Best Practice Design - Endpoint Management
Cisco Meraki Systems Manager is a complete endpoint management solution that provides deep visibility and control over your Android, Chrome OS, iOS, macOS, and Windows devices. It unifies endpoint management into a single pane of glass through an easy-to-use, cloud-based Dashboard shared with the rest of the Meraki stack, and is the only solution to bring network level security and visibility to the endpoint.
Key capabilities include:
- Manage and monitor endpoint devices
- Manage and distribute mobile and enterprise applications
- Investigate and change device functionality based on device status
Systems Manager Capabilities
Manage and Monitor Endpoint Devices
Cisco Meraki Systems Manager provides visibility into managed endpoint devices to help you better understand and react to changes. State changes include events such as a non-sanctioned application being installed, corporate applications being removed, and a device leaving a predetermined area. The dynamic tagging functionality in Systems Manager continually assesses the state of endpoints and automatically takes corrective action. Systems Manager profiles that are deployed on devices restrict or enable device capabilities based on your organization’s best practices.
Key capabilities include:
- Enforcing endpoint-specific restrictions (screenshots, camera usage, password length, screen lock activation, etc.)
- Applying network-based configuration (VPN, per-app VPN, wireless, etc.)
- Applying security certificates
- Monitoring and alerting when a device’s status changes (the device leaves a physical area, installs specific software, disconnects from a network, etc.)
Manage and Distribute Applications
Systems Manager application management enables the deployment of macOS, Windows, Android, and iOS applications. Organizing multi-device application management in a single interface allows you to monitor and set policies on applications holistically.
Key capabilities include:
- Delivering the right applications to the right devices based on tagging mechanisms
-
Loading and distributing macOS and Windows applications from the cloud
-
Provisioning and managing licensing for iOS and macOS through Apple’s Volume Purchase Program
-
Provisioning Google Play Store applications through Android Enterprise
Apply and Investigate Device Security Status
Systems Manager applies and actively enforces the security status of macOS, Windows, iOS, and Android devices to maintain device security integrity. By setting and responding to security requirements, you can better understand and control device access and capabilities.
Key capabilities include:
- Requiring that certain applications be loaded and running across all devices
- Requiring minimum operating system levels on all devices
- Requiring devices check in online with a specified frequency
- Requiring devices to be locked with passwords
- Requiring that devices not be jailbroken (iOS) or rooted (Android)
- Requiring that firewalls be enabled (desktop devices)
Solution Design
Requirements
Customers must set up a Cisco Meraki account and obtain licensing for Meraki Systems Manager. Systems Manager licensing is offered as a 1-, 3-, or 5-year subscription.
Logical Topology
The logical topology consists of endpoint devices enrolling and communicating with the Cisco Meraki cloud, and at times with MDM services from the operating system provider, such as Google or Apple notification services. If communication between the endpoints and that cloud traverses a firewall, you will need to open ports as described here. Additional info on Systems Manager specific firewall settings can be found here.
Best Practices
Deployment settings should vary depending on the level of control your organization has over devices, for example BYOD vs company-owned devices. Consider the following settings, especially for company-owned or single-purpose devices.
- Apply device security settings:
- Allow all mandatory apps
- Deny all non-sanctioned apps—for example, ensure that apps like Tor browsers aren’t installed on devices
- Mandate passcodes on devices combined with minimum screen-locking periods
- Mandate that firewalls are running on devices
- Mandate that devices are not jailbroken or rooted
- Mandate a minimum secure operating system for each device type
- Monitor and remediate devices
- Alert when devices install non-sanctioned software
- Alert when mission-critical devices leave the network or go offline
- Alert when devices violate mandated security settings
- Restrict non-corporate cloud apps
- Remove device profiles when devices leave their proper geographical area or violate device security rules
- Remove device applications when devices leave their proper geographical area or violate predefined device security rule
Solution Deployment Concepts
The following key concepts will be helpful in understanding how to set up your Cisco Meraki Systems Manager environment. Thinking about these steps beforehand will simplify initial deployment and ongoing management.
- Enrollment: When devices enroll into Systems Manager, they give you full device access for setting user restrictions, managing applications, and enabling device visibility and management.
- Tags: Systems Manager uses tags to verify that the right devices get the right applications, profiles, and restrictions. Tags can be applied manually, automatically, and even dynamically, based on a device’s status.
- Profiles: Profiles control device configurations and enable or restrict device access, depending on the use case.
- Applications: Systems Manager enables application delivery and management through public app stores and custom applications hosted in a cloud-based repository.
- Security: Security-solution sets within Systems Manager include securing the device itself, verifying that only secure corporate applications are installed, and processes to wipe data in the case a device is lost or stolen.
- Troubleshooting: Systems Manager has built-in tools to troubleshoot mobile and desktop devices.
Enrollment
Before devices can be managed within Systems Manager, they have to be enrolled in your Enterprise Mobility Management (EMM) network. Different types of enrollment can be used to meet the needs of different device types or deployment models. For example, while the simplicity of fully automated enrollment is ideal, this method does not suit Bring-Your-Own-Device (BYOD) deployments. It also isn’t compatible with all devices. Some of the available enrollment methods are described below.
This is a quick introduction to a few enrollment concepts. For comprehensive guides to enrolling devices for each operating system, refer to the Enrolling Devices article.
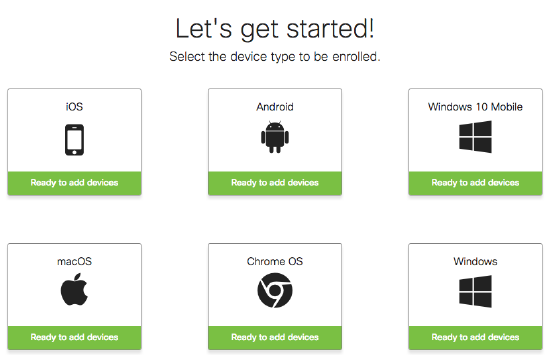
Systems Manager Enrollment Authentication
To provide an extra layer of security, you can require authentication upon enrollment through services such as Active Directory, Azure, Google, or Meraki authentication. Authentication is compatible with all types of enrollment, and it has additional benefits beyond security. First, enrollment authentication ties an owner to a device automatically. Second, enrollment authentication can tie in a user’s groups (either LDAP or those managed by Cisco Meraki solutions) to all of their devices as dynamic tags, for automatic grouping.
For a comprehensive guide to enrollment authentication, refer to the SM Enrollment Authentication article.
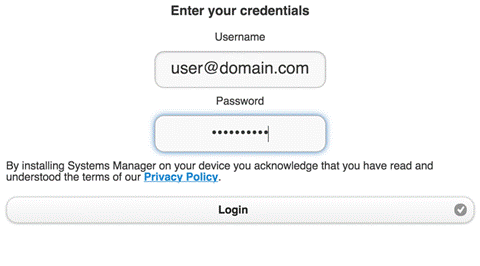
Fully Automated Enrollment
With fully automated enrollment, a device is enrolled into Systems Manager automatically. It can be configured so that the user has no option to cancel or prevent the enrollment. In addition, the device will automatically have apps, controls, and settings provisioned based on the person using the device (device owner) with no direct user or administrator configuration required.
This type of enrollment allows for the highest levels of EMM control. It is possible only with iOS and macOS devices that are eligible for Apple’s Device Enrollment Program (DEP). With DEP, devices can be directed by Apple to automatically enroll into Systems Manager when the user first powers on the device. This eliminates all prestaging and the need for Apple Configurator.
Automated enrollment can significantly reduce the administrative cost of deploying devices. This benefit increases in proportion to the number of devices being deployed.
Partially Automated Enrollment
Partially automated enrollment supports a wider range of devices, but workflows vary based on the operating system of the device. It can be completed by the end user or by an administrator who prestages the device. For example, iOS devices that are not in DEP can be provisioned in bulk through the Mac application Apple Configurator, or Android devices configured in Device Owner mode can be provisioned during the device’s initial setup process.
As with automated enrollment, two core functions are performed: installation of the Systems Manager profile, app, or agent to the device; and configuration of apps, settings, and controls.
Meraki wireless products can be integrated with Systems Manager to simplify and automate this process for users. This feature, called Systems Manager Sentry Enrollment, checks all clients connecting to an SSID and forces them to go through the onboarding process at http://m.meraki.com if it detects that they are not enrolled in Systems Manager.
Manual Enrollment
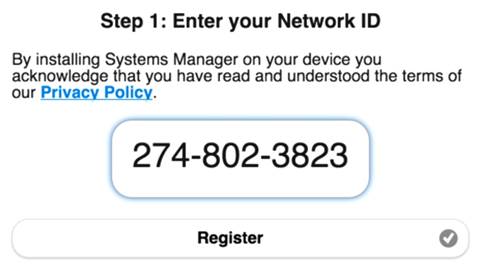
Manual enrollment supports the widest range of devices since there is no reliance on vendor- or platform-specific features. This type of enrollment is often suitable for BYOD environments. Installation of Systems Manager can be performed by a user or administrator by visiting http://m.meraki.com and following the instructions. Manual enrollment does not require a user database.
A unique Systems Manager network ID is used to identify which Systems Manager network the device should be joined to. The network ID and distribution options (email, text message (SMS), or QR bar code for the end user) can be found in dashboard.
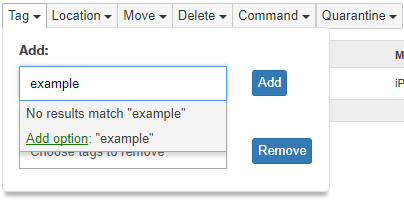
Tags
Tags are used to group devices and to inform you of a device’s current state within Systems Manager. These tags, once generated, can be used to define the apps, profiles, and settings that are provisioned by Systems Manager. For a comprehensive guide to tags, refer to Using Tags in Systems Manager.
There are three main types of tags:
- Static tags (category: Device Tag) are generally applied manually to individual devices by the administrator.
- Dynamic tags (category: Policy Tag) are automatically applied to devices based on their state and can change depending upon certain factors:
- Time-based tags use time-of-day information to implement device configurations, enforce policy restrictions, and enable application access.
- Geofence tags use location-based information to implement device configurations, enforce policy restrictions, and enable application access.
- Security policy tags use a device’s posture to implement device configurations, enforce policy restrictions, and enable application access.
- Owner tags (category: User Tag) use identity information to implement device configurations, enforce policy restrictions, and enable application access. Owner tags can be created or automatically imported from certain directory systems.
Scoping apps and profiles with tags is accomplished by using logical operators (AND and OR), which allows for a high degree of granularity when setting a device scope.
Profiles
After a device is enrolled, additional configuration profiles can be installed via Systems Manager. These profiles contain settings that are installed onto your managed devices, such as Wi-Fi access, VPN access, device restrictions, app home-screen layouts, email ActiveSync settings, and much more. Profiles allow you to easily customize and secure your enrolled devices. For more information, review Configuration Profiles.
In the Cisco Meraki dashboard, the Systems Manager > MDM > Settings page allows you to create or delete configuration profiles. These profiles are not to be confused with management profiles, which are installed when a device is first enrolled into Systems Manager.
Profiles are scoped to devices based on tags. This allows you to specify the devices, users, and specific conditions required for a device to receive a profile.
In an enterprise environment, it is often necessary to preconfigure or limit the availability of some features. These can be restrictions like disabling the camera or configuring settings like email or Wi-Fi. Restrictions and settings can be collected together into a profile, and devices can have multiple profiles applied to them.
