Cisco Security Applications with Systems Manager for Hybrid Home Office Work Deployments
Cisco Security Applications with Systems Manager for Hybrid Home Office Work Deployments
Cisco Meraki Systems Manager MDM can be used to remotely deploy & configure Cisco apps on managed devices. Managed devices can be both organization-owned and/or end-user owned. This means devices can be moving between a physical personal home and a physical office setting. For this hybrid setting, Meraki Systems Manager device management combined with Cisco app's security enables some of the most powerful management options in the industry.

As part of the Cisco Hybrid Work Software offer, there are many integrations between Meraki Systems Manager and other Cisco applications to enhance device's security and visibility. Learn more about the Cisco Hybrid Work Software offer here.

This guide will cover a high level overview for how to deploy the following Cisco secure software on Meraki Systems Manager enrolled devices:
- AnyConnect
- Duo
- Secure Endpoint
- ThousandEyes
- Umbrella
- Webex
Note: This is a living document which will be updated as additional enhancements and recommendations between Meraki Systems Manager and Cisco apps becomes available in the future.
Systems Manager deployment design considerations
Meraki Systems Manager can be used to push Cisco apps & their configurations to managed devices. Management means the devices are enrolled into the Meraki Systems Manager network. Optionally add enrollment authentication and enhance enrollment security and track end-user's identities on enrolled devices-- and even optionally add Duo as a 2FA prompt as part of initial device enrollments!
Managed devices can be both organizational owned devices or end-user owned devices:
Organization owned devices
Devices owned by your business/organization obtain additional benefits and security. The huge benefit to organizational owned device is they will automatically enroll upon initial setup and persist enrollments upon factory resets. This maintains the ownership of the devices owned by your company and makes it nearly impossible to lose a device. These also allow additional automatic device provisioning settings to gain more powerful management options, such as Supervision for Apple devices and Device Owner enrollment for Android devices. Maintain ownership of company-owned devices by integrating Systems Manager with the following vendor automatic enrollments:
-
Apple Automated Device Enrollment (iOS/iPadOS, tvOS, and macOS)
-
Windows Autopilot (coming soon)
End-user owned devices (BYOD)
End-users can self-enroll their own devices via the Meraki enrollment portal. This method of enrollment is recommend for devices which are not owned by your organization and where device management is still desired.
If wireless access point is a Meraki MR, a Sentry enrollment splash page could be used to encourage device BYOD enrollment before being authorizing device through the splash page.
Note: There are less management powerful management options on BYOD managed devices to protect end user's device and privacy. OS vendors enable more actions available for management on organization owned devices (e.g. Supervised Apple devices and Device Owner Android devices).
Cisco SecureX

Cisco SecureX delivers a consistent experience across your all of your products. Bring all of the products within this document into a unified experience via SecureX. Get unified visibility, intuitive automation, and robust security for your entire security portfolio in one place. Meraki Systems Manager has unique integrations with the Cisco SecureX portal to send Systems Manager MDM device information to SecureX via the Device Insights module. This will make Systems Manager's MDM information easily viewable along side all the other Cisco Security platforms. To learn more click here.
Cisco Security Connector

The Cisco Security Connector is a network extension app which Systems Manager enrolled devices can leverage to enable Cisco Umbrella DNS and Cisco Clarity (Secure Client) Content Filter for iOS/iPadOS devices. Enable these Cisco products with full device or per app protection and visibility. For more information, view the Cisco Security Connector with Systems Manager deployment guide.

iPadOS device protected with Cisco Umbrella DNS Security and Cisco Clarity Secure Endpoint Visibility configured remotely at scale with Cisco Meraki Systems Manager.
Cisco Secure Client

The Cisco Secure Client can be used to enable AnyConnect VPN, Umbrella DNS, Secure Endpoint, and much more (depending on operating system) within the Cisco Security Suite. See the steps below for how to configure each operating system managed within Systems Manager. For additional information, please review the official Cisco Secure Client documentation as there are many different ways to configure the Cisco Secure Client application and its various Cisco modules. Please review some of the working examples for each operating system below:
Android
On Android, the Cisco Secure Client app can be used to enable AnyConnect VPN and Umbrella DNS security for managed devices. Use a Managed App Config to configure the desired settings for the Cisco Secure Client application.

