Cloud Management with IOS XE Overview
Click 日本語 for Japanese
With the release of IOS XE 17.15, we are beginning an exciting transition from a container-based architecture to Cloud Management with IOS XE. Cloud Management with IOS XE offers flexibility of choosing the configuration source for your switches: cloud or device.
With cloud configuration, you can use Meraki dashboard and Meraki APIs to configure your switches. The authoritative source for all configuration is the Meraki cloud.
With device configuration, you are able to configure your switch locally via the CLI or using other tools. You have the same cloud management experience in Meraki dashboard as other switches aside from how you configure your switch.
Support for Cisco Catalyst switch platforms running IOS XE has been extended to the Meraki India, Meraki China, and Meraki Canada regional clouds. This enables customers in these regions to adopt cloud-managed Catalyst solutions while ensuring compliance with local data residency and governance requirements. Both cloud and device configuration modes are supported; please refer to the Key Highlights section for known issues related to cloud and device configuration modes in these regions.
Check out our latest Cloud Entitlement for DNA offer. Eligible devices can migrate to cloud management using your existing DNA license - no additional license migration or transfer required until February 1, 2029.
Configuration: Cloud
NEW! Experience the power of IOS XE 17.18.2 (release candidate) for Cloud Management with cloud configuration. (firmware upgrades -> 'other available versions' tab).
- In IOS XE 17.18.1 we introduced support for features like BGP, VRF, In-Service Software Upgrades, and expanded support for the entire Catalyst 9200,9300, and C9500H families.
- Now with IOS XE 17.18.2, we are introducing brand new cloud EVPN fabric capabilities, Virtual Router Redundancy Protocol (VRRP) support, and more advanced management capabilities such as SmartPort Automation. Learn more.
For cloud-managed Catalyst switches running CS firmware upgrading to Cloud Management with IOS XE 17.1x.x version: Note that after upgrading to any Cloud Management with IOS XE release, downgrading to CS firmware is restricted. Factory reset may be required, and support assistance will be necessary. Learn more
Cloud Management with IOS XE unlocks the powerful capabilities of IOS XE, enabling organizations to simplify operations, enhance efficiency, and improve network performance from access to core networking. This drastically simpler architecture unlocks many benefits for your cloud-managed Cisco Catalyst switches, including the 9300-M, 9300X-M, 9300L-M and MS390 families.
-
Since the introduction of Cloud Management with IOS XE 17.15, users enjoy faster boot and initialization, a Cloud CLI Terminal for running troubleshooting commands directly from the dashboard, and a new generation of features powered by advanced IOS-XE capabilities!
-
In IOS XE 17.18.1 we introduced support for features like BGP, VRF, In-Service Software Upgrades, and expanded support for the entire Catalyst 9200,9300, and C9500H families. Now with IOS XE 17.18.2, we are introducing brand new cloud EVPN fabric capabilities, Virtual Router Redundancy Protocol (VRRP) support, and more advanced management capabilities such as SmartPort Automation (early access).
Key highlights
-
Introducing a new onboarding flow including both cloud and device configuration: two powerful ways to manage your Catalyst 9000 switches from the Meraki dashboard. These options give you the flexibility to choose Cloud Management with cloud configuration in Meraki dashboard or device configuration (previously referred to as cloud monitoring) that offers configuration via an embedded cloud CLI while leveraging the cloud for monitoring and troubleshooting. Learn more.
-
Management Interface Architecture Change: a dedicated management interface is no longer required.
-
Default Network Module: this enhancement simplifies and consolidates network module configuration into 8 default ports that get applied dynamically to any inserted network module. (Watch this video to learn more about this change or see the Cloud Operating Mode for Catalyst Cloud-Managed Switches Overview documentation)
-
Standardized Cisco Logging and Interface Naming
-
Configuration Templates
-
Device Uptime
-
Support for regional clouds: Meraki India, Meraki China, and Meraki Canada
-
Note for Meraki China: Intelligent packet capture and standard packet captures are currently not supported for Catalyst switches running IOS XE in the Meraki China region. Support for Intelligent packet capture is planned for a future update.
-
For further details, refer to the release notes on the cloud dashboard.
Share Your Post-upgrade Feedback!
We value your feedback on our latest release! Complete this short 5-minute survey to tell us about your experience.
Available Firmware and Migration Paths
Refer to the Cloud Configuration: Release Versions and Highlights page. This page lists the features, supported models or families, minimum required licenses, and other details for each major Cloud Management version with IOS XE in Cloud Configuration.
|
Category |
Product |
Firmware Needs |
Path |
|---|---|---|---|
|
Firmware Upgrade for Cloud-Managed Catalyst Switching
|
Cloud Managed Catalyst 9300/MS390/C9200L |
Cloud Management with IOS XE 17.1x.x |
Upgrade from CS17 or Cloud Management IOS XE 17.15 to newest release on dashboard following the steps documented in Upgrade Steps for Cloud-Managed Catalyst Switches in Cloud Operating Mode. |
|
Switching Migration from CLI/DNA Management to Meraki Management
|
Catalyst 9300 and C9200L from DNA/CLI |
Cloud Management with IOS XE 17.1x |
Follow the migration process documented and supported models in Migration from CLI-managed Catalyst Switches to Meraki Cloud Operating Mode |
| Catalyst 9200/L/CX, Catalyst 9300, Catalyst 9500 high performance switch | NEW! Cloud Management with IOS XE 17.18.x | ||
|
Catalyst 9300 |
CS17 GA |
Follow the migration process documented in Migrating DNA Management Mode to Meraki Management Mode (Migrated switches will run CS) |
Prerequisites
Cloud-managed Catalyst switches that are being scheduled for an upgrade from any CS firmware version to the latest Cloud Management with IOS XE version (17.1x.x) should first meet the minimum CS firmware requirement of CS17 version before upgrading.
