Cisco Secure Connect - Admin User Management
Cisco Secure Connect is delivered via capabilities based on both Cisco Meraki and Cisco Umbrella dashboards. The goal of the account creation between dashboards is to create one unified experience between Secure Connect ( Meraki ) and Umbrella dashboard.
Using the same email account between Meraki and Umbrella for admin users while provisioning will enable logged-in Secure Connect users to automatically be logged into the Umbrella dashboard when clicking on any Umbrella link, regardless of whether they've manually logged into Umbrella. To learn more, read the Sign-on Once section below.
Secure Connect will automatically provision Umbrella admin users, and update their access levels, via the Admin Sync capability. To learn more, read the Admin Sync section below.
When you create an account, only one admin is created during the initial onboarding process. If you need to add more admins, you must follow the process below to gain access to the dashboard.
SAML admins may take up to an hour to sync fully. They can only access resources such as policies from the Secure Connect Dashboard once the SAML users are synced.
Manage Admin Users
All permissions for a dashboard organization can be managed under Organization > Administrators, however, this page is only visible to users with full or read-only organization access. Changes on this page can only be made by users with full organization access.
- More details for Meraki account creation can be found here: Managing Administrators Access
Meraki - Add an Organization Admin
- Navigate to Organization > Administrators
- Click Add admin along the right side of the page.

- Enter the admin's Name and the Email (use the same email as Umbrella account creation below ) they will use to log in.
- Choose a level of Organization Access as defined in the Organization Permission Types section within this doc.
- Click Create admin.

- An email will be sent to the email address entered and instructing the user how to log in.
- Click Save changes.
Umbrella - Add a New Account
Note: Admin Sync ensures that all users are created with matching permissions in Umbrella.
Normally, you do not need to manually add users to Umbrella.
- Navigate to Admin > Accounts and click New.
- Enter the new user's email address (use the same email as Meraki account creation above) and select a user role, then click Send Invitation.

Note: The user role you select controls the level of access an account has to your Umbrella dashboard. To learn more, see Manage User Roles.
- A message is sent to the new user's email address with instructions for setting a password. The account status is Pending until they create a password and log into their account. Afterward, the status becomes Active.
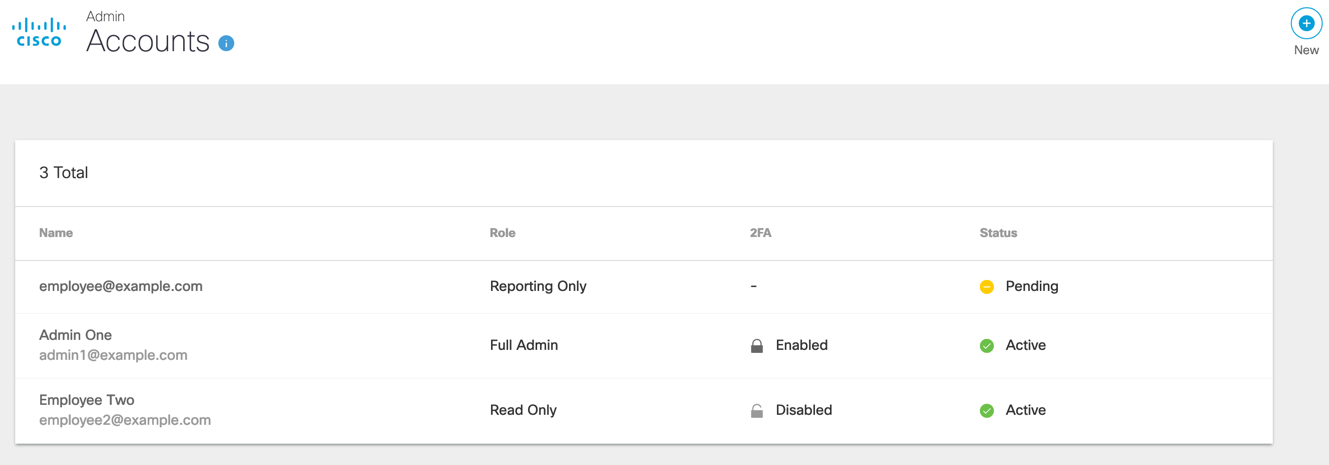
The new user now has access to your Umbrella dashboard. Their user role controls their level of access.
For more details on Umbrella account creation: Umbrella account creation
Sign-On Once
This enables logged-in Secure Connect users to automatically be logged-in to the Umbrella dashboard when clicking on any Umbrella link, regardless of whether they've manually logged-in to Umbrella.
Requirements:
- API Integration to provision Secure Connect has been completed.
- Admin user has the same email address in Meraki and Umbrella (see Admin Sync below).
- The Admin User logs into the Secure Connect ( Meraki ) dashboard directly, before accessing any Umbrella pages.
There are no additional configurations required to use this capability.
For Secure Connect Admin Sync to successfully sync Meraki SAML admins with Umbrella, the IdP used for Meraki SAML admin login must pass an email address as the username attribute to dashboard.
How it works:
- In Secure Connect, there is a link to an Umbrella page (note the icon:
 )
)

- When a user clicks a link (
 ) they will be automatically logged into the Secure Connect enabled org in Umbrella, and routed to the relevant page
) they will be automatically logged into the Secure Connect enabled org in Umbrella, and routed to the relevant page
- There will be a link to Secure Connect support visible at all times.
- There will be a link to the last Secure Connect (Meraki) page visible at all times.

Admin Sync
The admin sync feature automatically syncs new and existing Secure Connect admin users and permissions from Secure Connect ( Meraki ) to Umbrella. This ensures that admin user accounts in both Secure Connect ( Meraki ) and Umbrella dashboards in order to seamlessly navigate between them; this also attributes changes made in the Secure Connect dashboard to the individual user, rather than the organization.
We ensure that all admin users have the same email configured on the Umbrella side with admin sync.
How it works:
- Admin users only need to be created once, and from the Secure Connect ( Meraki ) dashboard.
- Sync is one-way Secure Connect ( Meraki ) -> Umbrella.
- Sync includes add user, update user or permission, and delete user.
- New Admins added to (or updated in) Umbrella will not sync to Secure Connect ( Meraki ) yet.
Note: Secure Connect Admins must have org-level permissions (read or write).
- If an admin's email attempting to be synced already exists in Umbrella, the admin's account will be updated matching Meraki permissions.
- Example: Admin-A was a read-only user existing in Umbrella. If Admin-A is added as a full-access admin in Secure Connect ( Meraki ) , they will become a full access admin in the Secure Connect enabled Umbrella org.
Note: Admin who has generated API Keys will not be deleted/updated by Admin Sync to preserve API Keys.
-
Example: Admin-A is the one who generated Umbrella API keys during the integration procedure. Admin-A left the company and their record is deleted from the Secure Connect ( Meraki ) side; there are still connections between Admin-A and Umbrella API keys. In this case, the new administrator Admin B should re-generate API keys, remove Admin A directly from Umbrella, and re-do the integration under Secure Connect -> Umbrella API keys section.
Admin User Experience FAQ
Does Secure Connect work with Single Sign On (SSO)?
When you have connected a Meraki org to an Umbrella org, SSO will work once configured. SSO should be configured in the Meraki dashboard, not Umbrella.
Note: An admin cannot have the same email used in SSO and as a named user. An admin user (with the same email) can either:
- Have SSO to access all Meraki organizations
- Have named-user access to all Meraki organizations
What happens when an admin logs into Secure Connect (Meraki) directly?
They will have full access to all Secure Connect features. Cross-launches to Umbrella pages will:
- Automatically log them in
- Point them to the appropriate (mapped) org
- Enable a return to the page from which they cross-launched
How are changes logged with Admin Sync?
All changes to Secure Connect appear in the Meraki Organization change log. Logs take about 5min to sync from Umbrella to Meraki. Some changes are made via the integrated Umbrella cloud security, and these are attributed using one of two methods:
- Changes made by the API key - attributed to the user who created the API key.
- Changes made by the Admin user - attributed to the user who has logged into Meraki Dashboard.
All changes made directly on Umbrella pages are attributed to the user who is logged into the Umbrella dashboard.
Note: Umbrella maintains its own changelog, and the name reflected in each platform will match the user's name in that platform. Typically they will be the same due to Admin Sync, but can differ if the name is changed directly in the Umbrella platform.
- Meraki Changelog shows Meraki Name
- Umbrella Changelog shows Umbrella Name


Changes made to the following pages will be logged as follows:
| Page | Logging Method |
|
Applications |
User who created the API key |
|
Browser Access |
User who created the API key |
| Remote VPN Access | User who has logged into Meraki Dashboard |
|
Endpoint Posture |
User who has logged into Meraki Dashboard |
|
Cloud Firewall |
IPS: User who created the API key FW Rule: User who has logged into Meraki Dashboard |
|
API Keys |
User who created the API key |
| Admin Sync |
User Added: User who has logged into Meraki Dashboard User Synced: Management API |
What happens when an admin logs into Umbrella directly?
They will be prompted to login to the Secure Connect dashboard, but can access a subset of Secure Connect capabilities.
The following capabilities are configured in the Secure Connect Dashboard:
- Browser access policy
- Endpoint posture profile for browser access policy
- SD-WAN monitoring and management
Why are some pages are spinning endlessly?
When a new organization is created, and/or a new admin user has been added to the Meraki Administrators page, there can be a delay before the admin user is synced to the Umbrella dashboard. Wait a few minutes, or contact support if the issue persists for more that 5min.
How does Enterprise Admin work with Secure Connect?
An admin user with Enterprise Admin permissions will not see Secure Connect in their left navigation; and will not automatically sync via Admin Sync as described above.
Admins with this permission level can see the Secure Connect regions (shown as Hubs) and their status from the VPN Status page, the Site-to-site VPN page, and the Organization overview page. Their permissions on these pages are documented here.

