Systems Manager Wi-Fi Settings Payload
The Systems Manager Wi-Fi Settings payload can be used to push custom wireless settings to enrolled devices. These settings can be applied to the following device types: iOS, macOS, tvOS, Android, and Windows.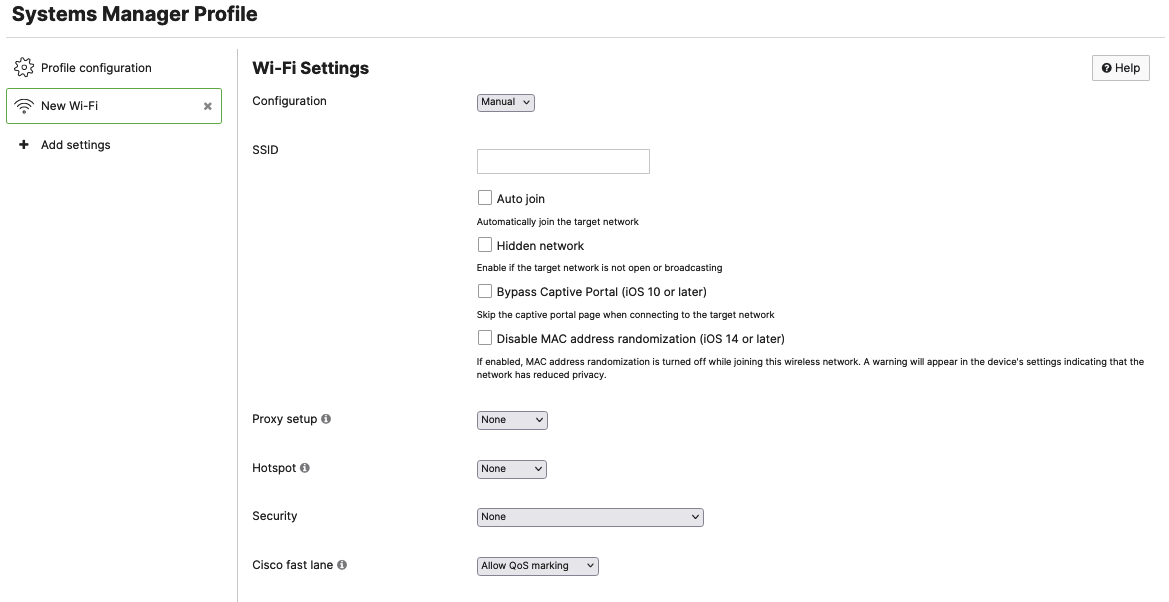
Wi-Fi Settings
Configuration: This setting can either be Manual or Sentry. Manual configurations are intended to allow administrators to push any SSID settings to devices. Sentry configurations are intended to be used with Meraki MR SSIDs. More information on Sentry configured SSIDs can be found in the Systems Manager Sentry Overview Documentation
SSID: Full name of the SSID
Auto Join: Pushes the configuration to enable the Auto join setting for this specific SSID
Hidden Network: Enable if the target network is not open or broadcasting
Bypass Captive Portal: Enables a device to skip any captive portal pages that are implemented on the SSID (requires iOS 10 or later)
Disable MAC address randomization: Disables MAC address randomization on the target device if the setting is supported
Proxy Setup: Proxying is only supported on Apple Devices. This setting can either be None, Manual, or Automatic. Selecting Automatic will allow administrators to specify a URL for target devices to reach out to for their Proxy settings but if left blank, WPAD will be used. Selecting Manual will require the following configurations:
Hotspot: This setting is only supported on Apple devices. Available in iOS 7.0+ and macOS 10.9+. This setting can either be configured as None, Legacy, or Passpoint. Legacy Hotspot settings permit the device to automatically connect to specified Wi-Fi networks. Passpoint will permit devices to automatically connect to HotSpot 2.0 Wi-Fi networks. Selecting Passpoint will also require the following settings:
- MCC/MNCs
- Enable/Disable Connect to roaming partner Passpoint networks
Additional information about Passpoint settings from Apple can be found here: https://support.apple.com/guide/depl...pea26c29b9/web
Security: This setting allows administrators to select the type of encryption the SSID is using. If this setting is set to anything except "None" or an Enterprise Encryption option, administrators will have to provide a Password. If selecting an option that is enterprise, you will be presented with additional configuration options that are outlined in the Enterprise Security section below.
Cisco Fast Lane: Cisco Fast Lane is only available on iOS 10+ devices. Allow-listed applications are allowed to mark DSCP for Quality of Service (QoS). Other applications are sent as best effort. Additional information about this configuration can be found in the Using Fast Lane with Systems Manager documentation.
