Blocking and Allowing Clients
In some cases, it is necessary to allow list or block a specific client on a Cisco Meraki Network. This configuration is completed on a client-by-client basis and will affect the client immediately.
Allow listing and Blocking can be done on both the Cisco Meraki WAN appliances and access points. At this time, it is not possible to add a client to the allow list or block list on a Cisco Meraki switch.
Client policies are configured on a device once it is listed in the network client list. It is possible to Pre-Configure the network policy for clients that aren't listed.
Built-in Client Policies
There are two built-in policies that can be configured for a client—allow list and blocked. Normal is the default setting for every client, subjecting the client to all of the network-wide settings. If configured, group policies can also be applied to the client in the same manner as detailed below.
Allow List
Applies the following settings to a client:
- Is exempt from all firewall rules, both Layer 3 and Layer 7 (Applies to both the MX Security Appliance and the MR Access Points)
- Bypasses AMP
- Bypasses a Click-through splash page
- Bypasses a Billing (paid access) splash page and access the network on an SSID without paying or authenticating
- Bypasses a Sign-on splash page without authenticating (applies to both the MX Security Appliance and the MR Access Points)
- Is exempt from Per-client bandwidth limit (applies to both the MX Security Appliance and the MR Access Points)
- Is exempt from Traffic shaping rules (applies to both the MX Security Appliance and the MR Access Points)
- Bypasses Content filtering on MX Security Appliance
- Restricted Youtube content will NOT be bypassed by allow listed clients as it is NOT considered part of Content Filtering.
- IDS/IPS under Security & SD-WAN > Configure > Threat Protection will NOT be bypassed.
Note: The device is still subject to association requirements and per-SSID bandwidth limits on MR access points, as well as Uplink Configuration and Security Filtering on a MX security appliances. RADIUS attributes that would assign a bandwidth limit to a client, such as Filter-ID (via a Group Policy) or Maximum-Data-Rate-Upstream / Maximum-Data-Rate-Downstream, are considered before any dashboard assigned configuration and a device would still be subject to these bandwidth limits if allow listed. Limits applied with the Maximum-Data-Rate-Upstream or Maximum-Data-Rate-Downstream TLVs can be viewed under the Wireless > Monitor > Splash logins page.
Note: If a device is allow listed in a network that is bound to a template, that client will be allow listed on all other networks bound to that template. Conversely, if the client is removed from the allow list on one bound network, it will also be removed from the allow list on all others.
Site-to-Site VPN Firewall Rules Behavior when Group Policy is Configured
- If Site-to-Site VPN Outbound Firewall Rule allows and Group Policy L3 denies, traffic will be denied.
- If Site-to-Site VPN Outbound Firewall Rule denies and Group Policy L3 allows, traffic will be denied.
- If Site-to-Site VPN Outbound Firewall Rule denies and Group Policy allow-listed preset is configured, traffic will be denied.
Block
Applies the following settings to a client:
- Firewall rule applied to block all communication with other devices on the Network (only applies to traffic that traverses the Cisco Meraki device that has the block is configured)
- Blocked Splash Page will be displayed when user tries to load a web page
Note: The device will still receive an IP address and will be able to resolve DNS names.
Note: The EAP exchange will still be allowed for wireless clients, and devices will be able to associate with an SSID. The block will apply to client traffic after the 4-way handshake is completed.
Blocking or Allow listing a Client
There are two ways to allow list or block a client on the Cisco Meraki dashboard.
Placing a client on the "Block list" will block both LAN and Internet traffic.
Note: There is a limit of 3000 clients for allow listing and 3000 clients for blocking. An error will appear when attempting to allow list or block more than 3000 clients.
Using the Clients List
Navigate to Network-wide > Monitor > Clients, then check the boxes of the clients that you want to allow list or block. Click on the Policy drop down above the client list, and select blocked or allow listed. To apply the allow list or block on a per-SSID basis or only on the MX security appliance, select Different policies by connection and SSID. To clear the setting, remove the block list or allow list policy and select normal.
If utilizing splash message when applying block, the message must be limited to one paragraph.
Note: The single configuration pane to block and allow list users on the security appliance and the SSIDs is only available when on a combined network. These settings would have to be completed on each dashboard network for uncombined networks.
Note: Security appliance policies applied for clients connected to a SSID with Meraki DHCP will not have effect, as the client mac and ip address will get NATed at the MR before reaching the Security appliance.