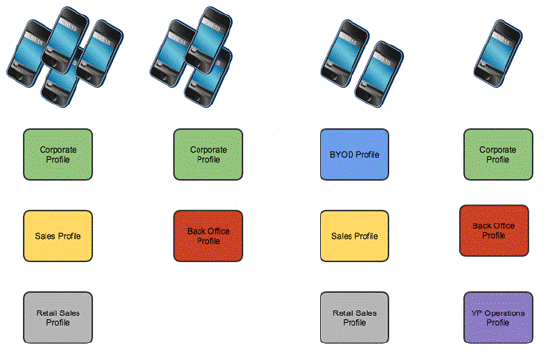
Multiple Profiles
Systems Manager also uses tags to scope which devices get which profiles. Tags allow for a highly granular or hierarchical approach to applying restrictions to devices. In an enterprise environment, you may want to create a baseline or global profiles that apply to a larger group of devices, like BYOD or Corporate. You can then apply more specific profiles targeted at smaller groups, like Sales or Back Office. This eliminates the need for administrators to maintain the same global settings across multiple profiles for each device use case. This global profile can then be updated in the future, and all associated devices will automatically update. If a device receives multiple profiles that have conflicting settings, the most restrictive applies. The ability to use multiple profiles allows for granular device restrictions with simple management.
Assigning a profile to devices in the dashboard uses the same scoping method discussed earlier: profiles can be scoped to static or dynamic tags. Dynamic tags reduce the work required to manage a large number of devices, while also providing automated control. For example, if a device is not physically in the office, then it can have the office restrictions removed for home use through the geofencing feature. For more information, see Geofencing with Managed Devices.
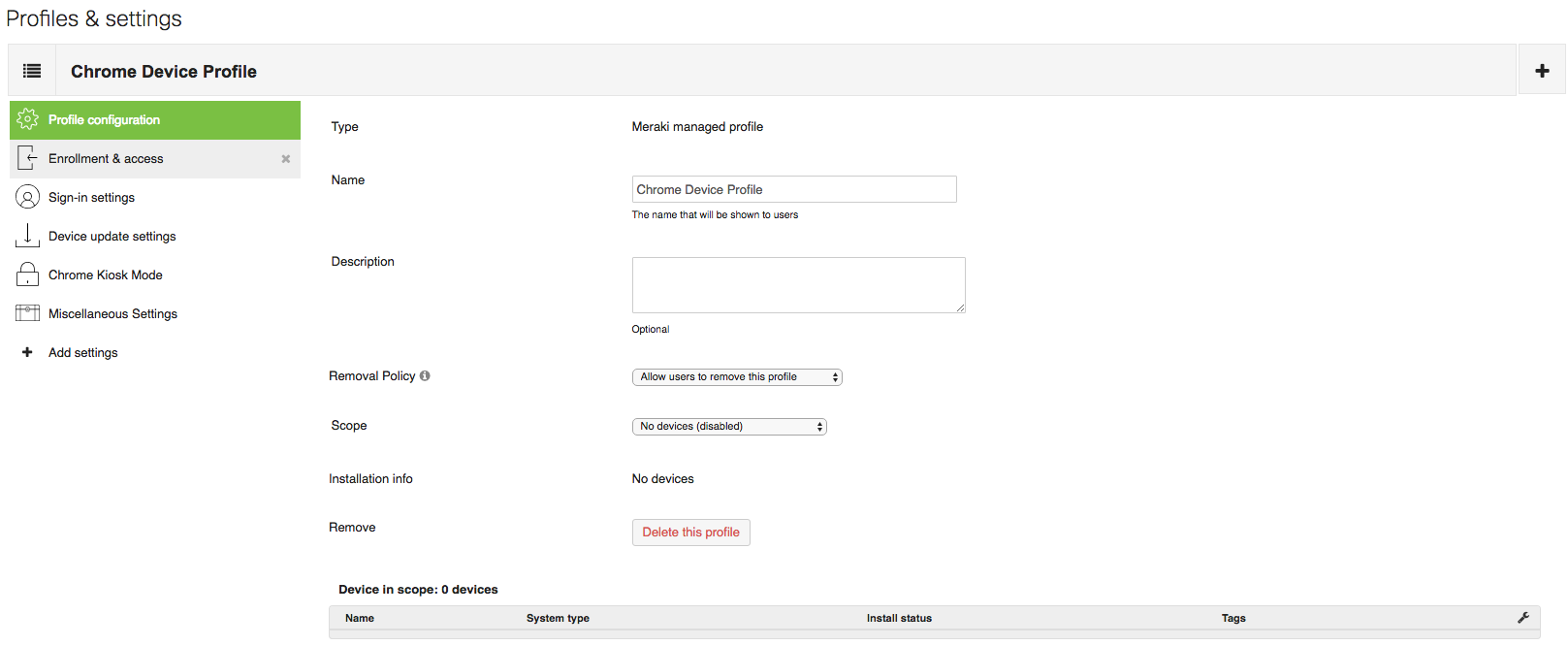
Settings
The Systems Manager > MDM > Settings page allows you to configure the specific settings associated with a particular configuration profile. These settings and profiles can be used to ensure that your devices meet business requirements and receive the configurations your users need to work.
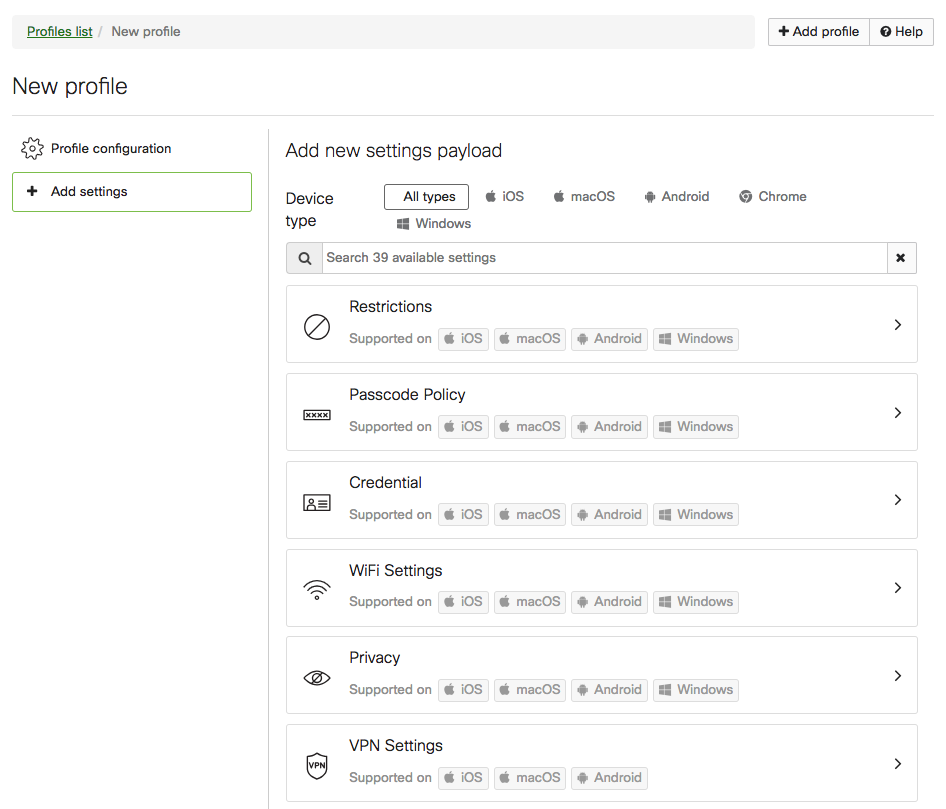
After creating a new profile, click the Add Settings option on the left to begin adding settings payloads to your profile. Profiles can contain multiple payloads at once, and multiple profiles can be installed on a device. Your settings and profiles should be tailored to how your device deployment and tag structure are organized. For more information, see Configuration Settings.
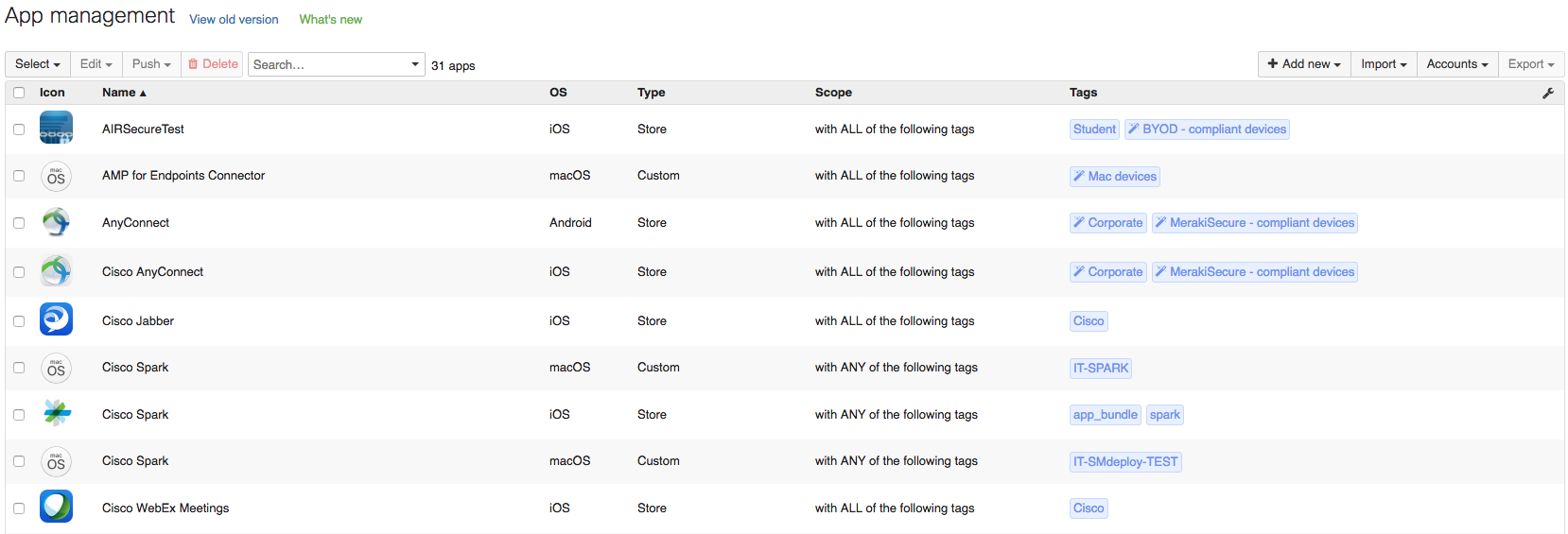
Applications
Cisco Meraki Systems Manager can deliver both mobile and desktop applications through the dashboard. This includes apps found in public app stores (iOS, macOS, Android) and custom apps (iOS, macOS, Android, Windows) that can be hosted externally or on the Cisco Meraki cloud.
Mobile Apps— iOS and Android
For iOS apps, Systems Manager integrates directly with both public and enterprise app stores. It also supports deploying custom .ipa files. To silently install apps without Apple IDs or user prompting, please review how to use Systems Manager with Apple's Volume Purchase Program (VPP).
For Android apps, Systems Manager can be used to deploy Google Play apps or custom .apk files. Organizations using Android Enterprise can create managed stores that will display only approved applications. See Push Applications.
Desktop Apps—Windows and macOS
Systems Manager can install .msi, .exe, .pkg, .app, and .dmg files. For information on how to install software on Windows and Mac machines, see Installing Custom Apps. For macOS, VPP can also can be used to license apps directly to an end user's Apple ID, which allows end users install apps through the Mac App Store.
Application Delivery
For full guides on how to provision and update applications through Systems Manager, review the following articles:
- Deploying Store Apps for iOS/macOS and Android
- Installing Custom Apps on Managed iOS and Android Devices
- Installing Custom Apps on Windows and Mac Devices
- Using Apple’s Volume Purchase Program (VPP) with Systems Manager
App management scopes the applications that will be added to a device and installs them accordingly. Native (built-in) applications on devices provide functionality for managing everyday activities like email, calendars, contacts, and web browsing. For increased productivity and functionality on top of these native applications, hundreds of thousands of third-party apps are available in Apple’s App Store and the Google Play store for mobile devices, in addition to the many applications available for Windows and macOS desktop machines.
The Cisco Meraki Dashboard provides several ways distribute apps and apps licenses to devices and to scope your app installation to certain devices. For mobile devices, there are public apps, like those found in the Apple App Store and Google Play store, and private apps, which are custom or enterprise iOS and Android apps. You can also scope traditional software apps for Windows and macOS platforms.
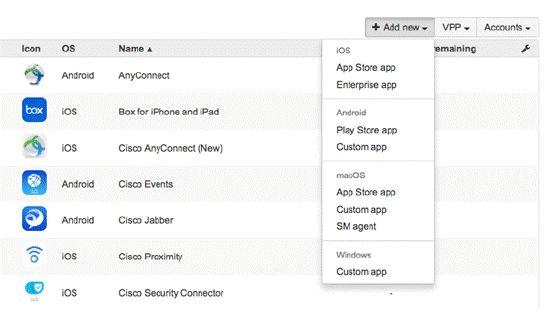
Step 1: To add applications to your Cisco Meraki dashboard, navigate to Systems Manager > MDM > Apps.
Step 2: Click the Add New button on the far right-hand side (Figure 10). Options are provided for iOS apps (publicly available), iOS enterprise Apps, Android Apps, macOS applications, and Windows applications.
Publicly available apps can be searched and downloaded from the respective platform’s app store. For other types of applications, the install file host is specified. You can upload the file to the dashboard or point to a URL accessible by the device. For more information on installing software for Windows or Mac devices, see Installing Custom Apps.
Security
Endpoint device security takes on multiple roles in a multi-cloud environment. By leveraging security profiles, you can verify end users are using devices only in the manner you intend them to. By using a combination of notifications and remote wipe tools through Cisco Meraki Systems Manager, you can mitigate potential security breaches in the event a device is lost or stolen.
Breach Mitigation
By leveraging built-in notifications you can be alerted when a device:
- Goes offline
- Leaves a predefined geographical location
- Fails security compliance
By leveraging built-in security tools you can:
- Selectively wipe devices, removing all managed apps and managed profiles installed via Systems Manager without having to restore the device to factory settings
- Erase the device, which restores the factory settings
- Engage Lost Mode for supervised iOS devices
Using these two tools you can proactively address lost and stolen items to prevent potential security breaches.
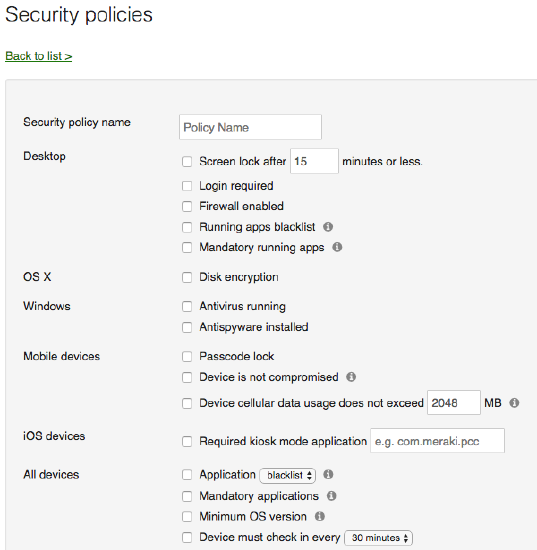
Security Policies
Using geofencing and security policies allows you to constantly monitor devices for a myriad of compliance checks, including device location, root/jailbreak status, cellular data limits, and application denying list. Security policies can be used to alert you of violations and automatically add or remove apps and profiles based on that status. For example, a security policy can remove secure email credentials and wireless settings if a user installs Tor software.
Once a policy is created, compliance information can be used to generate scheduled reports or control deployment of apps and profiles to clients through the use of dynamic tags generated by security policies. For example, in the case where a device becomes jailbroken or falls below the minimum OS version, a device’s access to internal VPN and wireless credentials can automatically be revoked and the apps uninstalled until the device is remediated and returns to compliance. Systems Manager can also send out automatic alerts to your administrative team to notify them when devices fall out of compliance or take actions such as removing management profiles.
For information on how to scope apps and profiles using security policy tags, see Using Tags in Systems Manager.
Troubleshooting
Systems Manager has built-in live tools that allow for device-level troubleshooting as well as live management of devices from the Cisco Meraki dashboard.
Mobile Live Tools
The live tools that are available depend on the device’s vendor and the level of access given to any Mobile Device Management (MDM) solution.
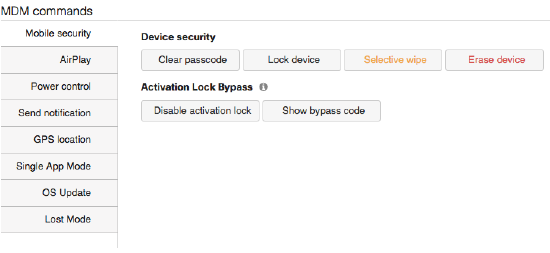
- Mobile security: Mobile security gives remote control over devices, including:
- Locking devices
- Clearing passcodes
- Selectively wiping devices (removing MDM-delivered applications and profiles)
- Erasing devices (resetting devices to factory defaults)
- Lock bypass that allows you to disable the activation lock on an iOS device when you do not have access to the Apple ID account used to lock it.
- AirPlay (iOS only): The AirPlay tool can be used to initiate streaming to known AirPlay-supported devices using MAC or device name.
- Power Control (iOS only): Power Control allows remote rebooting or shutdown of a device.
- Send Notification: The Send Notification feature sends a pop-up notification to the device to alert an end user.
- GPS Location (iOS only): GPS Location enables a request of the current location of an iOS device and delivers it back to the interface.
- Single App Mode (iOS only): Single App Mode locks an iOS device into a specific mode in which only the app you select will be available for use on the device. This is also referred to as Kiosk mode.
- Beacon (Android only): The Beacon feature enables an alarm to sound on an Android device to locate it.
- OS Upgrade (iOS only): OS Upgrade supports remote upgrading of an iOS device.
- Lost Mode (iOS only): When enabled, Lost Mode can push specific messages and contact information to the device on the lock screen.
Desktop Live Tools
The live tools that are available depend on the device’s vendor and the level of access given to the MDM solution.
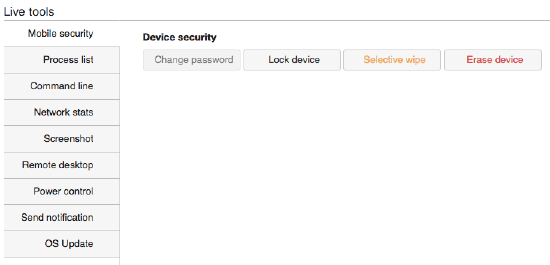
- Mobile Security (macOS only): Mobile security gives you remote control over devices, including:
- Locking devices
- Changing passwords
- Selectively wiping devices (removing MDM-delivered applications and profiles)
- Erasing devices (resetting devices to factory defaults)
- Process List: The Process List tool provides an active list of all running process on the device at the time of execution.
- Command Line: The Command Line tool allows administrators to run shell commands on Windows and Mac devices.
- Network Stats: Network Stats gives remote visibility into current network-specific information such as TCP connections, TCP statistics, and the device’s routing table.
- Screenshot: The Screenshot feature enables access to a real-time screenshot of the desktop device.
- Remote Desktop: The Remote Desktop feature enables full remote access to the MDM-managed desktop device.
- Power Control: Power Control allows remote rebooting or shutting down of a device.
- Send Notification: The Send Notification tool sends a pop-up notification to the device to alert the user.
- OS Update (macOS only): OS Upgrade supports remote updating of a macOS device.