Enterprise Security
When selecting an Enterprise Security Encryption setting, you will be presented with the following additional configurations:
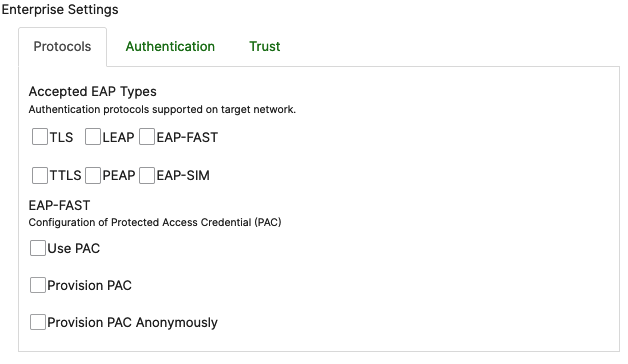
Protocols:
These settings will enable administrators to select the appropriate EAP types for their specific SSID.
EAP-TLS authentication will require the installation of the necessary identity certificate on target devices. Systems Manager offers the ability to push certificates to devices via the Certificates Payload. Once a Certificate Payload is configured and saved under the same settings profile, it will automatically populate as an option under the "Trust" section of the Wi-Fi Enterprise settings. Additional information on how to select and push the appropriate certificate can be found in the Trust section below.
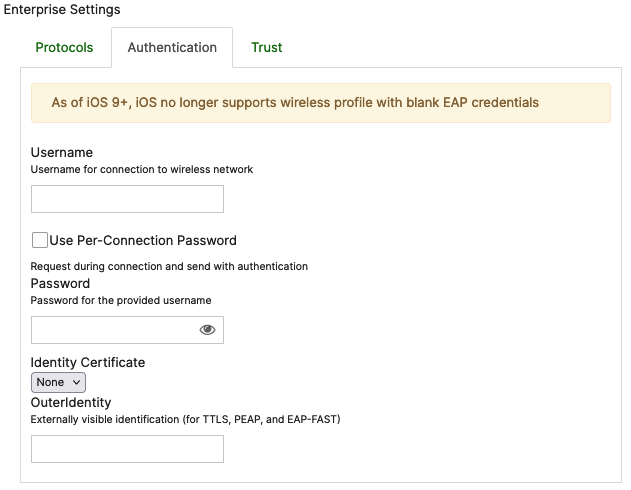
Authentication:
These settings will enable administrators to push pre-configured authentication credentials to devices using this profile. If the Username and Password fields are left blank, the system will prompt the user during login.