Supported Models and Minimum Firmware Requirement
ATTEMPTING TO MIGRATE UNSUPPORTED MODELS MAY RESULT IN A UNUSABLE SWITCH, AND MAY VOID THE DEVICE WARRANTY. REVIEW THE LIST OF SUPPORTED MODELS BEFORE PROCEEDING WITH THE UPGRADE.
Applies only to configuration source: cloud: Stacking Limit for C9200L series models: C9200L series models support stacking configurations of up to 5 members. Ensure your stacks for these models adhere to this limit. Exceeding 5 members may lead to unexpected behavior. This will be resolved in a future release.
Refer to the Cloud Configuration: Release Versions and Highlights page, which lists the features, supported models/family, minimum required license, and other details for each major Cloud Management with IOS XE version in Cloud Configuration.
Before You Upgrade or Migrate: Key Considerations
Upgrade or Migration Checklist
Due to changes in behavior caused by architectural differences between CS and IOS-XE, it is strongly advised to review this checklist and key considerations to ensure successful upgrades and connectivity thereafter
|
Downgrades are restricted |
Downgrades from Cloud Management with IOS XE to any prior CS firmware via the dashboard is restricted. For more details, refer to Downgrading from Cloud Management with IOS XE is Restricted |
|
Review any actions that may be required if L3 interfaces are configured
|
Due to changes in behavior on management interface, it is required to review the management VLAN scenario that applies to your devices and make required changes before proceeding with the upgrade. Review and take action if required on the following: Migrating Switches From CS Firmware to IOS XE Firmware |
|
Allow ICMP Pings to dashboard |
Catalyst devices need ICMP ping connectivity to several destinations to test uplink connectivity to the dashboard. For successful upgrades and continued connectivity post-upgrade, ensure that outbound ICMP pings from Catalyst devices are permitted to the following destinations: |
|
Resolve switch alerts on Organization > alerts page |
For successful upgrades and continued connectivity post-upgrade, resolve all alerts on the Organization > Alerts page that are associated with the switches being upgraded. |
|
Resolve Bad IP assignment alert on Uplink interface
|
A bad IP assignment could cause unstable uplink connectivity to the dashboard which is required for a successful upgrade and continued connectivity post-upgrade. Resolve Bad IP assignment alert on the uplinks of the switches being upgraded. For more details, refer to Bad IP assignment configuration |
|
Resolve VLAN mismatch alert on Uplink interface |
VLAN mismatches on the uplink interfaces could cause connectivity issues to the dashboard which is required for a successful upgrade and continued connectivity post-upgrade. Resolve any VLAN mismatch alerts found on the uplinks of the switches being upgraded. For more details, refer to VLAN Mismatch Alerts for Meraki Switches |
|
Resolve stacking related issues |
Issues related to stacking could cause upgrade failures on some devices leading to version mismatch between the stack members and may severely impact connectivity from the stack members. For successful upgrades and continued connectivity post-upgrade, resolve any issues related to stacking such as Misconfigured Switch, Unconfigured Switch and Switch Not Connected to Stack. |
|
Review unsupported features
|
Review unsupported features before proceeding with the upgrade Unsupported features on IOS XE 17.15.3 with cloud configuration |
|
CS to IOS-XE: Upgrade CS devices to IOS-XE before adding them to existing networks set to IOS-XE firmware |
If you plan to move or add CS firmware devices to networks with IOS-XE firmware, it is strongly advised to upgrade those CS firmware devices to IOS-XE before moving or adding them into IOS-XE networks. For new CS firmware devices that need onboarding, you can first add them to a separate network, upgrade them to IOS-XE firmware, and then move them to the intended network that already uses IOS-XE firmware. |
| DNA/CLI-managed to IOS-XE: Add switches to existing networks set to IOS-XE firmware | To onboard a DNA/CLI-managed switch to the dashboard in cloud mode, ensure you add the switch into a network already configured for Cloud Management with IOS XE firmware. Adding a switch into a network configured for CS firmware may have unexpected results. |
Scheduling CS to IOS-XE firmware upgrade - dashboard pre-checks and alerts
When scheduling a firmware upgrade from CS to IOS-XE from Organization > Firmware Upgrades > Schedule upgrades, the Dashboard performs several pre-checks and displays relevant banners to alert you about any necessary actions.

|
Alert name |
Alert details |
|
Resolve switch alerts before proceeding |
Dashboard performs a pre-check to determine existing alerts on switches that may cause upgrade failure or impact switch connectivity after the upgrade. If there are any alerts that may impact the upgrade or connectivity, a banner is displayed linking to the existing alerts. You may acknowledge and continue without any action, but it is highly advised to review and resolve any alerts before proceeding with the upgrade. |
| Highly recommended: ICMP pings blocked |
Catalyst devices require ICMP ping connectivity to multiple destinations to verify uplink connectivity with the dashboard. The Dashboard selects one switch IP address from each management subnet in the network and performs a pre-check by pinging these destinations: config-2037.meraki.com, catalyst.meraki.com, google.com, 8.8.8.8 (Google DNS) and 2001:4860:4860::8888 (Google DNS) Note: The uplink ICMP connectivity pre-check is performed once every 24 hours for a given network. As a result, if you permit ICMP pings and attempt to schedule an upgrade within that same 24-hour window, the banner may still be displayed. |
|
Action required before upgrade |
By default, a checklist warning banner appears for your review. To ensure a successful upgrade and continued connectivity after the upgrade, it is highly advised to review the checklist and make any necessary changes before acknowledging and proceeding. |
Firmware Upgrade Visibility for Cloud-Managed IOS XE Switches
Refer to Firmware Upgrade Visibility for Cloud-Managed IOS XE Switches to learn about the visibility you can gain into upgrade status, upgrade stages, and upgrade failure/retry behavior.
In scenarios where an upgrade fails due to issues such as bad IP assignment, ICMP pings being blocked, or stack members not being online, an event will be logged under Network-wide > Event log. This event indicates the specific reason for the upgrade failure, helping to identify and troubleshoot the problem.

Downgrading from Cloud Management with IOS XE is Restricted
Due to complexities in restoring the container-based architecture, downgrades from Cloud Management with IOS XE to any prior CS firmware via the dashboard is restricted. A factory reset may be required and support assistance will be necessary. Consider this before upgrading your production network to the cloud management with IOS XE version.
It may take up to one day to assign a support team to handle a downgrading request. Expect possible delays beyond the usual response time.
Onboarding your CLI/DNA-managed Catalyst
After migrating to Cloud Management, note that remote access (serial console and SSH) are no longer available. All management access can now be accessed through the cloud dashboard or the local status page via the rear management port.
Migrating a Layer 2 (L2) & Layer 3 (L3) Switch
For detailed instructions and recommendation on migrating a Layer 2 and a Layer 3 Switch from CS firmware to IOS XE firmware, please refer to Migrating Switches From CS Firmware to IOS XE Firmware
Migrating a Switch Template
Migrationg a switch template with bound networks is not directly supported. The recommendation is to migrate networks one at a time into a new template using the following procedure
Step 1: Preparation
Prep (Create a second configuration template)
-
Organization->Configuration Templates
-
“Create a new template”
-
“Copy settings from” choose source template
-
Organization->Firmware Upgrades
-
Upgrade new template to 17.15.x (latest 17.15 GA) for CS firmware, leave MS firmware the same
-
“Acknowledge the firmware upgrade checkbox” and enter your name
-
“Perform the upgrade now”
-
Wait 10-15 minutes for the new empty template network to upgrade to the latest firmware version.
-
Verify new template is at the correct firmware version and switch template port mappings are correct
Step 2: Unbind Networks
Note: Unbinding a network preserves current active network-module
-
Organization->Configuration Templates
-
Select Source Template
-
Choose networks in template and click “unbind”
-
Choose “Unbind and Retain Configurations”
-
Confirm “Yes, unbind template and retain configurations”
Step 3: Upgrade the Unbound Networks (optional)
Note: This phase can be skipped, but is recommended to allow for rollback and staged-upgrades if needed
Upgrade Networks before rebinding
-
Organization->Firmware Upgrades
-
Upgrade unbound networks to 17.15.x(latest 17.15GA)
-
Staged upgrades/scheduling can be done at this point
Step 4: Rebind Networks to New Template
Note: Networks not upgraded to match template will upgrade during binding
Note: That rebinding switches to templates will lose port-overrides, layer3 interfaces etc
-
Organization->Configuration Templates
-
Select Destination template
-
Select "Bind additional networks" and select your network to re-bind
-
Changes in Behavior
MS / CS / IOS XE Uplink Selection Differences
![]()
|
Feature |
MS / CS |
IOS XE 17.15.4.1 17.18.1 17.18.2 |
IOS XE 17.15.5 |
|
VLAN Discovery |
|
|
|
|
VLAN Interfaces |
|
|
|
|
IPv4/IPv6 address assignment |
|
|
|
|
Interface Scoring |
|
|
|
|
ARP Prober |
|
|
|
|
Compute best uplink |
|
|
|
|
Cause for re-compute best uplink |
|
|
|
|
Rescoring (for recomputing best uplink) |
|
|
|
|
DNS |
|
|
|
MS / CS / IOS XE Config Updater, Config Monitor Differences
|
Feature |
MS / CS |
IOS XE 17.15.4.1 17.18.1 17.18.2 |
IOS XE 17.15.5 |
|
Config Fetch for Nextunnel |
|
|
|
|
Connection Monitor |
|
|
|
|
Config Updater |
|
|
|
|
Config Rollback |
|
|
|
Uplink Auto Configuration (UAC)
Uplink Auto Configuration facilitates automatic identification of uplink interfaces and provides connectivity to Meraki Dashboard, eliminating the need for manual configuration of the switch. UAC supports new and existing deployments to ensure connectivity to Meraki Dashboard. UAC selects the uplink interface, connects to dashboard, and maintains the uplink connectivity. UAC provides reduced manual configuration effort, improved device management, easier device deployment, increased network scalability, and improved network reliability. UAC is implemented as a IOSd subsystem to utilize features like vlan-stats, ARP probes, and ping probes (depending on version listed above) for better performance and scale.
UAC Requirements:
Note: UAC Auto Fallback feature is available in IOS XE 17.15.4.1+.
Network
Underlying network has connectivity to Dashboard
DHCP server in the network or user assigning ip addresses
DNS server available & reachable from the device
Minimum 60 packets per 2 minutes on an active/uplink VLAN
New Deployments
Port in trunk mode
L2 VLAN configured
DHCP on an Uplink VLAN
DNS server availability
Existing Deployments
L2 VLAN configured
At least one path to reach Dashboard working
IP address assignment to SVI (DHCP or static)
DNS server configured/available and reachable through default gateway
UAC Uplink Selection
When the switch is powered on, UAC will attempt to identify any active VLANs in the network using data plane vlans-stats for frames the switch receives. If any VLAN receives more than 60 frames in 2 minutes then UAC will mark those as active VLANs. Once UAC has a list of active VLANs it will start to validate them as a potential uplink interfaces starting with the first active VLAN that received 60 or more frames within 2 minutes. UAC will configure an L3 SVI interface and enable DHCP to check if the SVI obtains IP address information. UAC will then go through each active VLAN that has a L3 capable SVI and will start testing each one serially. UAC will attempt to verify if a layer 3 gateway was received as part of the DHCP offer. If it was then UAC will test the gateway by issuing an ARP gateway probe in 17.15.5. If the ARP gateway probe is successful then that L3 SVI will be chosen as the uplink interface to Meraki Dashboard. Once this process has completed UAC will add the appropriate Dashboard routes and will bring up the encrypted tunnel to Meraki Dashboard for management.
For versions 17.15.4.1, 17.18.1, and 17.18.2 UAC will test the gateway by issuing an ARP probe and if successful will then will attempt to ping the gateway address. If both of those are successful, UAC will then attempt to ping catalyst.meraki.com. If that is successful then that L3 SVI will be chosen as the uplink interface to Meraki Dashboard. Once this process has completed UAC will add the appropriate Dashboard routes and will bring up the encrypted tunnel to Meraki Dashboard for management.
Preferred Uplink
For cloud managed Catalyst switches running IOS XE 17.15.5, once the switch has been deployed, if there is a preferred uplink chosen, UAC will start with that as the uplink interface. There could be instances when the user selected preferred uplink isn't being used. This could be due to the following reasons: gateway ARP probe failure, not enough traffic being generated on the preferred VLAN when the switch was brought online initially, DHCP server not reachable, etc. If UAC switches to different uplink interface due to ARP gateway probe failure, UAC will switch back over to the selected preferred uplink automatically once the ARP gateway probe is successful. UAC will continue to monitor the uplink interface via ARP gateway probes . If for some reason there is an issue where the ARP gateway probe has 3 failures UAC will automatically failover to the interface with the next highest score.
For cloud managed Catalyst switches running IOS XE 17.15.4.1, 17.18.1, or 17.18.2 once the switch has been deployed, if there is a preferred uplink chosen, UAC will start with that as the uplink interface. There could be instances when the user selected preferred uplink isn't being used. This could be due to the default gateway not reachable, DNS not resolving, unable to ping catalyst.meraki.com, not enough traffic being generated on the preferred VLAN when the switch was brought online initially, DHCP server not reachable, etc. If for any reason UAC switches to a different uplink from the selected preferred uplink, UAC will NOT switch back over to the selected preferred uplink automatically. There would have to be an issue impacting the existing uplink's connectivity to Dashboard in order for UAC to switch over to the user selected preferred uplink. This is to limit potential flapping of tunnel interfaces to Dashboard. UAC will continue to monitor the uplink interface every two minutes via ARP and ping probes . If for some reason there is an issue impacting connectivity to Meraki Dashboard, after 5 minutes, UAC will attempt to select another uplink interface in order to restore connectivity to Dashboard.
Configuring a switch's default routing table with uplink interface and gateway centralizes path selection for both local and downstream devices.
Key operational impacts include:
- Management Integration: For cloud-managed Catalyst switches (running IOS XE), the management interface is integrated with the Layer 3 uplink interface, meaning Meraki Dashboard connectivity uses the default routing table directly. If a preferred uplink fails or has connectivity issues reaching Meraki Dashboard, the switch can utilize a secondary path. This is accomplished by UAC injecting Meraki Dashboard specific routes in the routing table via the uplink interface. The UAC configured routes can differ from the user-defined default gateway. This allows management traffic to route through a backup uplink in the event the primary internet path cannot reach Meraki Dashboard.
- Downstream Connectivity: Meraki devices downstream that use this primary switch as their default gateway will inherit its routing logic. If the primary switch has a valid path to the Internet/Meraki Dashboard, the downstream switches will use that same path to maintain their own cloud connectivity.
- Layer 3 Behavior: When L3 routing is initialized, the first IPv4 and or IPv6 interface requires a default gateway. This entry creates a default route in the routing table (0.0.0.0/0) to forward all traffic not matching local subnet's or static routes to the designated next-hop.
- MS and CS Behavior: On MS and CS switches, management traffic for Meraki Dashboard communication typically uses a configured management IP and its own gateway, distinct from client-facing L3 routed interfaces.
For configuration, you can manage these settings in the Meraki Dashboard under Switching > Configure > Routing & DHCP.
UAC Automatic Fallback to Preferred Uplink (IOS XE 17.15.4.1, 17.181, and 17.18.2)
UAC may choose a uplink interface other than the preferred uplink in cases where upstream connectivity has been disrupted. UAC fallback is a feature that, when enabled, will periodically check the health of the preferred uplink. Once the preferred uplink is considered healthy, UAC will automatically fall back to the preferred uplink without any manual intervention.
To enable the Auto Fallback feature simply navigate to Switching, Configure, Switch Settings and select the check box next to "Automatically fallback to preferred uplink when available" and then click "Save changes".

UAC Manual Fallback to Preferred Uplink (All IOS XE firmware versions)
Customers who do not want to enable the UAC Automatic Fallback to Preferred Uplink feature will still have the option to force UAC to recheck the uplink interfaces and attempt to fail over to the preferred uplink manually. This can be done via the Switching, Switches, Switch Summary page. The "Recheck uplinks" button is located on the left side pane on the Switch Summary page.

UAC Allow List (IOS XE 17.15.5, 17.18.2)
Customers who want to have control over which interfaces UAC selects for uplink consideration will be able to opt into the Allow List feature by navigating to Organization, Early Access. Once on the Meraki Early Access Program page look for the feature UAC Allow List and "opt in".
Once you have opted into UAC Allow List, you will then navigate to Switching, Switch Settings Page to enable the feature.

When enabling this feature, by default only the configured preferred uplink will be allowed. Prior to enabling, ensure the switch is connected to Dashboard with the configured preferred uplink interface in order to avoid any connectivity issues connecting to Dashboard.
When enabling this feature, all compatible switches running IOS-XE 17.15.5 and 17.18.2 will have Allow List enforced.
In order to configure additional interfaces for UAC to include in the uplink selection process, navigate to Switching, Routing & DHCP page. Select the interface you want to include, navigate to the management connectivity section in the interface editor and select the Candidate uplink check box, then click Save changes.

UAC requires a route within the routing table in order to properly select an interface for uplink connectivity. In order to support candidate uplink interfaces when Allow List is enforced it is required to have a corresponding static route configured for that candidate interface.

If there are no candidate uplink interfaces configured when Allow List is enabled, UAC will only use the preferred uplink for Dashboard connectivity and will not attempt to select an alternate interface if the configured preferred uplink has connectivity issues to Dashboard.
When you change your preferred uplink, the previous uplink is removed from the Allow List. To use it again as a candidate uplink, you must manually re-add it.
Cloud CLI allows users to view the current uplink interface, configured preferred uplink, and any candidate interfaces when allow list is enabled.

Management Interface Architecture
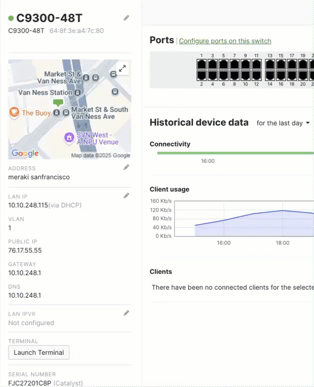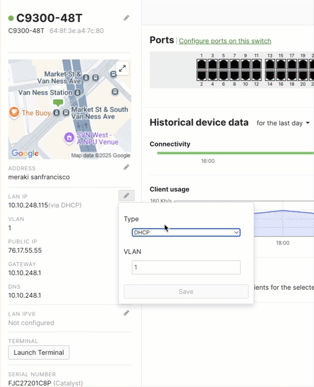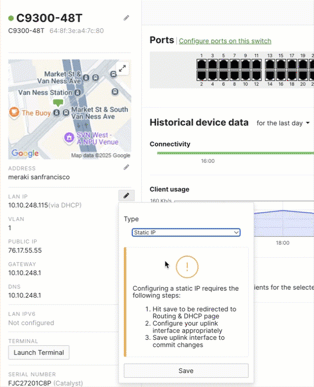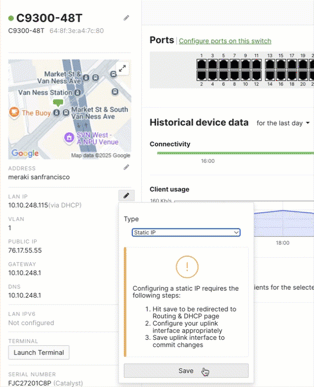
The management interface is now a Layer 3 (L3) interface. Previously, switches running CS firmware needed a specific management IP address. Now, management is handled by any L3 interface. All settings related to management connectivity and L3 interfaces can now be found on the Routing & DHCP page. For switches that only support Layer 2 (L2), DHCP functionality is available, but enabling L3 functionality requires setting a static management IP address first.
