Configuring EAP-TLS Wireless Authentication with Systems Manager Sentry Wifi
Click 日本語 for Japanese
Systems Manager Sentry Wi-Fi security provides automatic certificate-based EAP-TLS configuration in just a few clicks, eliminating the need for the use of a certificate authority (CA) and the additional management required for each device and user.
We cannot simultaneously support third-party-signed SCEP CA certs and Sentry Wifi. This means third-party-signed SCEP CA certs are not compatible with Sentry Authentication.
This article outlines how to integrate SM Sentry with Cisco Meraki MR access points for EAP-TLS wireless authentication.
Use Case
Commonly, network administrators want to configure different settings for corporate owned devices, employee owned devices, and guests. Each group of users will likely have their own separate SSID, with an additional SSID for onboarding:
|
SSID |
Use Case |
Default SSID Policy |
|
Corp |
Corporate-owned devices only |
Full access on Corporate VLAN |
|
BYOD |
Employee-owned devices |
Limited Corporate access Some apps optionally limited Higher bandwidth than Guest |
|
Guest |
All others |
Filtered Internet Rate limit No corporate devices |
|
Corp-onboarding |
Onboarding to Corp network only |
Restricted to onboarding |
Configuring EAP-TLS using Systems Manager Sentry WiFi Security
The following instructions explain how to apply EAP-TLS wireless access to corporate-owned devices tagged as "Corp" in our example Systems Manager network.
- In Dashboard, navigate to Wireless > Configure > SSID and enable/name each SSID.
The example image below shows four SSIDs: SL-corp, SL-byod, SL-guest and SL-corp-onboarding:
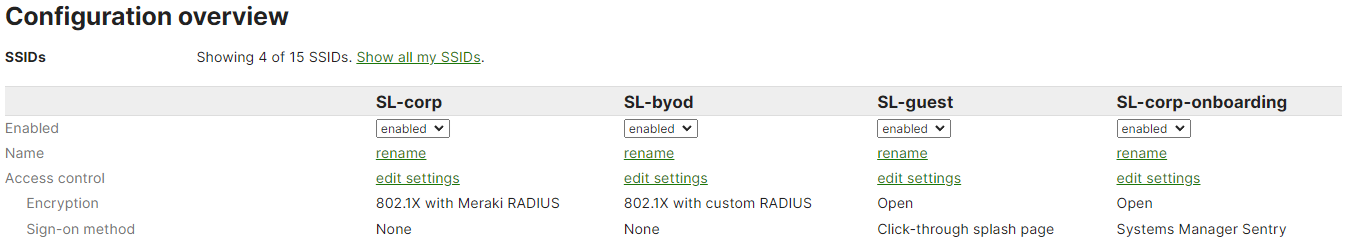
- Navigate to Wireless > Configure > Access Control:

- Select the device tags to be associated with EAP-TLS. This automatically creates a Systems Manager profile for the SL-corp SSID to use EAP-TLS and installs a client certificate from the Dashboard for each client (this profile will appear under Systems Manager > Manage > Settings). Note that wireless authentication settings should be provisioned from either the SSID side, as described in this article, or the MDM profile side in Systems Manager > Manage > Settings and not both.

- Click Save Changes. EAP-TLS is now configured for all devices tagged corp in Systems Manager.

Sentry WiFi Device Operating System Compatibility
| Operating System | Sentry WiFi Supported |
| iOS | Yes |
| macOS | Yes |
| tvOS | Yes |
| Windows 10/11 |
Yes1 |
| Android |
Yes2 |
|
Samsung Knox 3.0+ |
Yes3 |
| Chrome OS | No |
1. Local user accounts only. In a multi-user environment on a single device the Sentry WiFi profile will only function successful for a single user. Users must be logged in to associate to Sentry WiFi SSID.
2. A passcode is required on the device while in Knox mode.
Certificate-based WiFi authentication with Systems Manager and Meraki APs