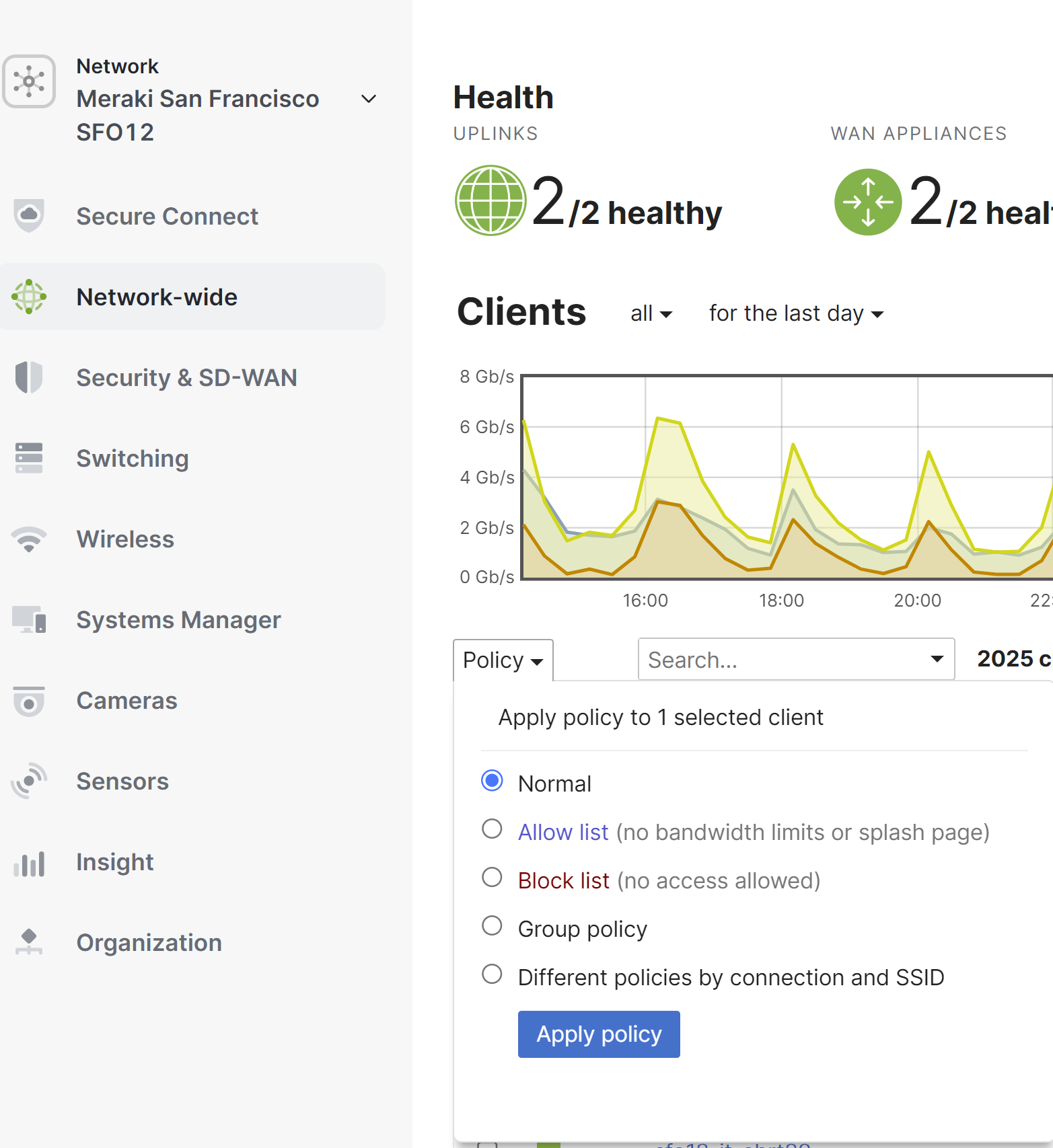
After this is completed it is possible to filter clients to determine which ones have a policy configured on them.
If the client has never connected to the network, or is not in the client list, it can still have a policy applied. This is done using the Add client button on the Network-wide > Monitor > Clients page. Enter a friendly name for the device, its MAC address, and then which policy you would like applied. Then click Save changes.
To view a list of clients that have been pre-configured, but not yet seen on the network, choose to show all clients with a policy. If a client doesn't appear immediately, the page may need to be refreshed first.

Using the Client Details Page
The current policy will be shown and can be updated at the client details page. Like above, to apply the allow list or block on a per-SSID basis or only on the MX, select the Different policies by connection and SSID. The options listed will allow you to configure blocked or allow listed per SSID and on the MX security appliance. To clear the setting, remove the blocked or allow list policy and apply normal. Below is where the setting would be configured with a combined network:


