Windows BitLocker Encryption with Meraki Systems Manager
Windows BitLocker Encryption

Windows BitLocker is the native method of enabling local disk encryption on Windows 10 and Windows 11 devices. Meraki Systems Manager can set various configurations to enable BitLocker with specific settings and make viewing/managing this encryption easy from Dashboard. Furthermore, Systems Manager Security Policies can be used to monitor device encryption in bulk from Dashboard, alert on non-encrypted devices, and use this security policy compliance as auto policy tags in Dashboard.
Prerequisites
To support BitLocker, devices must have Windows 10 version 1803 or later and MDM profile enrolled into Meraki Systems Manager. For more information on differences between agent and MDM profile enrollment, see here. For more information on enrolling Windows devices into Meraki Systems see here.
Dashboard Setup
To configure Bitlocker on SM enrolled Windows machines simply go to Systems Manager > Settings and create a profile with the BitLocker payload added to it. More information on creating profiles can be found here.
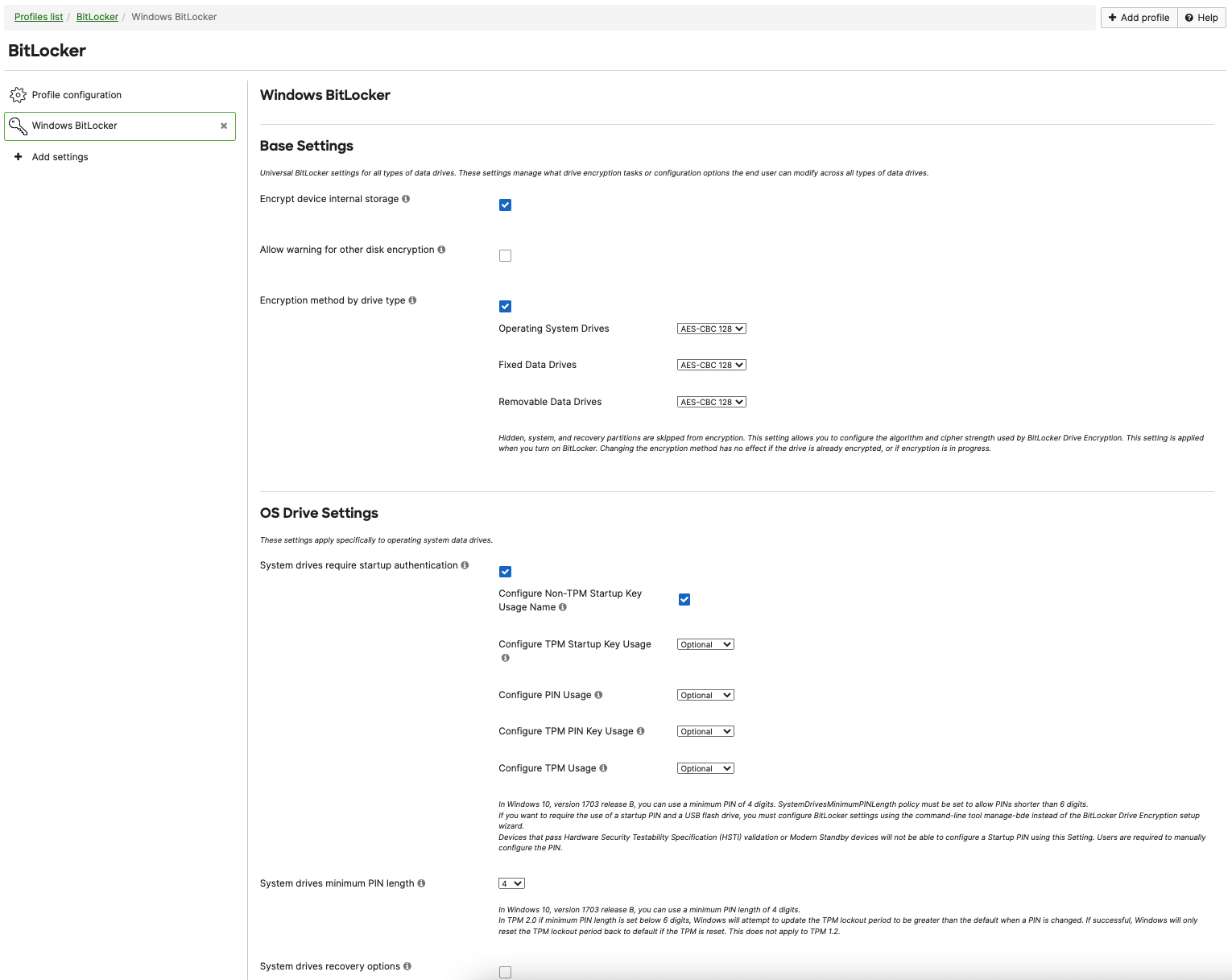
Select the desired Base Settings, OS Drive Settings, Fixed Data-Drive Settings, and Removeable Data-Drive Settings.
Systems Manager leverages the native Windows MDM APIs to set the supported values and enable disk encryption. The Microsoft documentation on BitLocker features can be found here.
Once the BitLocker profile is installed on a device, you can see its status on the Systems Manager > Devices list, by clicking on the device and finding its "Profiles" second.
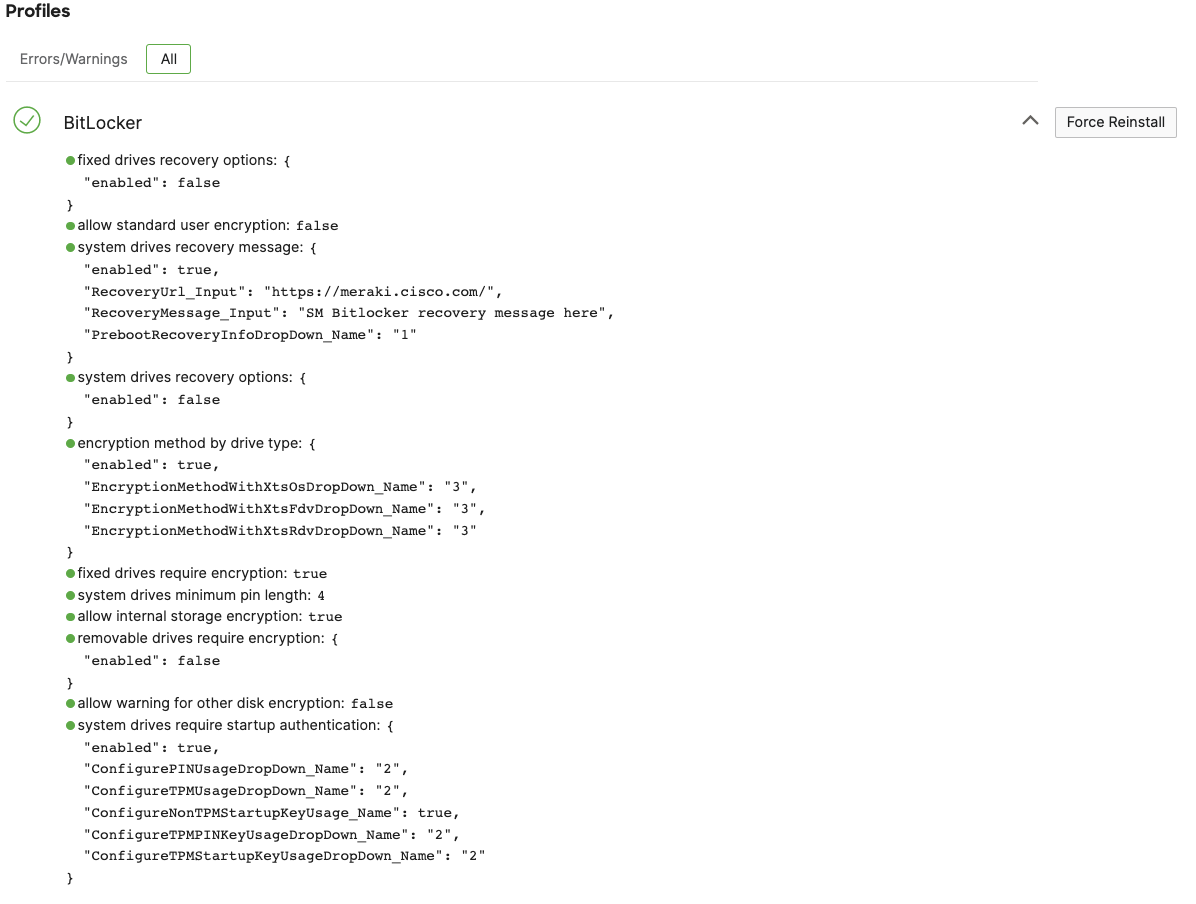
The value allow internal storage encryption indicates if the local disk is encrypted yet. In this example above, allow internal storage encryption is returned as true so we know the local device is encrypted. Since encryption can take devices some time to enable, it is expected to see this value returned as false until the local disk is actually encrypted. If allow internal storage encryption is returned from device as false but the profile is setting Encrypt device internal storage to true, then this profile will show in the "Errors/Warnings" section of the profile list until it matches the configured value.
Device Encryption
Based on the configured BitLocker profile in Systems Manager, the device will get a notification to enable the disk encryption as configured.
- There are some device requirements to silently enable Bitlocker, such as a TPM (Trusted Platform Module) 1.2 chip enabled Windows device. See Microsoft's full list of requirements to silently enable Bitlocker here.
- Bit-Locker Keys are not stored in Dashboard and it is up to the administrators to securely store them. They cannot be stored on the managed endpoint's drive(s) that is being encrypted.
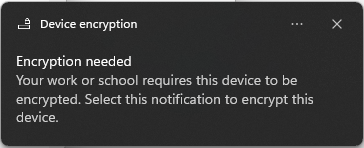
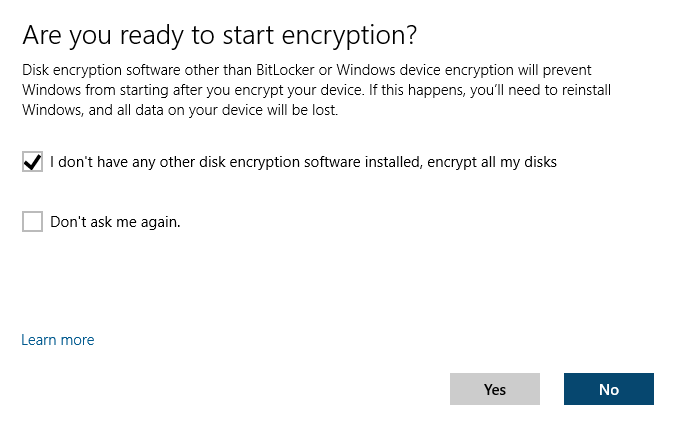
Accept the prompt, and follow the Windows BitLocker setup wizard. Depending on the configuration, the end user may be required to set their own password, PIN, and/or USB flash drive recovery disk.
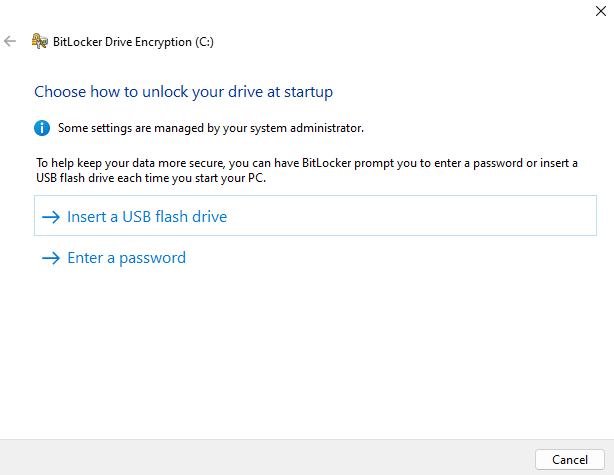
Set the recovery method, and then start the encryption.
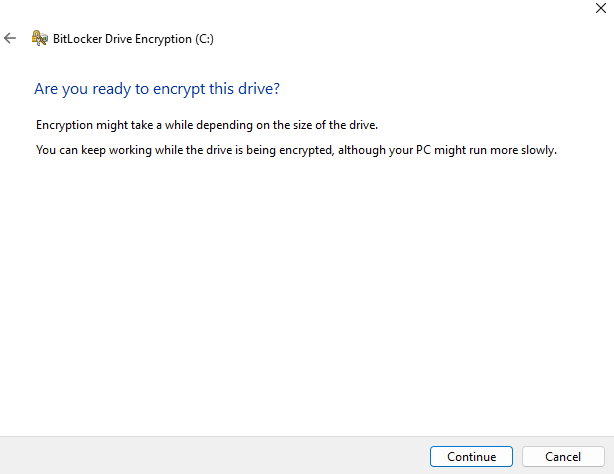
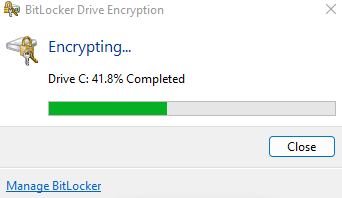
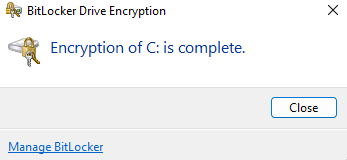
Depending on the disk's size and read/write speeds this process will take some time to complete, and show the user the encryption status in the menu bar.
BitLocker encryption status can be viewed and managed locally if the end user has permissions to do so.
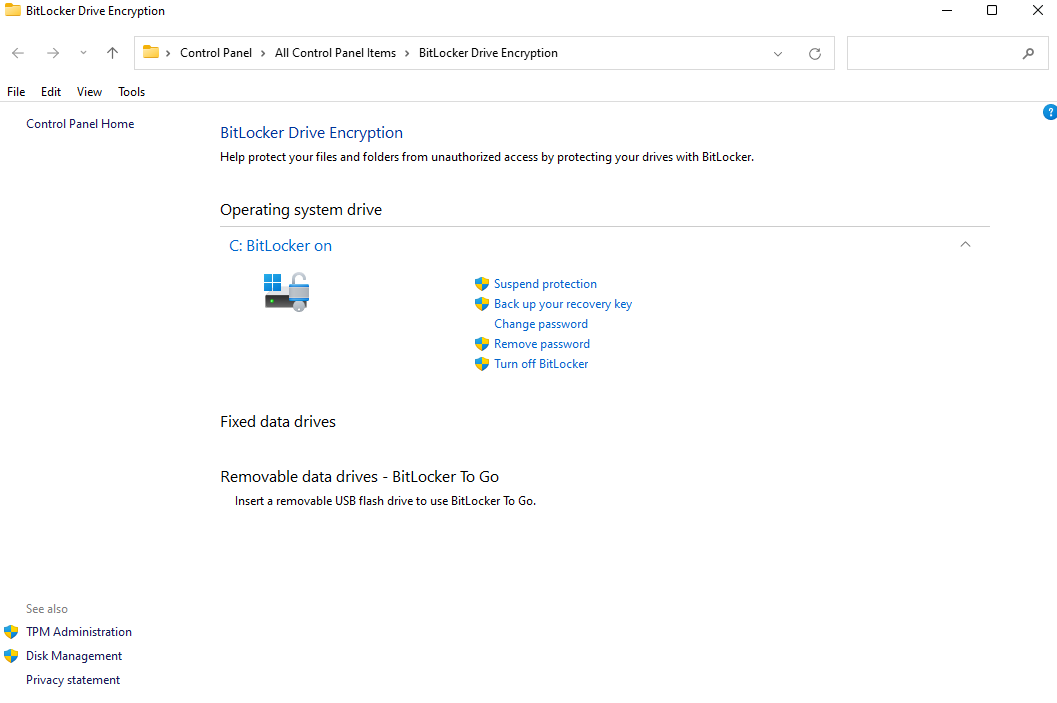
Dashboard Monitoring
To monitor encryption in bulk, administrators can create a Systems Manager Security Policy checking for Encryption. This security policy will check all operating systems enrolled in Systems Manager for encryption of their disks (e.g. Filevault on macOS, Bitlocker on Windows, etc). From there, this security policy compliance will be created as an auto policy tag to use as a dynamic tag in other places in Systems Manager, such as for email alerts or profile/app scoping. Furthermore, the Security Policy compliance will be a new field on the Systems Manager > Devices list which can be added/removed for easy viewing of the entire Systems Manager network at once. More information on Security Policies can be found here.
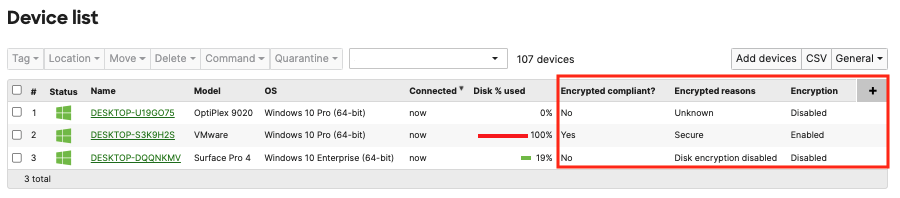
Systems Manager is able to detect 3 Windows Bitlocker encryption states: "Unknown", "Secure", or "Disk encryption disabled"