Watch this video to learn more about this change.

Step-by-step guide to configure a switch with Static IP
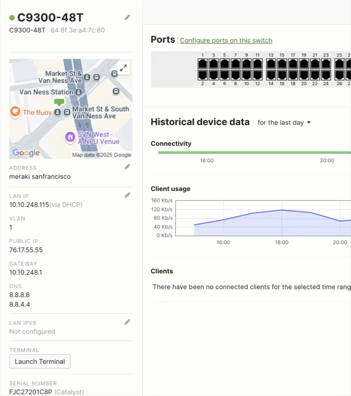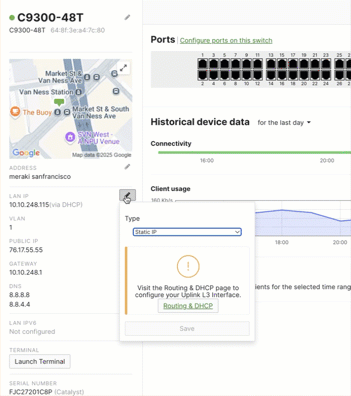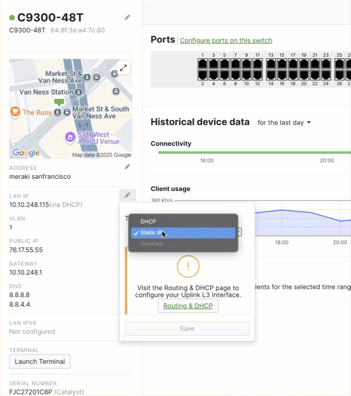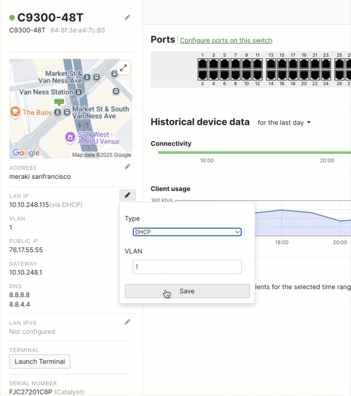
- Navigate to your switch details side bar.
- Set the option to “Static IP”.
.gif?revision=1&size=bestfit&width=434&height=535)
- You will be automatically redirected to the Router & DHCP page.
- On the Router & DHCP page, create a new Layer 3 (L3) Interface.
- Select "V4 Uplink" to designate this interface as the uplink.
.gif?revision=1&size=bestfit&width=740&height=611)
- To change back to DHCP, go to the Switch Details Side Bar.
- Change the setting from "Static IP" back to "DHCP."
.gif?revision=1&size=bestfit&width=409&height=462)
Step-by-step guide to change your uplink L3 interface
- Either create a new L3 interface or choose an existing one.
- Select “V4 Uplink”.
- Enter the required Gateway and DNS values.

Default Port Modules
Upgrading to the Cloud Management with IOS XE 17.1x.x firmware simplifies the network module configuration. When a module is not installed, the configuration is consolidated into eight default ports. Once a network module is installed, these ports are automatically mapped to the appropriate interfaces. Previously, each potential network module required its own unique configuration. For instance, configuring a 48-port switch required configuring 98 ports to accommodate every possible module. Now, there are only 56 ports (48+8) needed to support both current and future modules.
Watch this video to learn more about this change.

Safe-Config and Rollback
When upgrading to the Cloud Management with IOS XE firmware, if your switch fails to come online after transitioning from CS firmware, it will automatically revert to the CS/Container firmware after a period of 2 hours.
It is important not to reboot or factory reset the switch during this 2-hour window, as this may corrupt the rollback configuration and hinder the switch's recovery and will ultimately corrupt the rollback configuration. If, after 2 hours, the switch has not recovered or connected to the dashboard, contact support. Once the switch has successfully recovered, it will not attempt the upgrade again for another 2 hours.
Additionally, if the switch successfully upgrades to the Cloud Management with IOS XE firmware, ensure it remains online and connected for 30 minutes following the upgrade. This duration allows the configuration to be marked as safe and committed.
ROMMON Recover / Behavior
Rommon access is different than traditional Catalyst while in Cloud Managed mode. Please note the following behavior differences
- You cannot break into "ROMMON" by using the "Mode" button on boot. Mode button is used for factory-defaulting after the switch is booted and button held for an appropriate duration.
- As of IOS XE 17.15, devices that crash or fail booting 5 times in a row will temporarily unlock console access and drop into ROMMON mode for user recovery. Once the switch is recovered and reconnected to Dashboard, ROMMON console access is will be disabled.
Layer 3 SVI Behavior
Prior to Cloud Management with IOS XE, Layer3 Meraki switches required at least two IP addresses, one for the management IP and a second for the Layer3 Switch Virtual Interface (SVI). You cannot route traffic through the management-IP, it essentially worked as an out-of-band management interface. In Cloud Management with IOS XE, the Meraki management interface is now combined with a Layer 3 uplink SVI, using one single IP address, rather than two.
To use Layer3 SVI's with Cloud Management with IOS XE, the following requirements/conditions apply:
- The management/uplink SVI must be configured for a static IP address. It's highly recommended to configure your management interface to use a static IP address prior to upgrading.
- If you upgrade from Container-based (CS) firmware to Cloud Management with IOS-XE be aware of the following:
- If you have the management interface on the same VLAN as a configured L3 SVI, the SVI IP address will override the management interface address, and the management interface IP address will be erased. This is done to attempt to preserve L3 routability in the network, but may result in the loss of management traffic such as SNMP or RADIUS when the management IP address changes. For example:
- Management interface has a static IP of 10.10.10.100 on vlan 10
- There is also an SVI on VLAN 10 configured for 10.10.10.200.
- After the upgrade, the switch will use 10.10.10.200.
- If you have the management interface on a unique VLAN with no overlapping SVI, then the management interface will become a new uplink SVI.
- If your management IP is configured for DHCP, you be required to assign a static IP address to the uplink SVI before other L3 SVIs can be created. Static addressing is considered a Cisco best practice for Layer 3 switch deployments.
- If you have the management interface on the same VLAN as a configured L3 SVI, the SVI IP address will override the management interface address, and the management interface IP address will be erased. This is done to attempt to preserve L3 routability in the network, but may result in the loss of management traffic such as SNMP or RADIUS when the management IP address changes. For example:
Spanning Tree Changes
Spanning-Tree Protocol (STP) behaves differently in Cloud Management with IOS XE 17.15.1 onwards.
- CS17 and Cloud Management with IOS XE 17.15.1+ exhibit different behaviors in their handling of Spanning Tree Protocol (STP).
- Cloud Management with IOS XE runs Multiple Spanning Tree Protocol (MSTP) with PVST simulation enabled and changes the MSTP region identifier to the switch's MAC ID.

-
For spanning-tree root bridges, MSTP is preferred and remains compatible with Rapid-PVST+ as long as VLAN 1 is allowed on the trunk. If VLAN 1 is not configured on the uplink, the downstream Cloud Management with IOS XE/MSTP switch will become the root for all VLANs.
DHCP Behavior
DHCP pool configurations with fixed IP bindings must have the static binding deleted prior to modifying the size of the subnet for the DHCP pool. This will avoid any errors when pushing the configuration to the switch from Dashboard.
Workflow for changing a DHCP subnet with fixed IP bindings
- Navigate to the interface: Go to
Switching > Configure > Routing & DHCPand edit the SVI interface. - Delete existing fixed IP bindings: In the DHCP settings section for that interface, remove any fixed IP bindings that were associated with the previous subnet. You can re-create these later with valid addresses if needed.
- Modify the subnet: Change the subnet to the new, desired size (e.g., from
/24to/28). - Save the configuration: Once saved, the configuration will be successfully pushed to the device.
- Add new fixed IP bindings (if needed): You can now navigate back to the interface add new fixed IP assignments that fall within the new, smaller subnet.
LED Behavior
The system LED on the switch indicates the system status, including the progress of booting and connecting to the Meraki dashboard without logging in into the system or Dashboard. The MS390 switch has a rainbow system LED to indicate the system state. This rainbow LED is not available on Catalyst 9000 hardware. Blue Beacon LED button and the System LED are instead used on Catalyst 9000 hardware to indicate the system status.
- Cloud Management IOS XE firmware continues to use the rainbow LED in the MS390 and Blue Beacon and system LEDs in Catalyst 9000 to provide system status.
-
For the LED behaviour of cloud-managed Catalyst 9000 switches refer to the table in our Catalyst 9300/X/L-M Series Installation Guide. It stays the same in the Cloud Management with IOS XE firmware.
-
For the LED behaviour of MS390 refer to our documentation on MS390 Series Installation Guide. However, Cloud Management with IOS XE with MS390 adds two additional stages (taken from Catalyst 9000), described below:
-
|
MS390 Stage |
Rainbow LED |
Comments |
|---|---|---|
|
System error: Switch failed to complete local provisioning |
Solid Amber |
New LED Scheme |
|
There is a fault with the power supply, fan, or network module (not traffic-related) |
Alternatively blinking Amber and White |
New LED Scheme |
Unsupported features on IOS XE 17.15.x with cloud configuration
The following features are not available in Cloud Management with IOS XE. Future releases will address these features.
Refer to the Cloud Configuration: Release Versions and Highlights page, which lists the supported features on 17.18.x.
-
SmartPorts
-
MAC Blocklist
-
Digital Optical Monitoring (DOM)
-
RSPAN / VLAN SPAN
-
IPv6 RA Guard / DHCP Guard
-
HTTP Proxy
-
Sticky MAC
-
Dynamic ARP Inspection (DAI) Auto-Uplink
-
Netflow on IPv6
-
SecurePort
We value your feedback on our latest release! Take a moment to complete this brief 5-minute survey and share your experience with us.
What's next? Watch this in-depth session recording to learn more about this new architecture and get an exclusive preview of future advancements.
Configuration: Device
Introducing the public general availability of cloud-managed Catalyst with device configuration for Cisco Catalyst 9200/9300/9500 series switches running IOS XE 17.15.3 or later. This is the enhanced upgrade replacement to Cloud Monitoring for Catalyst switching.
Cloud Management with device configuration enables Catalyst 9000 series switches to be managed in the Meraki dashboard, providing an integrated view into device details, status, configuration, metrics, events and alerts; perform remote diagnostics and troubleshooting; and make configuration changes. Utilizing Cloud Management with IOS XE - configuration source: device, cloud managing Catalyst switches is now simpler and more efficient than ever.
Key highlights
- Cloud Management with device configuration is the evolution of Cloud Monitoring for Catalyst
- Dashboard-based onboarding experience (no application required). Learn more about this onboarding experience here
- Significant cloud connectivity benefits over Cloud Monitoring
- Write-capable Cloud CLI, to modify switch configuration directly from dashboard, with session and change logging. Learn more
- Intelligent packet capture
- Alert hub integration
- Syslog event logging
- Support for regional clouds: Meraki India, Meraki China, and Meraki Canada
- Note for Meraki China: Intelligent packet capture and standard packet captures are currently not supported for Catalyst switches running IOS XE in the Meraki China region. Support for Intelligent packet capture is planned for a future update.
Supported Hardware Models (Configuration: Device)
A full list of supported hardware can be found here.
- Switches labeled with -M, such as the C9300-M, are fully cloud-managed and do not require onboarding. Claim them like any Meraki device using the Cloud ID physically labeled on the device
- Leverage the new in-dash flow if your switches are currently on Cloud Monitoring and need to be upgraded to cloud management with device configuration. For more information, please refer to documentation here.
Supported IOS XE Software
Cloud Management with device configuration is supported on Catalyst switches running IOS XE version 17.15.3 and above.
Licensing
Catalyst switches require an active DNA Essentials or Advantage license. Traffic analytics and application-level visibility are only available in Dashboard for switches that have a DNA Advantage license.
Cloud Connectivity
Switches operating in Cloud Management communicate with dashboard similarly to other cloud-connected switches, using TCP 443 on specified subnets.
Ensure that outgoing firewall rules allow connections from switches to connect to the cloud at the following destination subnets on TCP 443:
209.206.48.0/20
216.157.128.0/20
158.115.128.0/19
Migration and Upgrade Paths
|
Category |
Product |
Path |
|---|---|---|
|
Onboarding Catalyst switches with device configuration to Meraki Cloud |
C9200 and C9300 series switches |
Follow the process documented in Enable Cloud Management for Catalyst Switches with Device Configuration. |
|
Upgrading cloud-monitored switches to cloud Management with device configuration |
C9200, C9300 and C9500 series switches |
Switches must be removed from Cloud Monitoring for Catalyst before being enabled for cloud management with device configuration. Click here for details. |
|
Converting a cloud-managed Catalyst switch from device configuration to cloud configuration |
C9200, C9300, C9500H* series switches |
Remove the switch with device configuration from its Dashboard network and then follow the process at Enable Cloud Management for Catalyst Switches with Device Configuration. |
* Please note, C9500H refers to C9500-48Y4C, C9500-24Y4C, C9500-32C, and C9500-32QC which can be managed in either cloud config (17.18.1+) or device config mode (17.15.3+).
For more details, refer to the FAQs.
Unsupported Features and Known Issues
- When port-channel 0 is used as the uplink connection to Dashboard from the switch, details about this aggregation interface are not visible in Dashboard.
- Each interface will report a maximum of 1,000 clients to Dashboard.
- An active application hosted on a Catalyst switch may prevent the initial onboarding from completing successfully. As a workaround, the application can be disabled until onboarding has completed.
Key Updates to Cloud Monitoring for Catalyst Switches
Cloud-managed Catalyst with device configuration (on IOS XE 17.15.3 and above) is the recommended upgrade path for all Cloud Monitoring for Catalyst switches. Starting May 1, 2025, no new organizations will be permitted to onboard switches to the Cloud Monitoring for Catalyst service. Effective November 1, 2025, no additional switches will be permitted to onboard.
Service on Cloud Monitoring for Catalyst is expected to terminate on January 31, 2026. After this date, switches which have not migrated from Cloud Monitoring to cloud-managed mode with device configuration will lose dashboard connectivity, but all switching functions will continue to operate locally.
Benefits of Upgrading to Cloud Managed mode with device configuration
Cloud management with device configuration for switches on IOS XE 17.15.3+ offers the same Cloud Monitoring functionality, plus additional features:
- Dashboard-based onboarding experience (no onboard application required).
- Cloud CLI, a fully interactive CLI terminal hosted right in the cloud dashboard for your IOS XE Catalyst switches. In cloud management mode with device configuration, Cloud CLI offers the option to enable write access to modify switch configuration via CLI directly in Dashboard.
- Intelligent packet capture.
- Alert hub integration.
- Syslog event logging.
- Integrated software image/firmware upgrade capability (coming soon).