For information on how to enable Cisco Umrella DNS protection for Android devices managed with SM, view the documentation here.
For information on how to enable Cisco AnyConnect VPN for Android devices managed with SM, view the documentation here.
iOS/iPadOS
On iOS and iPadOS, the Cisco Secure Client app can be used to enable Cisco AnyConnect VPN. Use a VPN payload set to "Cisco AnyConnect" to configure the desired settings for the Cisco Secure Client application. In the example below, a certificate is used for the authentication which is also installed via Systems Manager.
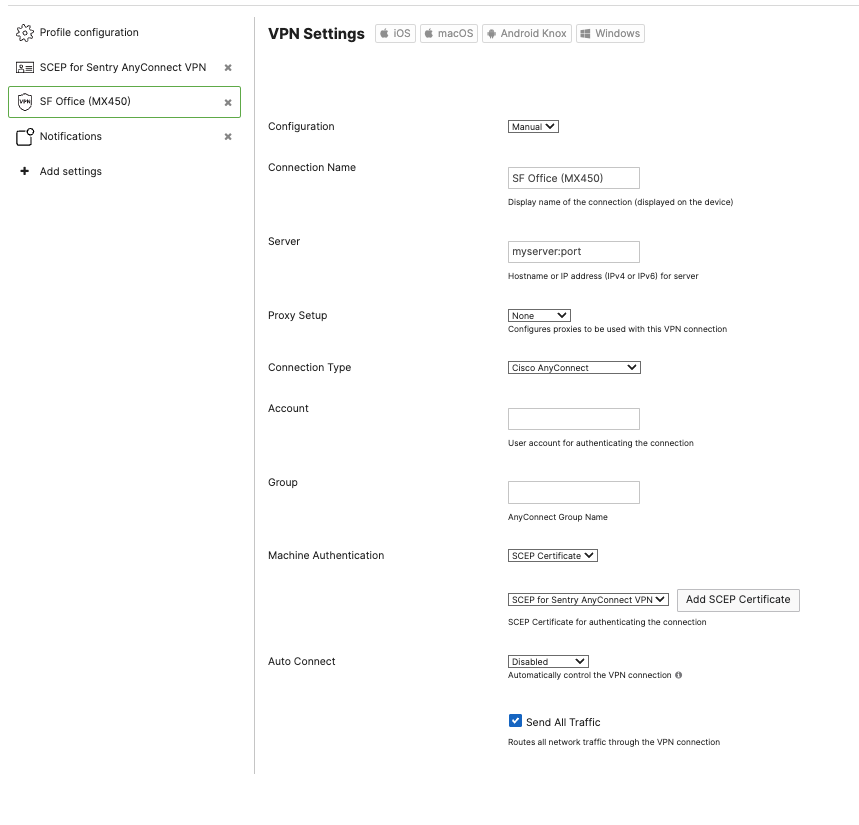
For more information, please review the Cisco AnyConnect documentation.
macOS
Deploy the Cisco Secure Client to managed macOS devices. This can be used to enable Umbrella DNS, AnyConnect VPN, and much more within the Cisco Security suite.
Upload the desired .dmg version on the SM > Apps page as a custom app.
Note: For the macOS application, you will need the Privacy Preference Policy Control profile and Kernel/System Extensions payloads to suppress end user permission prompts (or else end users will need to explicity grant permission). You can also upload this as a custom profile if you have a .mobileconfig of this. Please refer to Secure Client application (in the event that these permissions change), however a known working .mobileconfig for these permissions is:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN"
"http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>PayloadContent</key>
<array>
<dict>
<key>AllowUserOverrides</key>
<true/>
<key>AllowedKernelExtensions</key>
<dict>
<key>DE8Y96K9QP</key>
<array>
<string>com.cisco.kext.acsock</string>
</array>
</dict>
<key>PayloadDescription</key>
<string></string>
<key>PayloadDisplayName</key>
<string>AnyConnect Kernel Extension</string>
<key>PayloadEnabled</key>
<true/>
<key>PayloadIdentifier</key>
<string>37C29CF2-A783-411D-B2C7-100EDDFBE223</string>
<key>PayloadOrganization</key>
<string>Cisco Systems, Inc.</string>
<key>PayloadType</key>
<string>com.apple.syspolicy.kernel-extension-policy</string>
<key>PayloadUUID</key>
<string>37C29CF2-A783-411D-B2C7-100EDDFBE223</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
<dict>
<key>AllowUserOverrides</key>
<true/>
<key>AllowedSystemExtensions</key>
<dict>
<key>DE8Y96K9QP</key>
<array>
<string>com.cisco.anyconnect.macos.acsockext</string>
</array>
</dict>
<key>PayloadDescription</key>
<string></string>
<key>PayloadDisplayName</key>
<string>AnyConnect System Extension</string>
<key>PayloadEnabled</key>
<true/>
<key>PayloadIdentifier</key>
<string>A8364220-5D8D-40A9-Af66-1Fbfef94E116</string>
<key>PayloadOrganization</key>
<string>Cisco Systems, Inc.</string>
<key>PayloadType</key>
<string>com.apple.system-extension-policy</string>
<key>PayloadUUID</key>
<string>A8364220-5D8D-40A9-Af66-1Fbfef94E116</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
<dict>
<key>Enabled</key>
<true/>
<key>AutoFilterEnabled</key>
<false/>
<key>FilterBrowsers</key>
<false/>
<key>FilterSockets</key>
<true/>
<key>FilterPackets</key>
<false/>
<key>FilterType</key>
<string>Plugin</string>
<key>FilterGrade</key>
<string>firewall</string>
<key>PayloadDescription</key>
<string></string>
<key>PayloadDisplayName</key>
<string>Cisco AnyConnect Content Filter</string>
<key>PayloadIdentifier</key>
<string>com.apple.webcontent-filter.339Ec532-9Ada-480A-Bf3DA535F0F0B665</string>
<key>PayloadType</key>
<string>com.apple.webcontent-filter</string>
<key>PayloadUUID</key>
<string>339Ec532-9Ada-480A-Bf3D-A535F0F0B665</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>FilterDataProviderBundleIdentifier</key>
<string>com.cisco.anyconnect.macos.acsockext</string>
<key>FilterDataProviderDesignatedRequirement</key>
<string>anchor apple generic and identifier
"com.cisco.anyconnect.macos.acsockext" and (certificate
leaf[field.1.2.840.113635.100.6.1.9] /* exists */ or certificate
1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate
leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate
leaf[subject.OU] = DE8Y96K9QP)</string>
<key>PluginBundleID</key>
<string>com.cisco.anyconnect.macos.acsock</string>
<key>UserDefinedName</key>
<string>Cisco AnyConnect Content Filter</string>
</dict>
</array>
<key>PayloadDescription</key>
<string></string>
<key>PayloadDisplayName</key>
<string>Approved AnyConnect System and Kernel Extensions</string>
<key>PayloadEnabled</key>
<true/>
<key>PayloadIdentifier</key>
<string>A401Bdc2-4Ab1-4406-A143-11F077Baf52B</string>
<key>PayloadOrganization</key>
<string>Cisco Systems, Inc.</string>
<key>PayloadRemovalDisallowed</key>
<true/>
<key>PayloadScope</key>
<string>System</string>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadUUID</key>
<string>A401Bdc2-4Ab1-4406-A143-11F077Baf52B</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
</plist>
For more information on deploying Cisco Secure Client and its various Cisco modules, please see the official deployment documentation.
Note: Additional configurations and customizations can happen via shell scripting in Systems Manager for the Secure Client's profile.xml or umbrella.json config, for example.
Windows
Deploy the Cisco Secure Client to managed Windows devices. This can be used to enable Umbrella DNS, AnyConnect VPN, and much more within the Cisco Security suite.
Upload the desired .msi version on the SM > Apps page as a custom app.
For more information on deploying Cisco Secure Client and its various Cisco modules, please see the official deployment documentation.
Note: Additional configurations and customizations can happen via Powershell scripting in Systems Manager for the Secure Client's profile.xml or umbrella.json config, for example.
Webex

Cisco Webex can be deployed and configured remotely by Meraki Systems Manager on Android, iOS/iPadOS, macOS, and Windows. For more information, please review the Cisco Webex deployment documentation. See the steps below for the basic settings to configure each operating system:
Android
Meraki Systems Manager can configure Webex on managed Android devices. Use a Managed App Config to configure the desired Webex app settings for the SM managed devices in bulk. orgIdentifier is necessary to configure your exact Webex organization on the managed devices and can be customized with additional keys/values from there. For more information, please review the Webex mobile deployment documentation.

iOS/iPadOS
Webex deployed on iOS/iPadOS. Use a Managed App Config to configure the desired Webex app settings for the SM managed devices in bulk. orgIdentifier is necessary to configure your exact Webex organization on the managed devices and can be customized with additional keys/values from there. For more information, please review the Webex mobile deployment documentation. 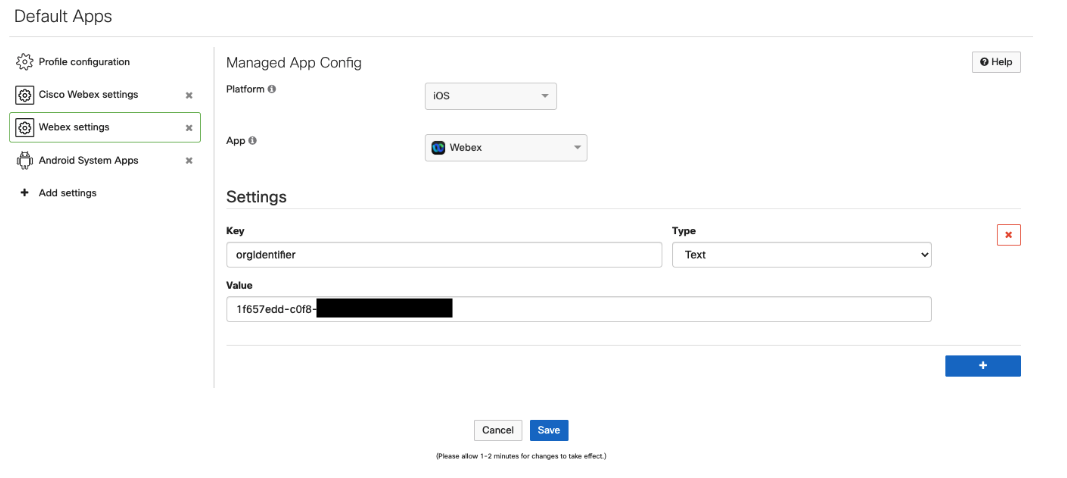
macOS
Webex deployed on Windows 10 and 11 devices. On the SM > Apps page add a custom app with the Webex Teams .dmg installer.
For more information and additional configuration keys for installations and upgrades, please review the official Webex deployment documentation.
Windows
Webex deployed on Windows 10 and 11 devices. On the SM > Apps page add custom app with the Webex Teams .msi installer. 
Add installation arguments to customize the installation based on the desired settings. For example, add this as an installation argument:
INSTALL_ROOT="C:\Program Files" ALLUSERS=1
This will make the app install for all users inside the C:\Program Files directory so it can run for all users. For more information and additional configuration keys for installations and upgrades, please review the official Webex deployment documentation.
Duo

Duo can be configured in a few ways with Meraki Systems Manager. On managed mobile devices (iOS/iPadOS and Android) Systems Manager can configure these clients to be a Duo Trusted Endpoint. On managed desktop platforms (macOS and Windows) Systems Manager can deploy the Duo Device Health Application and necessary certificates.
Duo can also be used for an additional layer of authentication to portal.meraki.com and enroll.meraki.com. And Duo can also be used to enable Trusted Endpoints feature:
- Duo Trusted Endpoints with Meraki Systems Manager
-
Duo used for 2FA on portal.meraki.com and enroll.meraki.com portals via SAML
Android
Meraki Systems Manager can configure Duo Trusted Endpoint for managed Android devices. Use a Managed App Config to configure the desired Duo app settings. trustedEndpointConfigurationKey is necessary to configure your exact trusted endpoint access on the managed devices. trustedEndpointIdentifier set as the Device: ID is useful to track devices with their unique SM device ID and can be customized with additional keys/values from there.
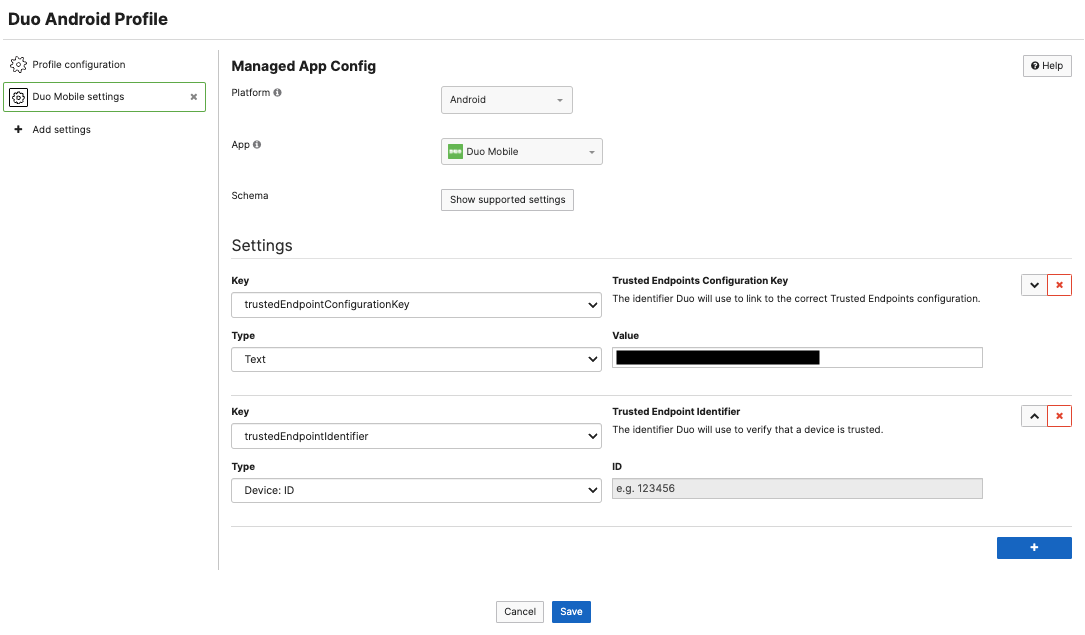
iOS/iPadOS
Meraki Systems Manager can configure Duo Trusted Endpoint for managed iOS/iPadOS devices. Deploy the Duo application with Systems Manager and then use a Managed App Config to configure the desired Duo app settings. trustedEndpointConfigurationKey is necessary to configure your exact trusted endpoint access on the managed devices. trustedEndpointIdentifier set as the Device: ID is useful to track devices with their unique SM device ID and can be customized with additional keys/values from there. 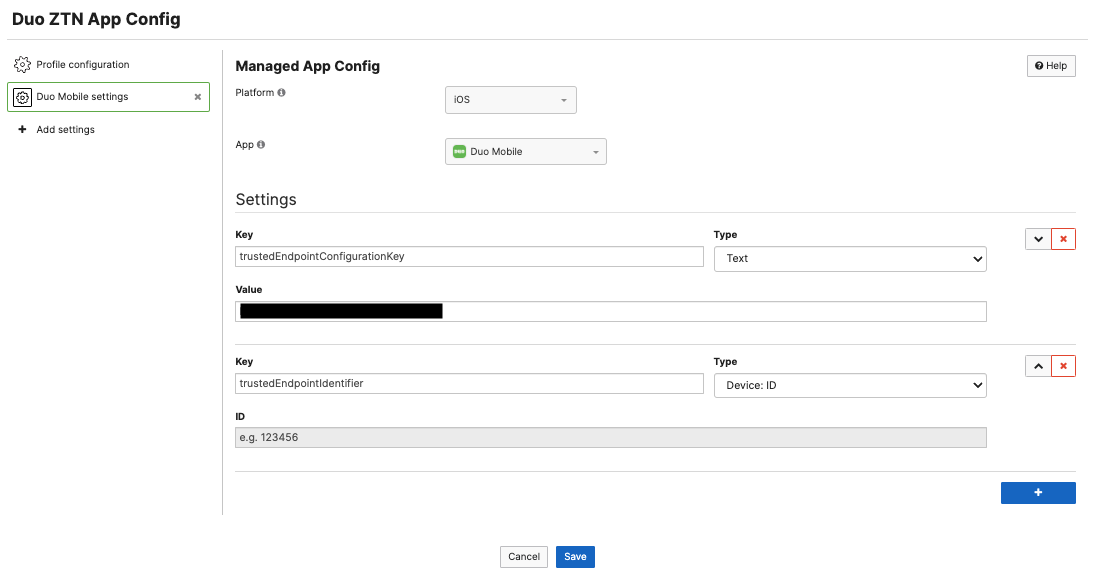
macOS
On macOS, Meraki Systems Manager can install the Duo Device Health Application (DHA). This can be deployed as a custom app in the SM > Apps page. For more information on to deploy Duo Device Health Agent via SM, see the Duo documention.
Windows
On Windows, Meraki Systems Manager can install the Duo Device Health Application (DHA). This can be deployed as a custom app in the SM > Apps page. For more information on to deploy Duo Device Health Agent via SM, see the Duo documention.
ThousandEyes

Meraki Systems Manager can deploy the ThousandEyes agent for additional networking device insights. The ThousandEyes agent is available on macOS and Windows, and the ThousandEyes agent can be deployed on SM enrolled devices as a custom app. It is also available as an extension on Google Chrome. Below are some of the recommended steps for each platform:
macOS
The macOS ThousandEyes agent can be deployed as a custom app via Systems Manager.
For more information on configurations, please review the Thousand Eyes macOS documentation.
Windows
The Windows ThousandEyes agent can be deployed as a custom app via Systems Manager.
For more information on configurations, please review the ThousandEyes Windows documentation.
Google Chrome Extension
A Google Chrome ThousandEyes extension can be deployed via Systems Manager. For more information on configurations, please review the Thousand Eyes Chrome Extension documentation. For more information on
Cisco ISE

Device posture for Wi-Fi and VPN. For more information on configuring Cisco ISE with Meraki, please see: MR Device Posturing with Cisco ISE or Central Web Authentication with Cisco ISE.

