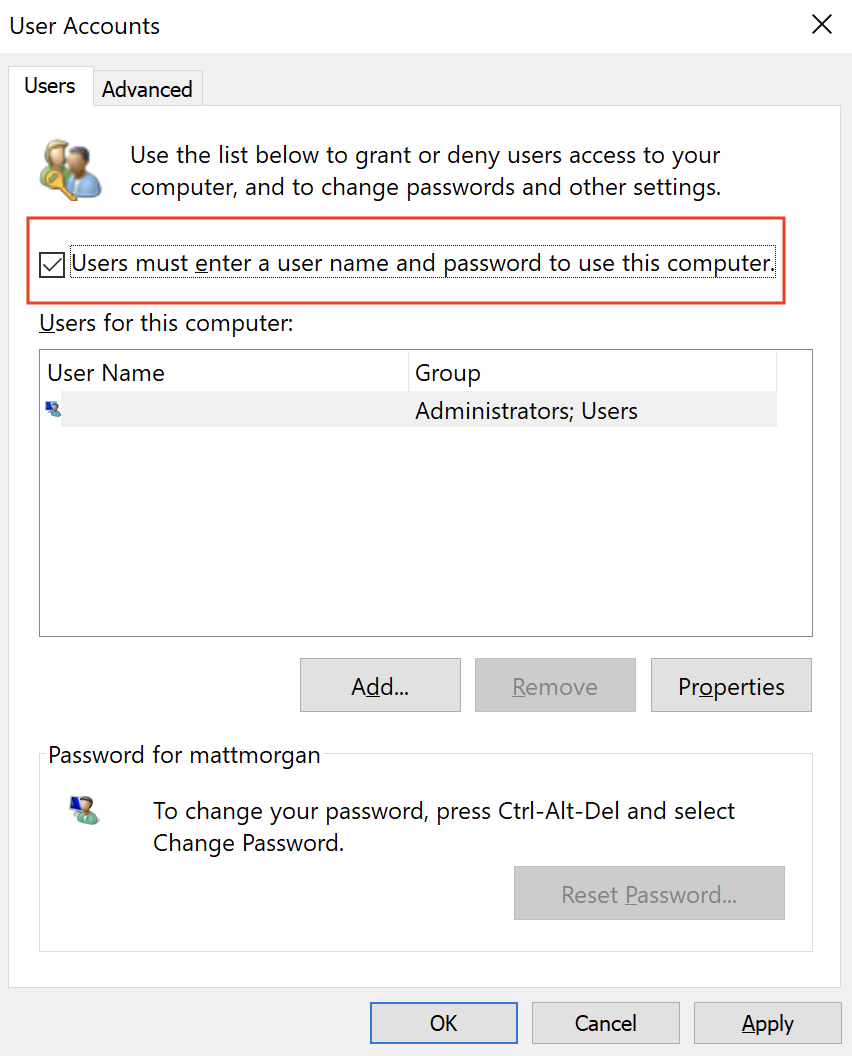
If "Users must enter a user name as password" is checked the security policy is compliant.
Firewall enabled
macOS:
System Preferences > Security & Privacy > Firewall.
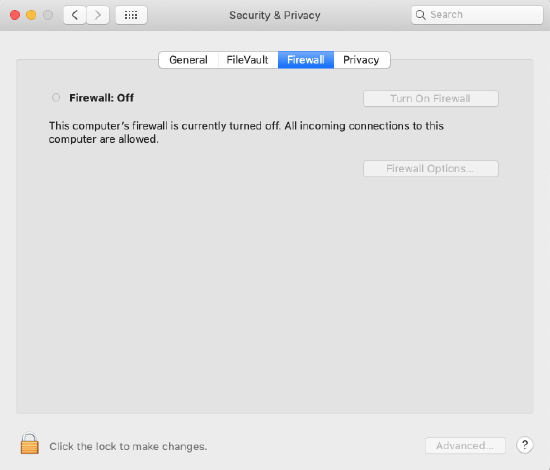
If Firewall is enabled, the security policy is compliant.
This is checked with the follow command:
defaults read /Library/Preferences/com.apple.alf globalstate
0 = Firewall OFF
1 = Firewall ON
Windows:
netsh advfirewall show allprofiles state
Running apps blocked
macOS: To see running application run top -o cpu -s 2 -i 5 from Terminal or open Activity Monitor.app and look in the CPU tab.
Windows: Open Task Manager (control+alt+delete) and open the Processes tab.
Mandatory running apps
macOS: To see running application run top -o cpu -s 2 -i 5 from Terminal or open Activity Monitor.app and look in the CPU tab.
Windows: Open Task Manager (control+alt+delete) and open the Processes tab.
macOS
Disk encryption
Detects if disk encryption (FileVault) is enabled on macOS. FileVault can be enabled locally in System Preferences > Security & Privacy > FileVault. It can also be forced to be enabled with a MDM profile in Systems Manager.
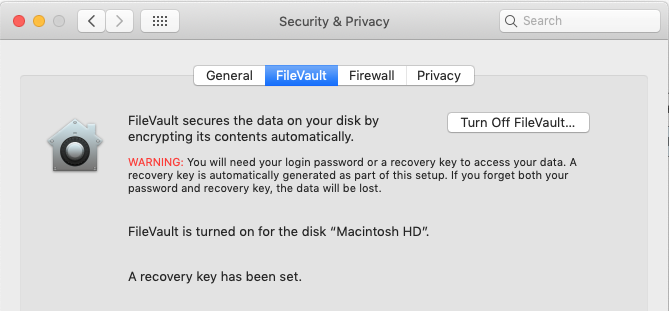
If Filevault is enabled, the security policy is compliant.
Windows
Antivirus running
The following commands are run on Windows to check for AntiVirus:
Get-WmiObject -query "Select * from AntiVirusProduct" -Namespace "root\SecurityCenter" Get-WmiObject -query "Select * from AntiVirusProduct" -Namespace "root\SecurityCenter2"
Antispyware installed
The following commands are run on Windows to check for Antispyware:
Get-WmiObject -query "Select * from AntiSpywareProduct" -Namespace "root\SecurityCenter" Get-WmiObject -query "Select * from AntiSpywareProduct" -Namespace "root\SecurityCenter2"
Mobile Devices (iOS and Android)
SM app installed is recommended. While troubleshooting iOS and Android security policies, it is always good practice to launch the SM app and have the device perform a check-in from the app.
Passcode lock
With this policy enforced, the device must have a passcode set on device to be compliant. You can confirm there is a passcode set by locking and then trying to unlock the device manually -- if you are forced to type a passcode (or touch ID, FaceID, etc) then the device has a passcode. You can also confirm the passcode is enabled by checking the device's local Settings.
iOS: Settings > TouchID/FaceID & Passcode
Android: Settings > Security > Passcode (this will change depending on Android OS and device)
Device is not compromised
With this policy enforced, the device must have a be jailbroken (iOS) or rooted (Android). If the device is not jailbroken/rooted, the device will be compliant with this policy.
Device cellular data does not exceed __ mb
Cellular data usage allowances are reset on the 1st day of the month. This data allowance reset day can be customized in the Systems manager > Configure > General. The SM app must be installed on devices to report this correctly. If a device goes over the security policy defined megabyte allocation, then the device will be failing this policy.
iOS
Required kiosk mode application bundle ID
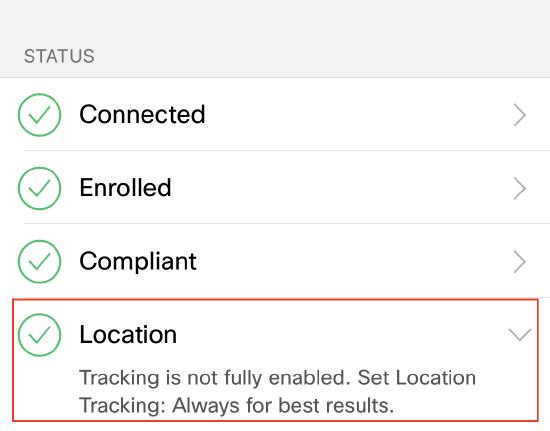
Require user to authorize location tracking
This one requires the SM app to be installed and running. On iOS, launch the iOS app. If Location does not have a green check (location tracking set to Always) the device will be failing this policy.
All Devices
Application block/allow list
The device will be checked if it has or does not have an application. To see a device's currently reported installed application list go to Systems Manager > Devices and click on a single device to view the Apps section. If the device does not have an application installed from the security policy allow list it will fail the security policy. If the device has an application installed that is on the block list it will fail the security policy.
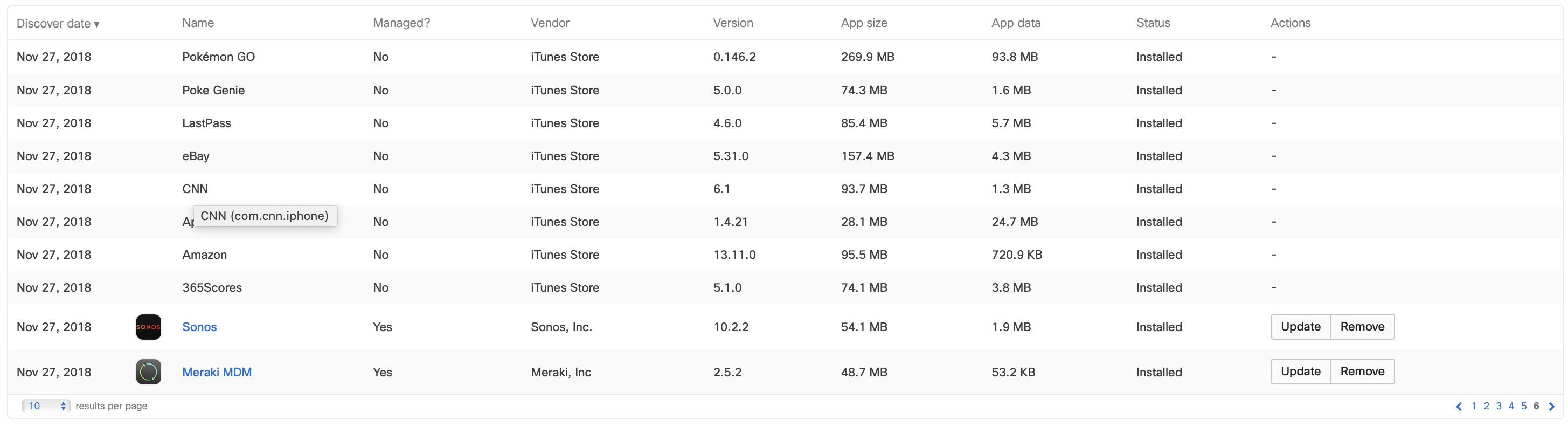
Note: Hover over an application in the device's installed App list to reveal its unique app identifier.
Note: Wildcard matches can be made with a '*'. (e.g. com.mer*, *meraki*, and *.sm would all match com.meraki.sm)
Mandatory installed applications
The device must have a certain list of applications installed. To see a device's currently reported installed application list go to Systems Manager > Devices and click on a single device to view the Apps section. This device must have all of the applications from the security policy to be compliant with the security policy.

Note: Hover over an application in the device's installed App list to reveal its unique app identifier.
Note: Wildcard matches can be made with a '*'. (e.g. com.mer*, *meraki*, and *.sm would all match com.meraki.sm)
Minimum OS version
The device must have a certain OS version to be compliant with this security policy. To see a device's currently reported OS version go to Systems Manager > Devices and click on a single device to view the OS section. There should be a field called "Version". This reported "Version" needs to match the security policy requirements to be compliant with the security policy.
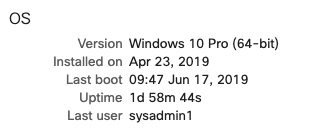
Device must check-in every __ minutes
To see a device's last MDM check-in timestamp, go to Systems Manager > Devices and click on a single device to view the "Last MDM check-in" field. The device must have performed a MDM check-in within the set time frame to be compliant with this security policy.