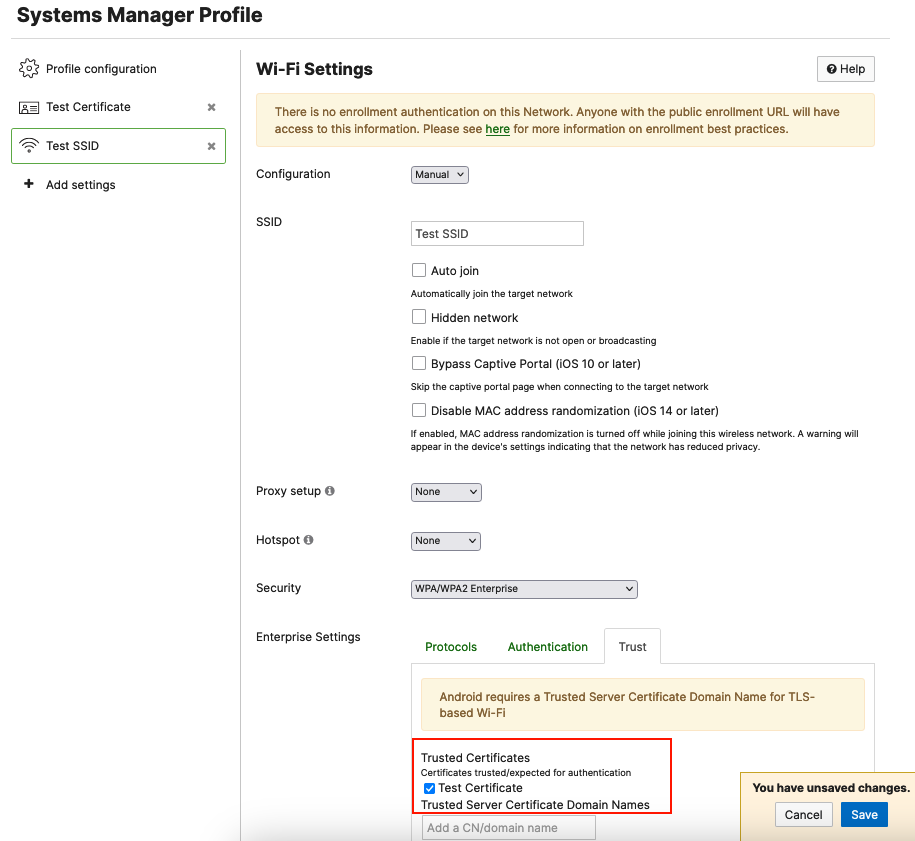
Trust:
This setting will enable administrators to select a Trusted certificate for TLS-based Wi-Fi
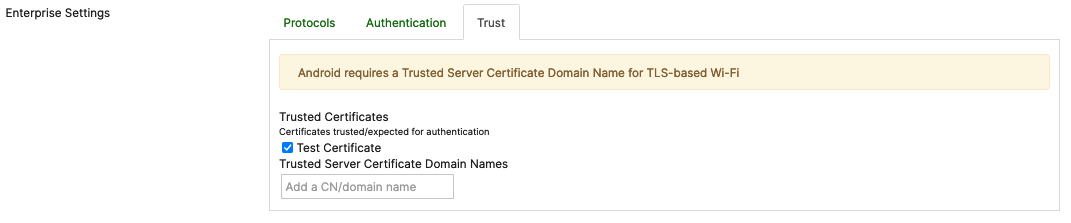
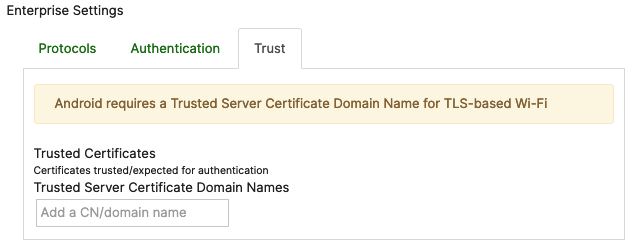
To have Certificate options to choose from under the Trust tab, you will first need to configure and save a certificate payload in the same profile where you configure your Wi-Fi settings. If you do not have Certificate Settings configured under the same profile, your Enterprise Trust tab will have no certificate options to choose from:
If you plan on using EAP-TLS authentication with certificate identification, you will first have to configure and save certificate settings on your payload as follows:
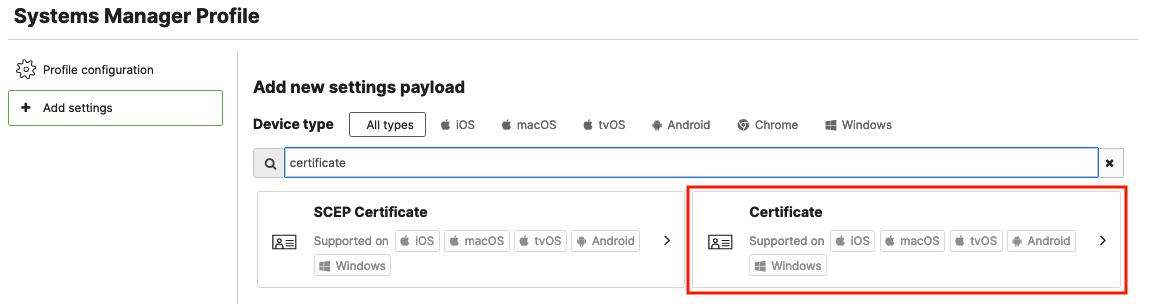
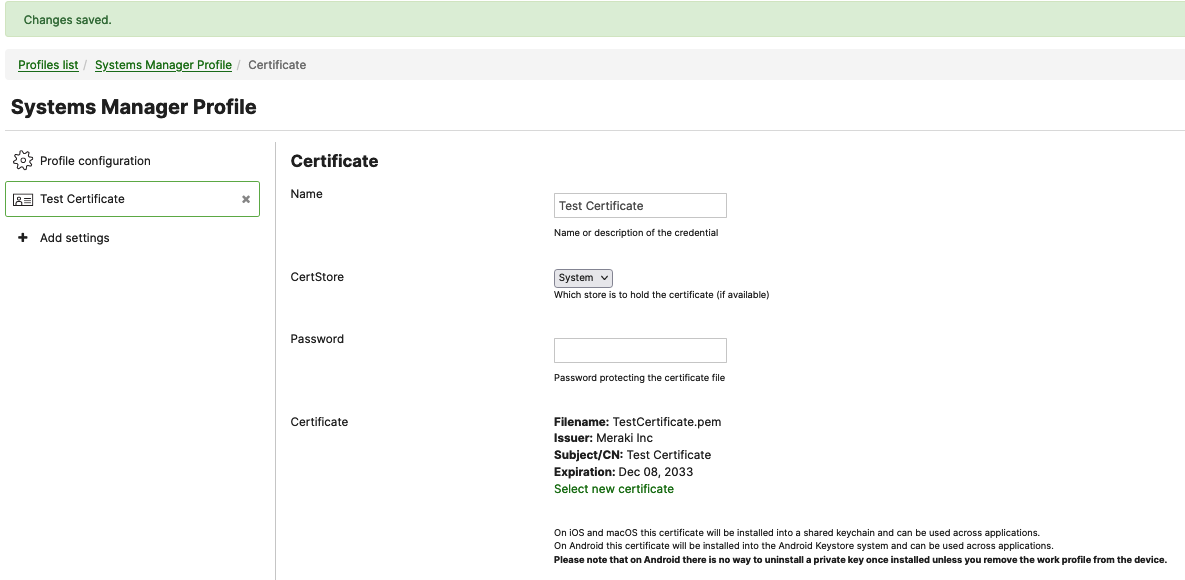
For additional information on how to configure a Certificate payload, please follow the steps outlined in the Certificate Payload documentation.
After you save the Certificate Settings on your payload, the certificate will be displayed as a selectable option under Enterprise Settings > Trust > Trusted Certificates: