Samsung Knox
Samsung Knox is platform available for compatible Samsung Android devices that can be used to enhance device security when combined with a Mobile Device Management (MDM) platform, such as Systems Manager Enterprise. This article will discuss features available in Systems Manager Enterprise as part of this platform.
While profiles containing Samsung KNOX settings can be applied to any device, they will only be effective on compatible Samsung devices.
Systems Manager Security Policies can also be used to control deployment of profiles to devices based on their compliance status.
We recommend enrolling Android devices into Systems Manager through Android Enterprise whenever possible. To see a comparison of features available through Android Enterprise vs KNOX, see the Android Enrollment article.
Kiosk Mode
Kiosk mode can be used to force a device to always run a single app full screen, with no access to other apps, device settings, etc. This is ideal for point-of-sale (POS) terminals, interactive displays, or similar applications.
To configure:
- Navigate to Systems Manager > Manage > Settings.
- Select the desired Profile, or create a new one.
- Go to the Samsung Knox tab.
- Click the checkbox next to Enable Kiosk Mode.
- Select the desired managed Application from the list. Only managed apps can be used, and must be added on the Systems Manager > Manage > Apps page.
- Click Save Changes.
To use the profile, ensure that both it and the desired app have been applied to the device. Read the article on Pushing custom apps and profiles to devices or the article on deploying store apps to devices for more information. Once the app and profile are installed, the device will run the app in full-screen mode whenever it is online.
App Allow List and Block List
The block list functionality can be used to control which apps are allowed to be installed on devices. To enable:
- Navigate to Systems Manager > Manage > Settings.
- Select the desired Profile, or create a new one.
- Go to the Samsung Knox tab.
- Click the checkbox to Enable App Allow List/Block List.
- Configure as desired, based on the options discussed below.
- Click Save Changes.
Note: Managed apps (MDM > Apps) are NOT exempt from these restrictions. Managed apps will fail to deploy if on the block list. Ensure these apps are either not on the block list, or covered in the allow list.
App Block List
The App Block List is used to indicate any apps (or patterns) that users are not allowed to install on the device. The app is listed by its package name (ex. "com.meraki.sm" for the Systems Manager app), and can use wildcards to block list groups of apps (ex. "com.meraki.*" would block all Meraki apps).
Apps can easily be added by using the Select apps bar to search by display name, and then clicking the icon to add the app to the list.
Apps can also be manually entered by typing the desired package name, or pattern, in the textbox. Once the desired pattern has been entered, click Add option.
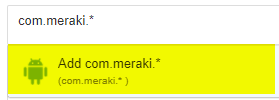
Once the packages are added, they'll appear as individual bubbles in the field. To remove a package, click the X.
After the profile is pushed to the device, any user attempting to install apps that violate the block list will receive a message similar to the one shown below.
App Allow List
The App Allow List is used to indicate any apps that should be explicitly allowed, overriding the block list. Package names are entered in the same way as block list apps above.
Apps that were installed prior to the allow list being created will remain on the device. Only future app installations will be subject to the allow list.
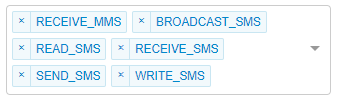
Permissions Block List
The permissions block list will not allow users to install apps that require any of the permissions selected. Information about what is provided by each of these permissions is available in the Android Developer Documentation.
As an example, the ability to send or receive text messages (SMS/MMS) over cellular could be blocked by selecting the following permissions.
Overriding Block Lists with Allow List Profiles
Block List and Allow List settings will be combined across profiles on a device, with Allow List settings taking priority. Thus, a general profile could be deployed to all devices with more restrictive settings, and then more apps allowed through a second profile with Allow List options.
Samsung Knox Service Plugin
The Knox Service Plugin app (com.samsung.android.knox.kpu) can be used to configure Samsung Knox policies. To configure this, add the Knox Service Plugin app to the SM > Apps page and deploy it to devices as a Managed App. Once the Knox Service Plugin app is installed on devices, the Managed App Configuration profile can be used to configure specific Knox policies on devices.

With the Meraki SM Managed App Configuration and Knox Service Plugin app installed: endpoint devices can be configured with specific Samsung Knox settings and restrictions. The Knox Service Plugin application shows as configured on end user devices with the latest policies from the SM Managed App Config. For more information on Samsung Knox settings for the Samsung Knox Service Plugin please review the Samsung documentation.


